Zero Trust Architecture: Stop Assuming, Start Verifying Everything
Explore the essentials of Zero Trust Architecture in this in-depth guide. Learn why organizations must stop assuming trust and start verifying every user, device, and access request. Discover the key principles, practical benefits, and step-by-step strategies for implementing a zero trust security model that reduces cyber risk, supports remote work, and protects sensitive assets in today’s evolving cyber threat landscape.

The traditional network security models are not enough anymore in the present very fast-changing digital world. Groups of people have already got to measure up to the risks coming in from every side namely, hackers from outside, untrustworthy employees, stolen passwords, and very advanced ransomware attacks. Zero trust security has come as the solution to this problem that keeps on growing, which is a modern way of thinking that changes the way organizations understand network security and access control then apply it.
What Is Zero Trust Architecture?
A zero trust architecture is a complete security system that is based on the easy but strong rule of not trusting and Verifying Always. Zero trust thinking implies that no user, device, or application should get trust automatically-in any case, whether they are entering resources from within or outside your network. This way, it differs from the traditional security models, which consider users and devices within the network perimeter as safe.
The introduction of zero trust security is a new and different way of thinking about security. Zero trust does not rely on strong perimeter security, rather it places perimeter security all over the network, through security checkpoints at every access point. An authentication and authorization cycle is required for every user, every device, and every request continuously before being allowed to use the resources. With such a method, one of the major assumptions of security-anyone or anything is trustworthy if on your network- is completely discarded.
The Five Core Principles of Zero Trust

To be able to implement zero trust successfully, it will be necessary to first grasp the basic principles of zero trust that will shape the architecture and the policy decisions.
The zero trust security mantra is never to trust anyone and always verify. This means that authentication is going to be needed all the time for every user and device, no matter where they are located. A person working from home or in the office is going to have to identify himself/herself every time he/she tries to access the network.
Least Privilege Access can be explained as giving users access rights that are only necessary for them to carry out their job functions. By doing so, the principle drastically lowers the attack surface and limits the actions of the intruder to the case where he/she gets a hold of a user's credentials.
Assume Breach works according to the principle that the attackers may have already infiltrated your network. Rather than expecting defenders to thwart every single attack, the zero trust infrastructures assume that breaches will take place and concentrate on limiting the damage through containment and continuous monitoring.
Microsegmentation is the practice of carving up a network into smaller, distinct security areas. Thus, it becomes difficult for the attackers to move around laterally and the security problems are restricted to specific areas instead of being allowed unauthorized access throughout the whole network.
Continuous Monitoring and Verification is the assurance that the zero trust security does not come to a halt once access has been granted initially. The real-time monitoring is going on to the point of tracking user behavior, device health, and access patterns in order to detect any abnormalities and threats throughout a session continuously.
How Zero Trust Architecture Works

The practical implementation of zero trust architecture consists of several interconnected components that are smoothly cooperating with each other.
Identity and Access Management (IAM) systems are the mainstay of zero trust security. The systems authenticate the users' identities and set up tight access controls based on the user's identity, the resources being requested, and the risk level of the request. Multi-factor authentication (MFA) adds another layer of verification, which makes it quite difficult for unauthorized users to obtain access.
In a zero trust model, device verification is of equal importance. The organization has to ensure that every device-laptop, mobile phone, server, IoT device, and printer-follows the security policies that have been laid down before it can connect to the organization's network. Organizations have detailed inventories of endpoint devices that are allowed and consequently deny access to devices that are unknown or not compliant with the organization's security policies.
Network microsegmentation sets up secure zones in your infrastructure. The zero trust architecture does not consider the entire network as a trusted space and instead divides networks into smaller segments with their own security controls. This ensures that attackers cannot move around freely within your systems.
Data encryption secures sensitive information both during transmission and when it is stored. Zero trust security requires that all data transferred over networks be encrypted and that any stored data also be encrypted to prevent unauthorized access.
Continuous monitoring and threat intelligence deliver real-time visibility into the activities happening across your infrastructure. Cutting-edge monitoring tools along with artificial intelligence are used for detecting suspicious activities, attempts of unauthorized access, and potential breaches that might have the capability of doing great damage if they are not caught early.
Zero Trust Architecture vs. Traditional Security Models

The distinctions between zero trust security and traditional security methods are indeed profound and wide-reaching.
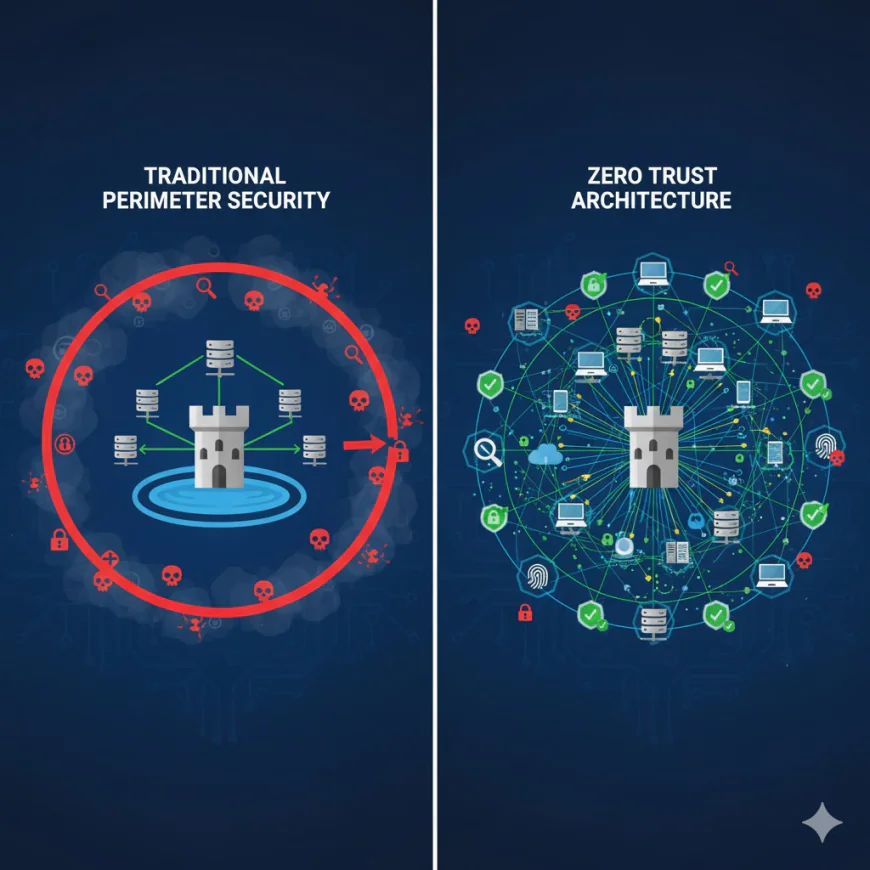
Old-style security systems depend on securing the perimeter-essentially a moat and castle strategy. After getting past the security checks at the network's edge, users and devices are taken to be trustworthy. This presumption leads to hazardous areas where security cannot detect the problems. If attackers take over the perimeter, they can very easily roam inside the network to steal data and plant the malware.
Zero trust enables the organization to see all activities within and around the perimeter as untrustworthy and to operate accordingly. Rather than just letting the internal users in, the zero trust model keeps on verifying every access request, monitoring every session, and limiting every user to just the resources needed. Even if the attackers penetrate your network, they are still confined through microsegmentation, and their activities are constantly tracked.
This basic discrepancy is the reason for zero trust being quite a lot more effective at spoiling breaches and damage limitation. Traditional security systems are really mostly oriented towards preventing external attacks, but they are hardly ever successful against insider threats and compromised passwords. Zero trust security deals with both kinds of threats (external and internal) through its exhaustive verification and monitoring approach.
Key Benefits of Implementing Zero Trust Security

Major security and business benefits are the highlights of organizations applying zero trust architecture.
Limiting the access only to the necessary resources results in a reduced attack surface in the case of organizations. Shifting to least privilege access and micro-segmentation, the possible entry points for attackers are reduced significantly and thus, the attackers find it more difficult to look for and commit their act of taking advantage of the unprotected areas of the system.
The natural outcome of zero trust security is enhanced data protection. Organizations by limiting access to sensitive data, PII the most, and continuously monitoring who accesses what, protect it in a more effective way giving them the advantage of stronger protection over personal information, proprietary knowledge, and financial data.
A major plus for the zero trust architecture comes in the improved visibility of user and network activity. Total logging and continuous monitoring enable the security group to see in detail the flow of access, the possible threats and the dubious activities that possibly cause a breach.
As support for remote work becomes ever more crucial, zero trust security will securely allow access while not dependent on the conventional VPNs. Employees working from home can connect to the resources securely from anywhere, provided that they authenticate on the compliant devices, thus enhancing employee experience and at the same time keeping security intact.
Insider threat mitigation happens only with the adoption of the zero trust security where at the same time the least privileged access and continuous monitoring are enforced. Those employees with good intentions who mistakenly do damage, or the malicious insiders trying to steal data, will find their access control limits and their movements tracked.
Simplified compliance is often an outcome of the zero trust system since the access control, logging and monitoring features that are made available by the framework are often in the same line with the requirements of many industries when it comes to regulations.
Implementation Challenges and Considerations

There is no doubt that the benefits are very attractive but the deployment of zero trust architecture has to be done through meticulous planning and dedication from the whole organization.
An organization should begin by identifying and classifying its critical assets, knowing which systems and data need to be protected the most. It is very important to have a complete mapping of the network including all users, devices, and applications in order to find access routes and apply proper controls.
The practice of zero trust implementation is usually gradual rather than the “big bang” method. Organizations frequently begin with pilot projects to prove the concept in specific departments or business units before going enterprise-wide. This phased approach lessens the impact on operations while at the same time proving the value.
Training for employees and changing the organizational culture are often overlooked but are, in fact, the most important aspects of the whole process. Users may see the zero trust security as a hindrance at first but after receiving the right training, they will be able to appreciate the necessity of the security model and how to operate effectively within it.
Conclusion
Zero trust architecture is the new trend in network security. Zero trust security, the modern framework that actually repels today's threats, provides organizations with a trustworthy solution by getting rid of the old assumption that anyone or anything inside the network is automatically trusted.
In the case of cyberattacks being sophisticated, remote work, cloud computing, and insider threats, organizations have to ditch the traditional precautionary measure of perimeter-based security that creates blind spots. Continuous verification, least privilege access, and microsegmentation-what zero trust security is all about-allow one to embrace the legitimate way of not only reducing risk and containing breaches but also protecting the most important resources.
Rolling out the full zero trust model might consume time, however, the security and business pluses make it an investment that is worthwhile to pursue. Companies that are serious about data protection, customers' and their own reputation should initiate the process of zero trust transformation right away.