How I Found Multiple Bugs On Dell Technology Using Reconnaissance (OSINT)
A detailed bug bounty write-up on how I discovered multiple vulnerabilities in Dell by leveraging reconnaissance and OSINT techniques. This article explains the methodology, tools, and thought process behind identifying exposed assets, misconfigurations, and sensitive information during recon.

I’m excited to share my journey of how I found multiple security issues in Dell using advanced recon techniques.

Scope:- (*.dell.com ) & (*.delltechnologies.com)
and Any Verified Dell-Controlled Endpoint (domains/IP space/etc.) — No Bounty
Recon doesn’t always mean an asset discovery activity. In this one, it can also mean that we try to learn how the application works, target’s development culture, and more.
- Understand the organization’s infrastructure, what services and technologies it uses, and learn through its documentation.
- Check the organization’s GitHub or GitLab profile to learn more about its infrastructure.
- Check Org subsidiaries
Github Reconnaissance
GitHub is a proprietary developer platform that allows developers to create, store, manage, and share their code.
- There are many People who have shared a lot of topics related to GitHub recon, so in this write-up, I’ll highlight the main important points — like how to specifically target an organization and how to use dorks in correct way
- Here we begin the first lesson
- that Github is divided into 3 sections
((ORG Page — User Page — Github Page))
- The organization page on GitHub — meaning you’re only doing recon on the org’s own page, specifically in the repositories that are managed by the organization itself.
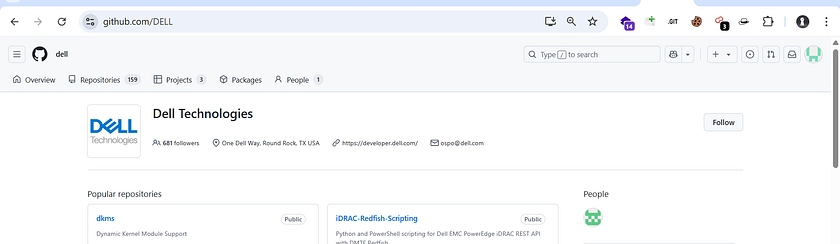
- So, I explained that first you should understand the organization, then create your dorks accordingly, and finally perform the recon on the target.
Examples:- org:dell path:server
org:dell path:jenkins
org:dell path:api_
org:dell path:internal
- So The Next One (User Page) Check the People on Org Github Page

- This way, you’ll find many employee profiles who belong to the organization. Then you can manually use dorks on their profiles, where there’s a good chance of finding valuable data.
- And The Last One is Github Page (Search on All Github)
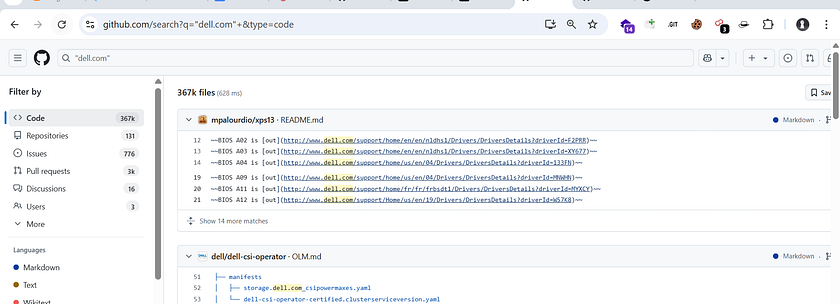
- In this, you have a much higher chance of finding data — but many people just use the common dorks that are already available, and when they don’t find anything, they get demotivated :(
I’m repeating the same point I mentioned in the first line — until you understand the organization, you can’t do good recon. So first, understand the organization, then create your dorks.
Examples:-
"dell.com" path:key_
"dell.com" forget password
"dell.com" language:java "passwd"
"dell.com" OR "dell" OR "delltechnologies.com" password
"dell.com" path:credentials
"dell.com" language:text "Internal" "Private use only" You don’t just have to think like a hacker — you also need to think like a developer and a DevOps engineer to properly understand the organization.
- References
So Move To the Next Topic Gitlab Reconnaisiance
GitLab is an Open Source code repository and collaborative software development platform for large DevOps and DevSecOps projects.
- It was simliar Like Github But here, the way you perform dorks is a bit different.
- How to search specific Org Related Data on Gitlab
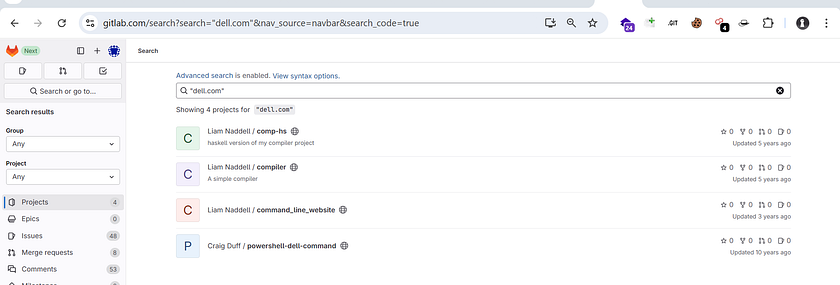
“dell.com” search on all gitlab
“@dell”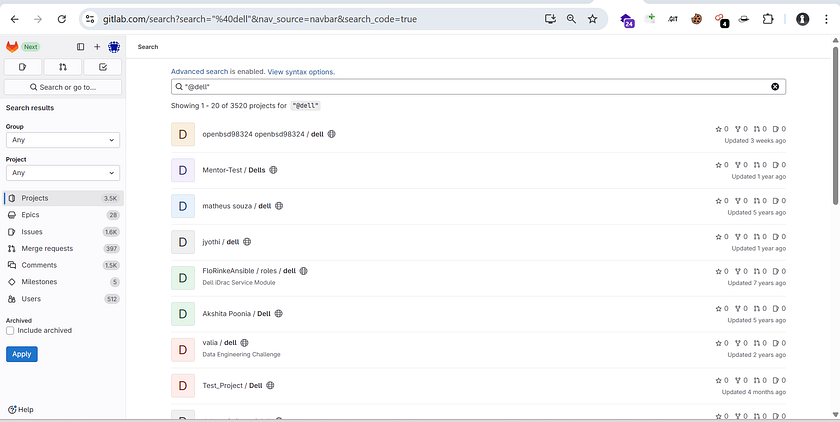
- Find Users Belongs to Org
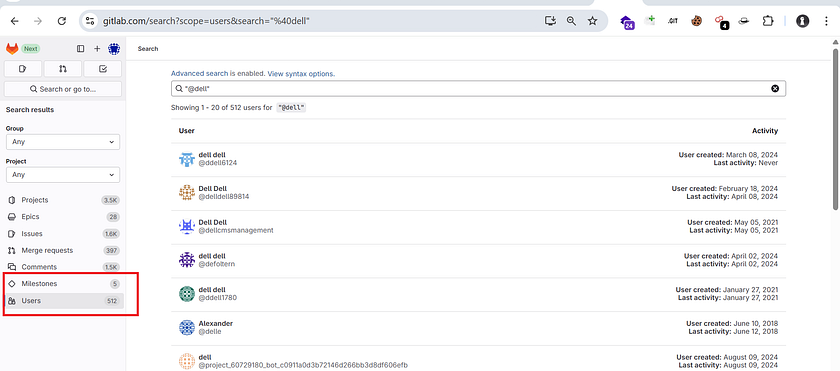
- Just like you perform dorks on GitHub, you can also perform them on GitLab.
Examples:-
"dell" logs
"google.com" secret_key
"dell.com" private
"dell.com" internal Thanks All , Happy Hacking :)






































