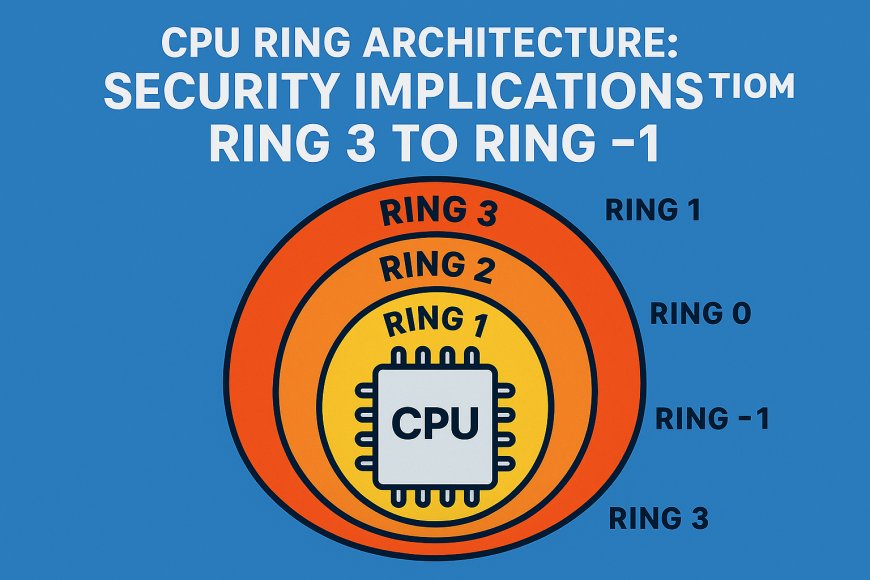
CPU Ring Architecture: Security Implications from Ring 3 to Ring -1
Explore the fundamental security architecture of modern CPUs through user mode, kernel mode, and hypervisor mode. Learn how attackers exploit privilege boundaries, understand real-world vulnerabilities, and discover practical security implications with hands-on examples and code demonstrations.
Ever wondered why a crashed browser doesn't bring down your entire computer? Or how malware attempts privilege escalation attacks? The answer lies in CPU privilege levels - a fundamental security architecture that separates user applications from critical system operations.
What are CPU privilege levels?
When you're browsing the web, editing documents, or playing games, your applications are running in a carefully controlled environment that prevents them from accessing critical system resources directly. This isn't just good software design—it's a hardware-enforced security mechanism built into every modern processor.
CPU privilege levels , also known as protection rings or privilege rings, are hardware-enforced boundaries that control what code can and cannot do on your system.To protect user applications from accessing and/or modifying critical OS data, Windows uses two processor access modes (even if the processor on which Windows is running supports more than two): user mode and kernel mode. User application code runs in user mode, whereas OS code (such as system services and device drivers) runs in kernel mode. Kernel mode refers to a mode of execution in a processor that grants access to all system memory and all CPU instructions.
Architecture Overview
A simplified version of this architecture is shown in Figure 2-1. Keep in mind that this diagram is basic. It doesn’t show everything. For example, the networking components and the various types of device driver layering are not shown.
Image source: Windows Internals by Mark Russinovich, David Solomon, and Alex Ionescu - Microsoft Press
- User Mode:
• Runs applications like browsers or editors
• Has limited access to memory and CPU instructions
• Can't directly interact with hardware or kernel memory
• If it crashes, only the app fails, not the OS
- Kernel Mode:
• Executes core OS functions, drivers, and services
• Has full access to all memory and hardware
• Can execute privileged CPU instructions
• A crash here can cause system-wide failure (BSOD)
Some processors differentiate between such modes by using the term code privilege level or ring level, while others use terms such as supervisor mode and application mode. Regardless of what it’s called, by providing the operating system kernel with a higher privilege level than user mode applications have, the processor provides a necessary foundation for OS designers to ensure that a misbehaving application can’t disrupt the stability of the system as a whole.
Note: The architectures of the x86 and x64 processors define four privilege levels (or rings) to protect system code and data from being overwritten either inadvertently or maliciously by code of lesser privilege.
CPU Privilege Levels (Rings) in x86/x64 vs Windows Usage
- x86/x64 CPUs define 4 privilege levels (Rings 0–3):
• Ring 0: Highest privilege — full access (used for kernel/OS)
• Ring 1–2: Mid-level (rarely used in modern OSes)
• Ring 3: Lowest privilege — restricted access (used for user apps)
- Windows only uses Ring 0 and Ring 3:
• Ring 0 → Kernel Mode
• Ring 3 → User Mode
- Why skip Rings 1–2?
• Other architectures (e.g., ARM, MIPS, Alpha) only support 2 privilege levels
• Using just two levels ensures cross-platform portability
• Intermediate rings don’t offer clear security boundaries or benefits in practice
- Result:
Windows sticks to a simple and portable model (Ring 0 vs Ring 3), ensuring reliable protection between kernel and user space.
Memory Protection: User Mode vs Kernel Mode
In Windows, even though each process runs with its own isolated virtual memory, the kernel-mode components, like the OS core and device drivers, share a single virtual address space. This design enables performance and system integration but brings high risk — if something goes wrong in kernel mode, it can affect the whole system. Each memory page is tagged to indicate which mode (user or kernel) is required to access it. User-mode pages can be accessed by both user and kernel code, but kernel-mode pages are strictly off-limits to user-mode processes. Additionally, Windows uses read-only pages to protect static data and DEP (Data Execution Prevention) to prevent code execution in non-code memory like heap or stack. This mitigates many exploits such as buffer overflows and shellcode injection. However, once code executes in kernel mode, it bypasses most OS-level protections, making secure driver development and signature enforcement absolutely critical.
Kernel Mode = Full System Access (and Risk)
Once code enters kernel mode, it gains unrestricted access to all system memory, even bypassing built-in security controls. That means any bug or vulnerability in a kernel-mode component (like a driver) can compromise the entire system. This is why Microsoft enforces strong standards for drivers — one bad third-party driver can destabilize or expose the whole OS. Windows has no protection against kernel components misbehaving, which is why testing and validation tools like Driver Verifier exist. This tool can catch issues like memory leaks, race conditions, and buffer overflows that could otherwise turn into kernel-mode vulnerabilities — often prized in privilege escalation exploits.
Kernel Driver Signing & Security (KMCS)
To mitigate malicious or unstable kernel-mode drivers, Microsoft introduced Kernel-Mode Code Signing (KMCS). Since Windows 2000, it required drivers (especially plug-and-play ones) to be signed — optionally enforced. However, on Windows 8.1 x64 and ARM, all drivers must be cryptographically signed by a trusted Certificate Authority. You can’t just load a random driver, even with admin rights — unless you boot into Test Mode, which disables digital rights management and shows a warning watermark.
With Windows 10 (July 2016, version 1607), Microsoft raised the bar again. New drivers must be signed using an EV (Extended Validation) SHA-2 certificate from one of only two accepted authorities. Then, they must be submitted to Microsoft for attestation signing via the SysDev portal, and the result is a driver with a Microsoft signature. Pre-Windows 10 drivers signed with SHA-1 still load (for now), but that’s changing too.
Windows Server 2016: WHQL Enforcement
On Windows Server 2016, the requirements are even stricter. Drivers not only need KMCS but must also pass Windows Hardware Quality Labs (WHQL) testing and be submitted via the Hardware Compatibility Kit (HCK). Only WHQL-signed drivers load by default. This helps ensure drivers meet strict performance, stability, and security guidelines. From a hacking perspective, this makes kernel exploitation harder on servers, since you can't just load unsigned or poorly-written kernel code.
Enterprises can customize these protections using Device Guard or other policies. For instance, a company could enforce WHQL signing even on regular Windows 10 workstations, or loosen it on a specific server. Hackers often target misconfigured systems where these policies are disabled or relaxed. Knowing how to identify unsigned drivers, test mode, or policy overrides is critical when assessing privilege escalation potential.
Switching Between User Mode and Kernel Mode
Here is the intresting part, Every time a user application performs an operation that needs OS-level functionality — like reading a file — it calls a system service (like ReadFile), which transitions the processor from user mode to kernel mode. This is not a full context switch but a mode switch, typically triggered by a specific instruction like syscall or int 2e. The call lands in Windows’ system service dispatching layer, which routes it to the correct internal function in Ntoskrnl.exe or Win32k.sys. After the OS completes the operation, control is returned to user mode.
Interestingly, GUI-based applications often spend more time in kernel mode. Why? Because Windows' graphics subsystem (GDI, Direct2D, etc.) operates largely in the kernel to improve performance. So when you open something like Paint or Photoshop, a lot of that rendering logic runs as privileged code. However, newer APIs like DirectComposition try to reduce kernel transitions by doing more work in user mode, sending only final image data to the GPU kernel driver.
Terms like Ntoskrnl.exe or Win32k.sys may sound heavy for beginners, but with future analysis, we can understand them better and in an easier way.
TABLE 1-1 Mode-related performance counters
EXPERIMENT: Kernel mode vs. user mode
1. You can use the Performance Monitor to see how much time your system spends executing in kernel mode versus in user mode. Follow these steps: Open the Start menu and type Run Performance Monitor (it should be suggested before you finish typing) to run Performance Monitor.
2. Select the Performance Monitor node under Performance/Monitoring Tools in the tree on the left side.
3. To delete the default counter showing the total CPU time, click the Delete button on the toolbar or press the Suppr key on the keyboard.
4. Click the Add (+) button on the toolbar.
5. Expand the Processor counter section, click the % Privileged Time counter, and, while holding down the Ctrl key, click the % User Time counter.
1. Click Add, and then click OK.
2. Open a command prompt and type the below command to run a directory scan of your C drive
dir \\%computername%\c$ /s
That graph is now showing:
- Red line:
% Privileged Time→ this is Kernel Mode CPU usage - Green line (probably):
% User Time→ this is User Mode CPU usage
When you run a command like:
dir \\%computername%\c$ /sYou're triggering:
- A file system traversal (
/s= recursive) - Across the ADMIN$ share (which is a protected system share)
- Involving NTFS driver, SMB stack, I/O calls
All of these are handled in Kernel Mode (Privileged Time), so you’ll see red line spikes during this operation.
Meanwhile, User Mode handles user-space applications (e.g., File Explorer, PowerShell UI), and you’ll see less activity there for system-level tasks.
You can also quickly see this by using Task Manager. Just click the Performance tab, right click the CPU graph, and select Show Kernel Times. The CPU usage bar will show kernel-mode CPU time usage in a darker shade of light blue.
To see how the Performance Monitor itself uses kernel time and user time, run it again, but add the individual process counters % User Time and % Privileged Time for every process in the system:
- If it’s not already running, run the Performance Monitor again. (If it is already running, start with a blank display by right-clicking in the graph area and selecting Remove All Counters.)
- Click the Add button on the toolbar.
- In the available counters area, expand the Process section.
- Select the % Privileged Time and % User Time counters.
- Select a few processes in the Instance box (such as mmc, csrss, and Idle).
- Click Add, and then click OK.
- Move the mouse rapidly back and forth.
- Press Ctrl+H to turn on highlighting mode. This highlights the currently selected counter in black.
- Scroll through the counters at the bottom of the display to identify the processes whose threads were running when you moved the mouse, and note whether they were running in user mode or kernel mode.
When you move the mouse, you should see the kernel-mode and user-mode time increase in the Instance column of the mmc process in the Process Monitor. This is because the process is executing application code in user mode and calling Windows functions that run in kernel mode. You’ll also notice kernel-mode thread activity in a process named csrss when you move the mouse. This activity occurs because the Windows subsystem’s kernel-mode raw input thread, which handles keyboard and mouse input, is attached to this process. (See Chapter 2 for more information about system threads and subsystems.) Finally, the Idle process that you see spending nearly 100 percent of its time in kernel mode isn’t really a process—it’s a fake process used to account for idle CPU cycles. As you can observe from the mode in which the threads in the Idle process run, when Windows has nothing to do, it does it in kernel mode.
Hypervisor
Whether to allow for hosting multiple tenants on a server farm and run 100 isolated websites on a single server or to permit developers to test dozens of different OS varieties without buying dedicated hardware. The need for fast, efficient, and secure virtualization has driven new models of computing and reasoning about software.
In fact, today, certain software—such as Docker, which is supported in Windows 10 and Server 2016—runs in containers, which provide fully isolated virtual machines solely designed for running a single application stack or framework, pushing the boundaries of a guest/host even further. To provide such virtualization services, almost all modern solutions employ the use of a hypervisor
A hypervisor is a piece of software (or firmware) that creates and manages virtual machines (VMs). It runs at a higher privilege level than the traditional operating system (even higher than ring 0 or kernel mode), and it isolates hardware resources (CPU, memory, I/O) among different guest operating systems.
Hyper-V is an example of such a hypervisor, which powers the Hyper-V client functionality exposed in Windows 8.1 and later. Competing products such as Xen, KVM, VMware, and VirtualBox all implement their own hypervisors, each with their own strengths and weaknesses.
Any hypervisor that runs at the hardware level can exert control over the kernel (Ring 0) of guest operating system.
Privilege Hierarchy (Applies to ALL Hypervisors)
| Privilege Level | Description | Applies to |
|---|---|---|
| Ring -1 | Hypervisor mode | Hyper-V, Xen, KVM, VMware, VirtualBox |
| Ring 0 | Kernel mode | Windows kernel, Linux kernel |
| Ring 3 | User mode | Apps like Firefox, VSCode, bash |
kernel is the core of the operating system, acting as the "heart" that manages system resources, hardware communication, memory, processes, and security. However, the statement about the hypervisor having "access even greater than the kernel itself" refers to a deeper architectural hierarchy in modern systems with virtualization.
1. Hypervisor Runs at a Higher Privilege Level Than the Kernel
- On x86/x64 CPUs, privilege levels are enforced by hardware (ring levels: Ring 0 = kernel, Ring 3 = user apps).
- A Type-1 hypervisor (like Hyper-V) operates at an even more privileged level called Ring -1 (or "root mode" in Intel VT-x / AMD-V). This is below the OS kernel (Ring 0).
- The hypervisor controls physical hardware directly and can virtualize the kernel itself. This means it can:
- Isolate the kernel from bare-metal hardware.
- Intercept/modify kernel operations (e.g., memory access, CPU instructions).
- Enforce policies that even the kernel cannot bypass.
2. Kernel vs. Hypervisor Privileges
- The kernel manages the OS and hardware, but it trusts its own code (and drivers). If the kernel is compromised (e.g., by a rootkit), all security fails.
- The hypervisor can monitor or restrict the kernel itself. For example:
- Memory Isolation: VBS uses "Virtual Secure Mode" to shield security-critical processes (like Credential Guard) from the kernel.
- Code Integrity: Hypervisor-enforced Kernel Code Integrity (HVCI) prevents unauthorized kernel modifications, even if an attacker gains kernel privileges.
- Hardware-Based Security: The hypervisor can enforce DMA protection (via IOMMU) to stop malicious hardware from accessing memory.
3. Why This Matters in Windows 10/11 (VBS)
- Virtualization-Based Security (VBS) uses Hyper-V to create isolated regions of memory ("secure worlds") where security services run outside the kernel's influence.
- Even if the kernel is hacked, VBS protections (like Device Guard, Credential Guard) remain intact because the hypervisor enforces their isolation.
- This is why Microsoft says the hypervisor offers "assurances beyond what the kernel provides"—it’s a higher authority.
In Windows 10, Microsoft now leverages the Hyper-V hypervisor to provide a new set of services known as virtualization-based security (VBS):
■ Device Guard This provides Hypervisor Code Integrity (HVCI) for stronger code-signing guarantees over KMCS alone, and allows for the customization of the signature policy of the Windows OS, for both user-mode and kernel-mode code.
■ Hyper Guard This protects key kernel-related and hypervisor-related data structures and code.
■ Credential Guard This prevents unauthorized access to domain account credentials and secrets, combined with secure biometrics.
■ Application Guard This provides an even stronger sandbox for the Microsoft Edge browser.
■ Host Guardian and Shielded Fabric These leverage a virtual TPM (v-TPM) to protect a virtual machine from the infrastructure it’s running on.
Now, let’s take a deeper look at the inner workings of Virtualization-Based Security (VBS) architecture.
Virtualization-based security architecture
Traditionally, Windows enforces a privilege separation model using:
- User Mode: Ring 3 — where apps run (e.g., browsers, games).
- Kernel Mode: Ring 0 — where core OS components, drivers, and system-level code run.
This separation protects the OS from user-level attacks.
However, if malicious code gets into kernel mode, it can bypass all protections because:
- Kernel mode has unrestricted access to memory, devices, and hardware resources.
If the attacker installs a malicious driver or exploits a kernel vuln , the system is essentially compromised because all kernel-mode code has complete access to the entire system.
Introducing VTLs (Virtual Trust Levels)
VTLs provide an additional layer of isolation — orthogonal to user vs kernel mode.
Beyond simply introducing a new orthogonal way of isolating access to memory, hardware, and processor resources, VTLs also require new code and components to manage the higher levels of trust. The regular kernel and drivers, running in VTL 0, cannot be permitted to control and define VTL 1 resources; this would defeat the purpose.
VTL 0 (Left side):
- User Mode: Where your regular applications run (browsers, games, Office, etc.)
- Kernel Mode: The standard Windows kernel that manages system resources, drivers, and system calls
VTL 1 (Right side):
- Isolated User Mode (IUM): A special secure environment for running security-sensitive code
- Secure Kernel: A minimal, hardened kernel that protects critical security functions
Hyper-V Hypervisor (Middle):
- Acts as the foundation layer that enforces isolation between VTL 0 and VTL 1
- Manages memory access and ensures VTL 0 cannot tamper with VTL 1
Hardware Layer (Bottom):
- SLAT: Second Level Address Translation - hardware feature that helps with memory virtualization
- I/O MMU: Input/Output Memory Management Unit - protects against DMA attacks
- These hardware features are essential for VBS to work securely
The hypervisor creates a security boundary where even if malware compromises the regular Windows kernel (VTL 0), it cannot access or modify the secure components running in VTL 1. This protects features like:
- Windows Defender credential protection
- Device Guard code integrity policies
- Secure boot measurements
Thus, even if kernel-mode code is compromised in VTL 0, it cannot touch or tamper with VTL 1.
With Windows 10 version 1607 and Server 2016 releases, it’s always active by default if supported by hardware. For older versions of Windows 10, you can activate it by using a policy or with the Add Windows Features dialog box (select the Isolated User Mode option).
At this point, it’s important to understand how this security model actually works under the hood.
Secure Kernel Implementation
The entire system starts with the hypervisor, which launches before the Windows kernel during the boot process. This early initialization gives the hypervisor complete control over system hardware and memory management.
The hypervisor creates two isolated Virtual Trust Levels: VTL 0 contains the normal Windows environment, while VTL 1 contains the secure execution environment. These are not just software divisions but hardware-enforced separations that prevent code in one VTL from accessing resources in the other.
The Two Worlds and Their Purpose
VTL 0 contains the standard Windows operating environment including all user applications, system services, and the regular Windows kernel. This environment operates with normal Windows functionality and security boundaries.
VTL 1 operates as a highly restricted, secure execution environment designed exclusively for critical security functions. The key architectural principle is that VTL 1 provides isolation rather than additional power. Code running in VTL 1 cannot be accessed or modified by code in VTL 0, even if VTL 0 is completely compromised by malware.
The Secure Kernel: The Guardian of the Inner Keep
The secure kernel operates within VTL 1 as a separate binary file called securekernel.exe. Unlike the regular Windows kernel, the secure kernel implements only a minimal set of system capabilities. It functions as a proxy kernel, selectively filtering which system calls from VTL 1 applications can be forwarded to the VTL 0 kernel.
This filtering mechanism is highly restrictive. The secure kernel blocks all I/O operations including file system access, network communication, and registry operations. Graphics operations are completely unavailable, and VTL 1 applications cannot communicate with any device drivers. This creates a severely limited execution environment focused purely on secure computation rather than general system functionality.
Memory Protection: The Physical Barriers
The VTL isolation is enforced through hardware-level memory protection mechanisms. The secure kernel uses Second Level Address Translation (SLAT) to control memory access permissions. SLAT allows the secure kernel to designate specific memory regions as accessible only to VTL 1, creating hardware-enforced memory barriers that VTL 0 cannot breach.
The I/O Memory Management Unit (MMU) provides additional protection by virtualizing memory access for hardware devices. This prevents malicious device drivers from using Direct Memory Access (DMA) to bypass SLAT protections and directly access secure memory regions. The I/O MMU ensures that even hardware-level memory access attempts are controlled and filtered through the virtualization layer.
The Boot Process: Establishing the Fortress
The entire security model depends on establishing these protections before any potentially malicious code can run. Here's how the boot process creates this secure foundation:
- Hypervisor First: The boot loader starts the hypervisor before anything else, giving it complete control over the system hardware.
- Hardware Configuration: The hypervisor immediately configures SLAT and I/O MMU to create the memory barriers and hardware protections.
- VTL 1 Initialization: The boot loader runs again, this time in VTL 1, to start the secure kernel. The secure kernel can now further configure security settings from its privileged position.
- VTL 0 Jail: Only after the secure fortress is fully established does the system start the regular Windows kernel in VTL 0. By this point, VTL 0 is essentially running in a "jail" - it can operate normally but cannot escape to access VTL 1 resources.
This sequence is crucial because it ensures the security barriers are in place before any potentially vulnerable code starts running.
IUM: The Controlled Environment
Within VTL 1, there's another layer called Isolated User Mode (IUM). If VTL 1 is the inner keep, then IUM is like a specially controlled workshop within that keep. IUM serves two connected purposes:
First, it restricts what user-mode applications can do in VTL 1. Just as the secure kernel limits what system calls can be made, IUM limits which DLLs can be loaded and what functions they can access.
Second, IUM provides special secure system calls that only work in VTL 1. These are accessed through special libraries: Iumdll.dll (the VTL 1 version of the system's Ntdll.dll) and Iumbase.dll (the VTL 1 version of Kernelbase.dll).
The clever part of IUM's design is that it shares much of the same code as regular Windows, but runs it in this restricted environment. This reduces memory overhead while maintaining security - it's like having the same tools available in your workshop, but with safety locks that prevent dangerous operations.
Copy-on-Write: Preventing Contamination
An important protection mechanism ensures that VTL 0 cannot corrupt VTL 1 binaries. Through copy-on-write mechanisms, if any VTL 0 process tries to modify a binary that VTL 1 uses, the system creates a separate copy for VTL 0 instead of allowing the modification. This prevents VTL 0 malware from poisoning VTL 1 resources - it's like having a rule that anything from the outer courtyard that enters the inner keep must be a clean copy, not the potentially contaminated original.
Trustlets: The Exclusive Club
Not just any code can run in VTL 1. Only specially signed binaries called "Trustlets" are allowed. Each Trustlet has a unique identifier and signature that the secure kernel recognizes. The secure kernel has hard-coded knowledge of every legitimate Trustlet that exists.
This creates an exclusive club where membership is tightly controlled. You cannot create new Trustlets without access to Microsoft's secure kernel code, and you cannot modify existing Trustlets without breaking their signatures. This ensures that only Microsoft-approved, security-focused code can execute in the secure environment.
The entire VBS architecture is built around a fundamental principle: privilege levels control power, while VTLs control isolation. A VTL 1 user-mode application is not more powerful than a VTL 0 kernel driver - in fact, it's much less powerful. But it's completely isolated from potential threats in VTL 0.
This is counterintuitive but brilliant. Traditional security tries to give trusted code more power. VBS gives trusted code less power but perfect isolation. It's like moving your most valuable possessions from a heavily armed but exposed location to a simple but impenetrable vault.
The Secure Kernel's Special Position
While VTL 1 applications are restricted, the secure kernel itself occupies a unique position. Running in both VTL 1 and kernel mode, it has complete access to VTL 0 memory and resources. This allows it to monitor and control VTL 0 operations while remaining protected from VTL 0 interference.
The secure kernel can use its privileged position to enforce policies on VTL 0 - like Device Guard's code integrity checks or Credential Guard's secret protection. It's like having a security chief who can observe everything happening in the outer courtyard and intervene when necessary, but cannot be reached or influenced by anyone in that courtyard.
The Correct Boot Sequence
┌──────────────────────────────────────────────────────────────────────────────┐
│ POWER BUTTON PRESSED │
│ - PSU sends Power Good signal to motherboard │
│ - CPU reset vector triggered │
└──────────────────────────────────────────────────────────────────────────────┘
│
▼
┌──────────────────────────────────────────────────────────────────────────────┐
│ FIRMWARE (BIOS / UEFI) │
│ - POST: RAM, CPU, GPU checks │
│ - Enables CPU virtualization extensions (VT-x/AMD-V, SLAT) │
│ - Optionally initializes I/O MMU (VT-d/AMD-Vi) for DMA protection │
│ - Secure Boot: verify bootloader signature │
└──────────────────────────────────────────────────────────────────────────────┘
│
▼
┌──────────────────────────────────────────────────────────────────────────────┐
│ BOOTLOADER (Bootmgr.efi) │
│ - Loads OS loader (winload.efi) │
│ - Hands control to OS loader │
└──────────────────────────────────────────────────────────────────────────────┘
│
▼
┌──────────────────────────────────────────────────────────────────────────────┐
│ OS LOADER (Winload.efi) │
│ - Loads ntoskrnl.exe, HAL, boot drivers │
│ - If VBS/Hyper-V enabled: load hvloader.dll │
│ - Passes control either to Hypervisor or directly to kernel │
└──────────────────────────────────────────────────────────────────────────────┘
│
┌────────┴──────────┐
│ │
▼ ▼
┌─────────────────┐ ┌─────────────────────────────────────────────────────────┐
│ NORMAL BOOT │ │ HYPERVISOR BOOT PATH │
│ (No Hyper-V) │ │ (VBS / Hyper-V Enabled) │
├─────────────────┤ ├─────────────────────────────────────────────────────────┤
│ Kernel starts │ │ Hypervisor starts at Ring -1 │
│ directly │ │ - Configures SLAT for memory translation │
│ (VTL0 only) │ │ - Configures I/O MMU for DMA isolation │
│ │ │ Secure Kernel (VTL1) starts: securekernel.exe │
│ │ │ - Runs Code Integrity, Credential Guard, etc. │
│ │ │ Normal Kernel (VTL0) starts: ntoskrnl.exe │
└─────────────────┘ └─────────────────────────────────────────────────────────┘
│ │
└──────────┬────────┘
▼
┌──────────────────────────────────────────────────────────────────────────────┐
│ KERNEL INITIALIZATION │
│ - Memory manager, scheduler, object manager │
│ - Load Session Manager (smss.exe) │
│ - Start CSRSS, Services, LSASS │
│ - Start Winlogon │
└──────────────────────────────────────────────────────────────────────────────┘
│
▼
┌──────────────────────────────────────────────────────────────────────────────┐
│ USER MODE │
│ - User logon │
│ - Explorer.exe / Desktop │
└──────────────────────────────────────────────────────────────────────────────┘
This is a brief description for Boot Sequence in a more beginer friendly manner.
The Evolving Landscape
As technology continues to advance, we’re witnessing exciting new developments in privilege separation and system security. These innovations go beyond traditional OS protections and are reshaping how trust and isolation are enforced at both the hardware and software level:
-
Hardware Security Modules (HSMs)
These are dedicated physical devices designed to protect sensitive information such as cryptographic keys. By offloading critical operations to an isolated, tamper-resistant module, HSMs add an extra privilege layer that even the operating system cannot easily bypass. -
ARM TrustZone
Modern ARM processors support two worlds: a secure world for sensitive operations and a non-secure world for normal applications. This division ensures that even if the regular OS is compromised, critical security functions running in the secure world remain protected. -
Intel CET (Control-flow Enforcement Technology)
CET adds hardware-level defenses against common exploit techniques like Return-Oriented Programming (ROP). By enforcing strict control-flow integrity, it makes it much harder for attackers to hijack execution flow, effectively raising the bar against memory corruption attacks. -
Confidential Computing
In cloud environments, sensitive workloads can now run inside secure enclaves, where even the cloud provider’s administrators cannot peek into the data. This creates entirely new trust boundaries, allowing organizations to safely process highly confidential information in third-party environments.
Final Thoughts
Every time you click an application icon, submit a web form, or interact with a cloud service, you're participating in a carefully orchestrated dance of privilege levels. Understanding this dance—knowing when and how trust boundaries can be crossed—is what separates good security professionals from great ones.
The hardware-enforced privilege model isn't just about keeping systems stable; it's about creating a foundation of trust that our entire digital world depends on. Whether you're defending against the next zero-day exploit or architecting the next generation of secure systems, these fundamental concepts will serve as your compass.
Remember: in cybersecurity, understanding the rules is the first step to understanding how they can be broken—and more importantly, how to prevent that from happening.