Reducing ClickOps with Automated Guardrails -Automated Scripts Replace Manual Console Clicking
In fast-paced cloud environments, every manual click in the console is a potential risk — and that’s where “ClickOps” becomes a silent productivity killer. Teams spend hours managing configurations by hand, increasing the chances of errors and compliance gaps. Automated guardrails flip this story. By enforcing policies, permissions, and best practices automatically, they help engineers move faster without sacrificing control or security. This blog dives into how modern DevOps teams are replacing fragile ClickOps habits with self-service automation and built-in safety nets that keep their cloud clean, compliant, and cost-efficient.

The Problem: “ClickOps” and Its Hidden Cost
We’ve all been there — logging into the AWS console to tweak an IAM policy, open a port “just for testing,” or resize an EC2 instance for a quick fix.
It feels faster in the moment... until something breaks, security teams start asking questions, and nobody remembers what actually changed.
That’s ClickOps — the habit of manually configuring cloud resources through UI clicks instead of version-controlled automation.
While it may seem harmless for small tasks, over time it leads to:
- Inconsistent environments (no two setups are identical)
- No audit trail for what changed, when, and why
- Security blind spots due to forgotten or misconfigured settings
- Burnt-out engineers trying to reproduce “magic” console fixes

The Shift: From Manual Clicks to Automated Guardrails
Modern DevOps teams are realizing that prevention is better than correction.
Instead of trying to stop engineers from using the console, they’re building invisible safety systems — guardrails that automatically enforce good behaviour.
Think of it like this:
- Guardrails don’t stop you from driving — they just make sure you don’t fall off the cliff.
Similarly, automated guardrails allow engineers to move fast, but within safe limits.
These can be built using:
- Policy-as-Code tools like Open Policy Agent (OPA) or HashiCorp Sentinel
- Cloud-native frameworks like AWS Control Tower Guardrails or Azure Policy
- GitOps workflows that automatically validate configurations before deployment
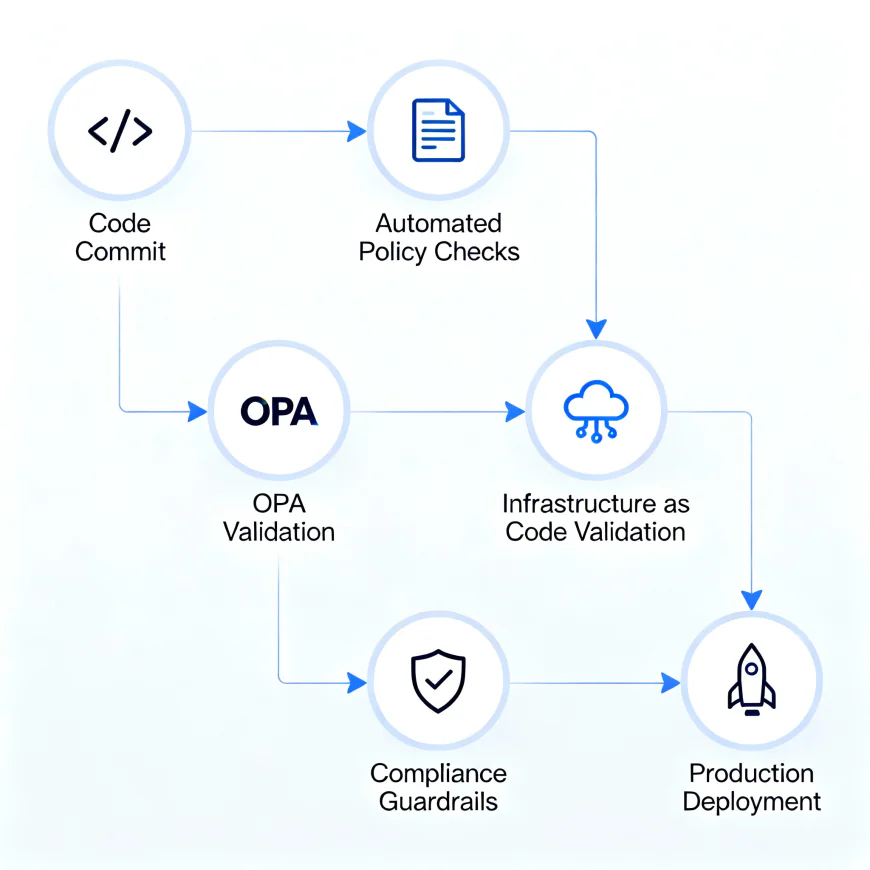
How Automated Guardrails Actually Work
Here’s a simplified flow of how it fits into a real DevOps workflow:
- Developer writes code or Terraform configuration
- Pipeline runs pre-deployment policy checks (e.g., OPA validating no public S3 buckets)
- Guardrail rules automatically block non-compliant changes
- Approved changes get deployed safely
- Continuous monitoring ensures drift is detected and fixed automatically
Instead of policing engineers manually, these rules build trust and reduce friction between Dev, Sec, and Ops teams.
Real-World Examples of Guardrails in Action
Here are a few practical implementations seen across industries:
- AWS: Using Service Control Policies (SCPs) with AWS Organizations to block risky actions (like disabling CloudTrail).
- Kubernetes: Integrating Kyverno or Gatekeeper to enforce pod security standards automatically.
- Terraform: Adding OPA policies in the CI pipeline to prevent hardcoded credentials or unencrypted resources.
- GitOps: Embedding compliance rules directly into pull requests — so policy violations are caught before merging.
Each of these ensures that developers stay empowered, but the system itself remains secure by default.
Benefits Beyond Security
Automated guardrails aren’t just about preventing bad deployments — they transform team culture.
Here’s how:
- Faster onboarding: New engineers don’t need tribal knowledge — the system teaches them what’s allowed.
- Predictable costs: No surprise bills from forgotten over-provisioned instances.
- Better collaboration: Dev and Sec teams stop arguing over permissions — they co-own the same rules.
- Compliance by default: Auditors love automated evidence of policy enforcement.

How to Start Implementing Guardrails
If your team is still dealing with console chaos, here’s a roadmap to start small:
- Audit current ClickOps habits — find where manual changes happen most.
- Adopt IaC everywhere — Terraform, Pulumi, or CloudFormation.
- Add Policy-as-Code tools in your CI/CD pipelines.
- Set up drift detection — tools like AWS Config or Cloud Custodian.
- Educate your team — make automation a shared goal, not a rule.
Remember, automation isn’t about control — it’s about empowering engineers to move faster safely.
Conclusion
Reducing ClickOps isn’t about banning console access — it’s about building a culture of safety and automation.
By embedding guardrails into your DevOps workflows, you’re not just protecting your cloud — you’re freeing your teams from fear, enabling innovation at full speed without losing control.
Because in the end, the best automation isn’t the one that stops you — it’s the one that silently keeps you safe while you move fast.











































