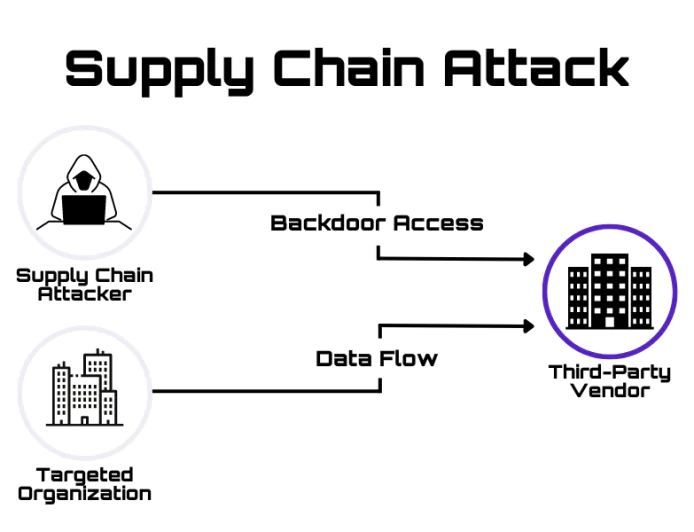
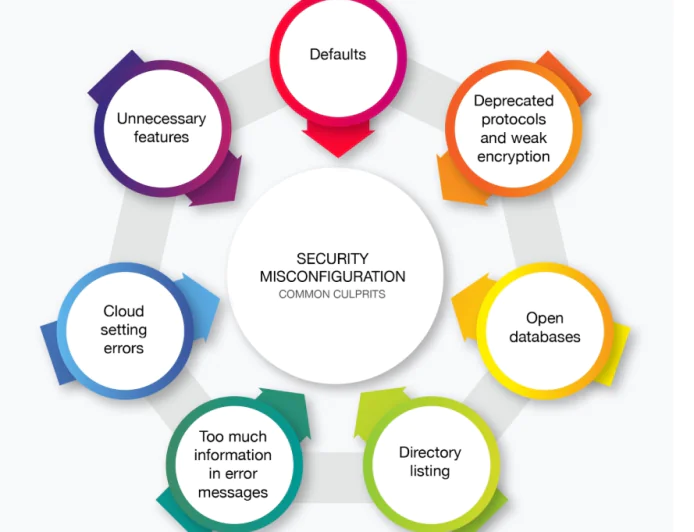
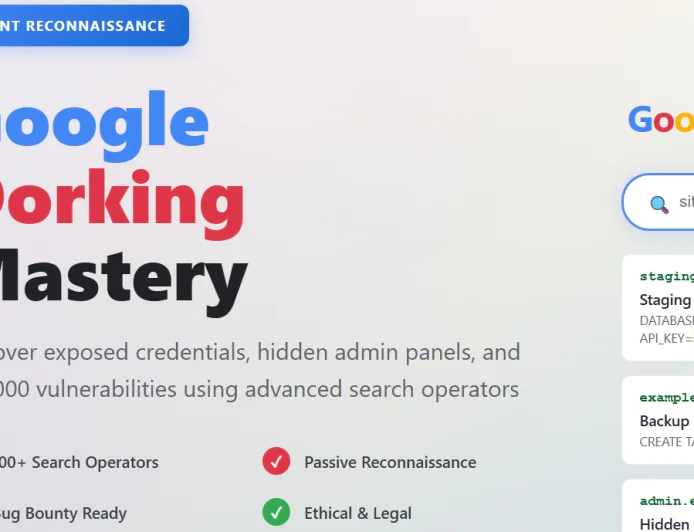
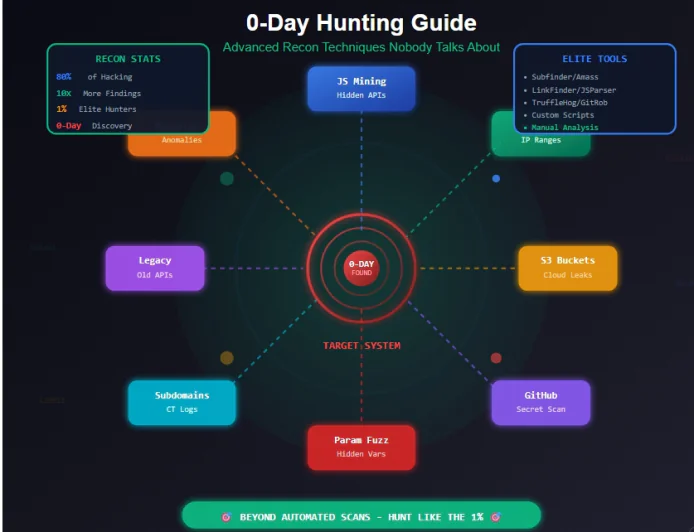
CyberSecurity News
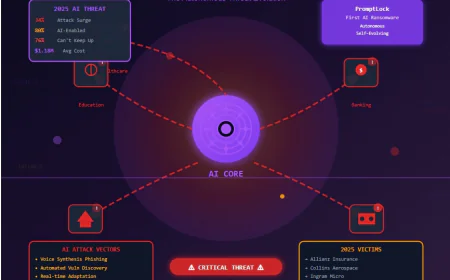
North Korea-Linked Hackers Steal $2.02 Billion in 2025, Leading Global Crypto Theft
Shivi_k Dec 22, 2025
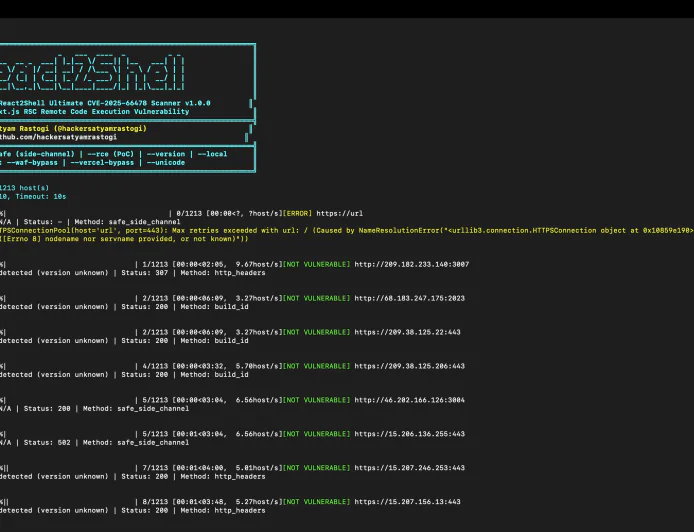
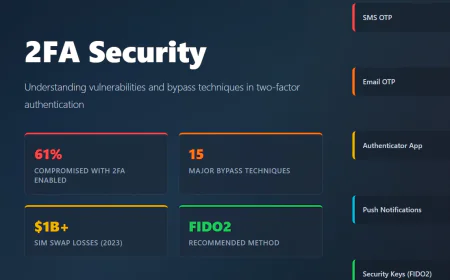
OSINT
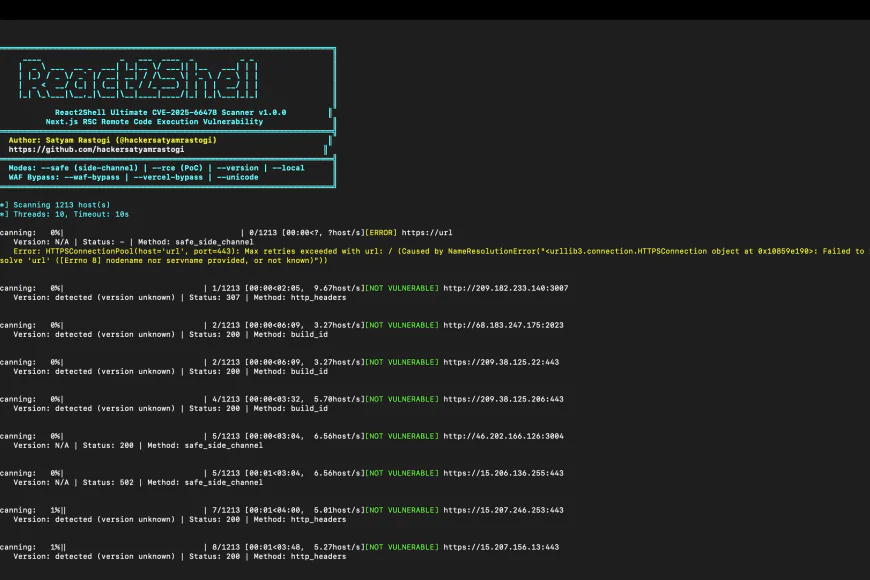
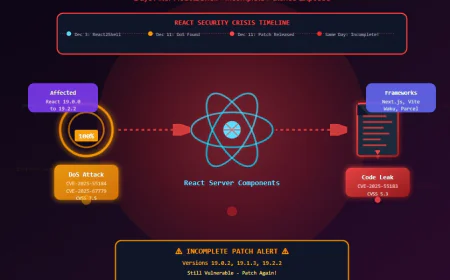
React2Shell Ultimate - The First Autonomous Scanner for Next.js RSC RCE (CVE-2025-66478)
Jack Barlow Dec 6, 2025

Compliance
The DPDP Act, 2023: India's New Era of Data Privacy and Cybersecurity
Shivi_k Sep 30, 2025