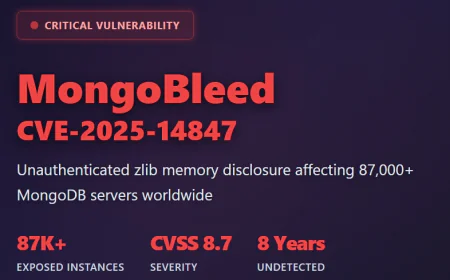
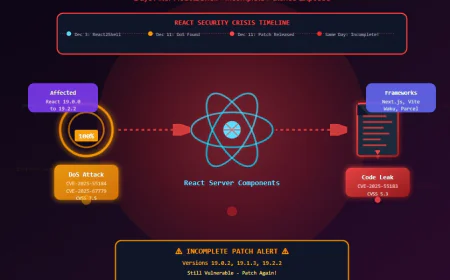
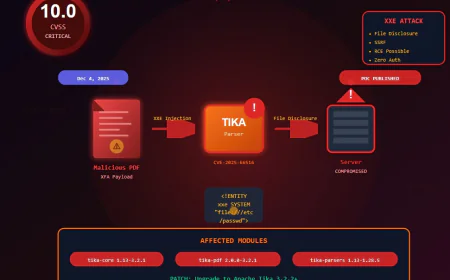
Spoofing Attacks Explained - Types, Risks, and How to Stop Them
Spoofing attacks involve attackers impersonating trusted sources across email, phone, DNS, and other systems to steal data or commit fraud. Defense requires a multi-layered approach combining email authentication protocols (DMARC, DKIM, SPF), AI-based threat detection, user training, and solutions from vendors like Proofpoint and Microsoft.

Introduction
The evolution of technology and the transition to digital communication have forced attackers to up their game and become more sophisticated. Spoofing attacks are one of the most misleading tactics, as they use fake identities to trick victims into revealing their secrets, visiting infected sites, or by mistake letting the intruders into their secure areas or money. It is vital in the cyber threats era to grasp the mechanisms of spoofing, its various forms, and the countermeasures against it.
What Is a Spoofing Attack?
Spoofing attacks are tactics employed by a hacker when he/she tries to deceive a victim by masquerading as a reliable source and thereupon providing false identifying data. When it comes to this level of deceit, the perpetrator may use simple ways such as altering the "From" part of an e-mail header or may pursue a more complex way by deceiving a navigation system through imitating GPS signals. The main goal of the attacker is to produce such believable lies that the target’s guard is significantly lowered giving the attacker a free hand to steal the data, disseminate malware, or conduct fraud.
Spoofing, in the end, is a battle pitting the attacker against the internet protocols and the victim’s trust. A considerable number of the primary protocols that form the basis of email, telephone, DNS, and IP networking systems were created with the intention of being functional rather than secure and thus it is quite easy for hackers to alter these identifiers.
Conventional spoofing assaults move through stages:
Reconnaissance: The attackers collect the informations of the target.
Preparation: Fake addresses, domains or technological arrangements are made.
Execution: Sending of misleading messages or making of connections with the targets.
Exploitation: The attackers obtain their objectives like stealing data or compromising the system.
The cycle is frequently characterized by the use of multi-channel campaigns that combine technical spoofing and social engineering to increase the impact even more.
Types of Spoofing Attacks
Spoofing attacks come in various forms, each exploiting different systems and protocols:
Email Spoofing
Email spoofing is indeed one of the most prevalent and most concerning forms of cybercrime. The criminals pretend to be someone else when they are sending an email and that way the emails look like they are coming from trustworthy individuals or companies. This method takes advantage of the Simple Mail Transfer Protocol (SMTP), which does not verify the sender's identity as a matter of course. Current research indicates that only about one-third of the top domains (35%) are fully compliant with the email authentication regulations, which leaves a lot of organizations without protection.
Spoofed emails are very likely to have phishing links or virus-laden attachments, and they may cause usage of false urgency or even authority (e.g. an impersonator of a CEO asking for fund transfers). The tactics of advanced spoofing consist of using similar-looking domain names or taking over of the server to get around the filters.
Caller ID Spoofing
This particular technique is able to make a phone call look like it’s coming from a reliable number and by using social engineering, it can manipulate the victims to give away such sensitive information which includes passwords, bank details, or personal identifiers. A few of the voice spoofing methods at present have already started utilizing AI to produce very realistic imitations of voices, thereby, rendering the detection of scams even harder.
Website Spoofing
Cybercriminals set up fake websites that are similar to the genuine ones to get usernames and passwords or to put virus into the victims' computers. They usually do this by registering domain names that are very close to the authentic ones but with small misspellings. Users can input private information thinking that the site is real
IP Spoofing
By changing the source IP address in the data packets, the attackers are able to conceal their actual location or to impersonate the trusted devices. This technique is the root cause of many massive Distributed Denial-of-Service (DDoS) attacks that target and overwhelm, as well as methods to bypass IP-based access controls.
ARP Spoofing
This attack is aimed at local networks and is executed by sending misleading Address Resolution Protocol messages that connect the hacker’s MAC address to the IP address of a legal device, which allows intercepting or altering the data (man-in-the-middle). It aids in stealing credentials, hijacking sessions, and moving laterally within the networks.
DNS Spoofing (Cache Poisoning)
This is an act of altering DNS entries so as to reroute traffic from genuine domains to the ones created by attackers. Attackers take advantage of the absence of response authentication in DNS to insert bogus records. The victims may find themselves inadvertently redirected to phishing or malware distribution sites.
GPS Spoofing
By implanting phony GPS signals, the attackers can control the location data that devices are receiving. Such situations are of high concern especially with the navigation systems that are used in aviation, maritime, or vehicles tracking, as they could potentially lead to disastrous misrouting.
SMS/Text Spoofing
Just like voice caller ID spoofing, scammers send text messages with forged sender information. These messages are usually part of smishing campaigns and contain malicious links or personal data requests.
Risks Associated With Spoofing Attacks
The effects of spoofing attacks are diverse:
Data Breaches: Unauthorised individuals gaining access to sensitive information.
Financial Loss: Money lost through unauthorised transactions or scams.
Malware Propagation: Spoofed messages may serve as channels for spreading viruses, ransomware, or spyware.
Operational Disruptions: DDoS or man-in-the-middle support spoofing attacks causing disconnection or unavailability of the network or service.
Reputational Harm: Companies that suffer from spoofing might not only lose customer trust but also legal liabilities.
With the rise of AI that can produce near-perfect impersonations, the threats are now more serious and extensive than ever.
How to Detect Spoofing Attacks

Detection involves both alerting user behavior and implementing technical measures:
-
Inspect unexpected emails or phone calls for discrepancies (typographical errors, odd requests).
-
Be very careful in checking the email addresses of the senders, not just the names that are displayed.
-
Do not click on unknown links; check the URLs.
-
Make use of network monitoring tools that can identify abnormal ARP or DNS activities.
-
Apply domain authentication methods such as SPF, DKIM, and DMARC to ensure emails are legitimate.
-
Utilize caller ID verification tools and text message filtering systems.
-
Conduct user education sessions frequently to help them recognize social engineering strategies and spoofing signs
Best Practices for Prevention
The most effective defense against spoofing is having an all-around approach that consists of technology, policies, and user education:
-
Implement strong email authentication protocols (DMARC, DKIM, SPF) and make sure they are widely adopted.
-
Invest in AI-based software for detecting phishing and fraud that would not only analyze but also recognize patterns of messages by their metadata and behavior.
-
Make cybersecurity training a regular practice throughout the organization as a means of building awareness.
-
Network security techniques should be employed such as firewalls, intrusion detection/prevention systems, and encrypted communication protocols.
-
Introduce multi-factor authentication to minimize the consequences of username/password abuse.
-
Conduct regular updates of systems and software in order to eliminate known security loopholes.
-
Utilize risk-based authentication and behavioral biometrics for the sophisticated user verification process.
Companies Protecting Against Spoofing Attacks
|
Company |
Speciality Area |
Key Features |
|
IntelligenceX |
Threat Intelligence & Security |
Dark web Monitoring, leak detection , real-time anomaly detection |
|
Proofpoint |
Email Security & Threat Protection |
Anti phishing, BEC,protection , DMARC enforcement |
|
Microsoft |
Cloud Security & Email Defense |
Defence for office 365, brand impersonate protection |
|
Mimecast |
Email Security & Awareness Training |
AI threat detection, brand impersonation protection |
|
Barracuda Networks |
Phishing & Spoofing Protection |
AI filtering, phishing defence , domain spoofing prevention |
|
IronScales |
Email Threat Defence |
Maching learning detection, automated incident response |
|
Valimail |
Email Authentication & Fraud Prevention |
Cloud-native DMARC enforcement, fraud detection |
|
ZeroFox |
Digital Risk & Brand Protection |
Social media monitoring, impersonation takedown |
|
Arkose |
Anti Fraud & User Verification |
Behavioral biometrics, risk-based verification |
Conclusion
As digital communication becomes the norm, spoofing attacks are still regarded as a major threat since they take advantage of the weaknesses that are both technical and human by nature. Spoofing can be done using various methods, from simple gumming up the works of communication channels to calling and sending emails impersonating someone else. The consequence of these actions can be the loss of money, the draining of bank accounts, and the interruption of service.
It is fundamentally necessary to comprehend the various sorts of spoofing attacks, the dangers associated with them, and to use multi-layered detection and prevention methodologies to keep the cybersecurity of the entire organization or personal space. The firms like IntelligenceX, Proofpoint, Microsoft, and others have already come up with progressive and adaptive technologies that can detect and then neutralize these threats before they cause any harm. The combination of tech protection, stringent practices, and ongoing awareness campaigns makes up the backbone of an organization’s defense against spoofing attacks.
The goal of this detailed and wide-ranging portrayal is mainly to inform the readers indicating them how to spot spoofing attacks, what the risks are, and to suggest the use of best practices and solutions to keep their digital lives safe from this widespread cyber menace.