North Korean Hackers Release 197 npm Packages for the Purpose of Distributing the Latest OtterCookie Malware in a Major Operation
North Korean threat actors have launched a large-scale supply-chain attack by publishing 197 malicious npm packages designed to deliver the newly updated OtterCookie malware. The campaign targets developers by mimicking legitimate libraries, stealing authentication cookies, and enabling full account takeover. Security researchers warn that the operation is one of the biggest npm-focused attacks of the year, highlighting the growing risk of compromised open-source ecosystems.

The North Korean hackers have not only increased their cyber activities but also deployed an extensive number of malicious packages via the npm registry that could be seen as the hackers´ gaining not only more but also sophisticated capabilities. The security experts have reported the distribution of 197 more malicious packages that are part of a well-planned Contagious Interview campaign, which has already established itself as one of the most frequent and enduring threats aimed at JavaScript and cryptocurrency development communities.
Scale and Impact of the Campaign
Security company Socket has come up with an estimate of the new malicious packages' belonging that have been downloaded more than 31,000 times, making it a potential risk for thousands of developers and companies. This high download number not only highlights the cleverness of the threat actors' distribution but also the difficulty that the open-source package registries have in detecting and preventing such hidden submissions. The packages are cleverly built to spread the next level OtterCookie malware which, in addition to the features of the previous OtterCookie versions, has incorporated the advanced features of BeaverTail. The merging of these two malware families is an intentional act by the attackers to produce a fatter and more versatile payload that would be capable of executing a whole range of malicious
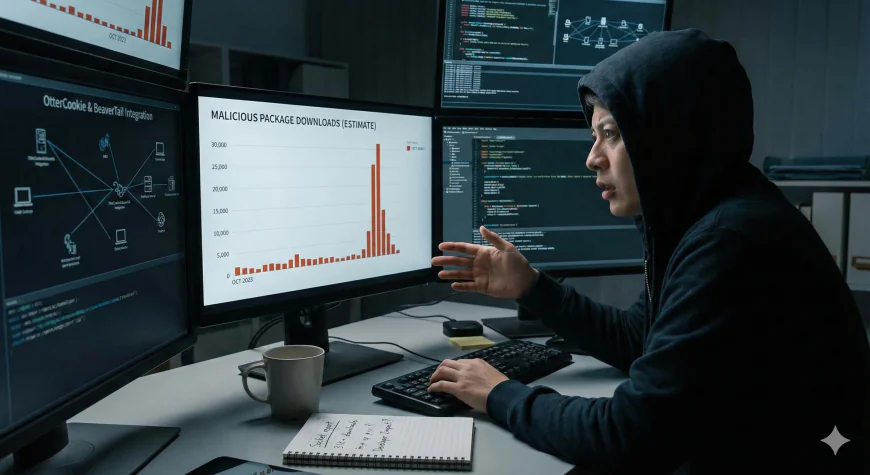
Identified Malicious Packages
Security researchers have pointed out that among the many malicious packages that the npm ecosystem accommodated, some of them were very significant examples that developers might have installed without knowing. The named packages that are misleading are bcryptjs-node, cross-sessions, json-oauth, node-tailwind, react-adparser, session-keeper, tailwind-magic, tailwindcss-forms, and webpack-loadcss. Each of these package names was selected methodically to look like the legit and commonly-used libraries, thereby creating a very reliable cover that would make even casual inspections significantly harder to detect.
The intentional imitation of authentic package names indicates the use of a very skilled social engineering trick that aims to take advantage of the developer's familiarity with popular libraries. By choosing names very similar to the trusted packages, the threat actors are banking on human nature and the typical assumption that packages are legitimate when they are only slightly modified versions of well-known tools.

Advanced Malware Capabilities
The whole plan of the cybercriminals is to get into a target system through the malicious packages that have been installed and executed. The first step is to use the OtterCookie malware that will then spread through the system in several stages with the sole purpose of making the attackers’ remote access and persistence secure. Also, the malware uses sophisticated techniques for detection of sandboxes and virtual machines that help it prevent researchers from analyzing its behavior through the employment of security tools that might be deployed for the purpose of analyzing it. After the successful defeating of the defensive mechanisms, the malware maps the target computer thoroughly, collecting the most detailed information regarding the hardware configuration, operating system and software installed. This reconnoitering stage gives the attackers essential intelligence that they will need to make later attacks more suited and to spot the right targets. A command-and-control channel is then set up by the malware through which the attackers are given the remote shell interface and thus granted the extensive control over the compromised system. The malware carries out not only the execution of basic commands but also implements an extensive toolkit of data-stealing capabilities designed to extract valuable information from infected machines. These capabilities include the theft of clipboard content, keystroke logging, screenshot capturing, browser credential harvesting, document exfiltration, cryptocurrency wallet data theft, and seed phrase collection.

Connection to Previous Campaigns
Last month, Cisco Talos security researchers were able to witness and document the changing characteristics of OtterCookie and BeaverTail malware while they were looking into an infection that had taken over a system linked to a Sri Lanka-based company. The case showed that the attackers had managed to trick a user into running a harmful Node.js program by misrepresenting it as part of a fake job interview, which is a typical method of social engineering called the Contagious Interview campaign.
Technical Infrastructure Analysis
The technical analysis done in detail pointed out that the malicious packages are using a very elaborate multi-staged delivery system. The packages are designed to connect to a hard-coded Vercel URL ("tetrismic.vercel[.]app"), which acts as an intermediate delivery platform. This URL then pulls down the OtterCookie payload for the cross-platform from a repository on GitHub that is controlled by the threat actor.
The GitHub username that was identified as the source of the account hosting and distributing the malicious payloads, stardev0914, has been disabled, probably as a result of a security researcher and platform administrator detection and reporting. Nevertheless, the account's existence and its association with malware distribution are a testament to how cybercriminals are taking advantage of free hosting services to create strong, distributed delivery infrastructures.

Scope and Scale of North Korean Operations
The extraordinary scale of these operations was underlined by security researcher Kirill Boychenko who stated this continuous speed of operations makes Contagious Interview one of the most effective and frequent campaigns that have exploited npm and it demonstrates how completely North Korean threat actors have adapted their toolset to current JavaScript and crypto oriented development workflows. This evaluation presents the inimitable flexibility that these threat actors have shown in their attack on developers and crypto people.
Connected Campaign: ClickFake Interview
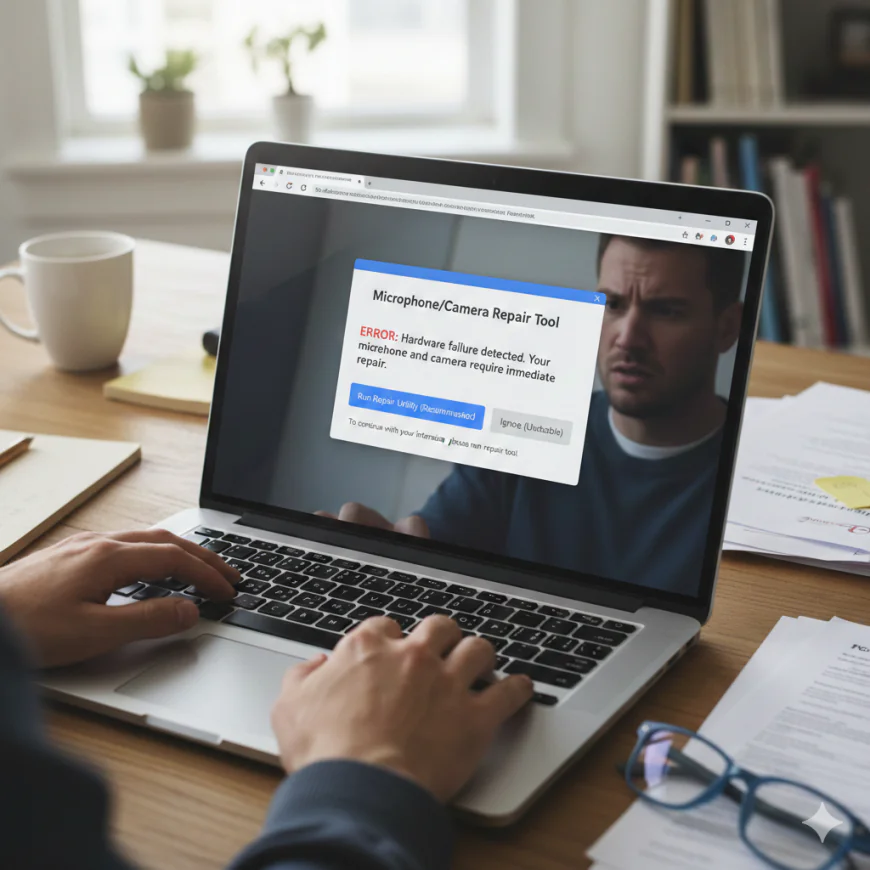
Parallel to the npm based Contagious Interview campaign security researchers have found a corresponding ClickFake Interview campaign which is the name of the operation. The ClickFake Interview campaign uses the same fake websites that the Contagious Interview campaign is using and the two campaigns have ClickFix style social engineering instructions for delivering the malware variant which is called GolangGhost, FlexibleFerret, or WeaselStore. The ClickFake Interview campaign main tactic involves luring the users under the pretext that the camera or microphone are broken and they have to be repaired, thus making the users execute the malware. The malware written in Go programming language GolangGhost is contacting a predetermined command and control server and being placed into a loop which is persistent for command processing that enables collection of system information and file operations such as upload and download execution of commands on an OS level and information gathering from Google Chrome browsers to a great extent. The threat actors carry out the persistence technique by getting a macOS LaunchAgent components installed that will automatically execute the malware through user login by running the shell script right after the user logs in. At the same time they put a bait application which produces the very realistic fake Chrome camera access prompt. Thus trapping the users into the social engineering scenario. The next stage of the attack chain is a Chrome style password prompt that collects user credentials and sends them to Dropbox accounts that are under the control of the attackers.
Distinction from Other North Korean Operations
Validin researchers pointed out that there is an operational overlap with other schemes of the Democratic Peoples Republic of Korea (DPRK) identified technology workers, which target placing people with false identities within the legitimate businesses. However, the Contagious Interview campaign is clearly a different operational approach. This campaign is mainly for the purpose of drawing people in through fake recruitment pipelines, hacking tasks and counterfeit job platforms. Thus turning the job application process into a weapon used against the applicants. Along with being a multi faceted campaign, it is a worrying case of development in tactics used by threat actors, as it reveals their high level grip on developer communities, open source ecosystems, and social engineering methods.












































