Incident Report
A Critical tool for minimizing damage , ensuring compliance and improving an organization's overall security posture.

A cyber security incident report document is security event detailing waht happened how it was handled and the action taken to prevent future occurrences.
Importance of cyber security incident report
It provides much - needed data and context for security teams to deal with the incident and minimize potential repercussions.It empowers the management to make better strategic choices to help prepare for future threats.
Structure of a Cyber Security Incident Report
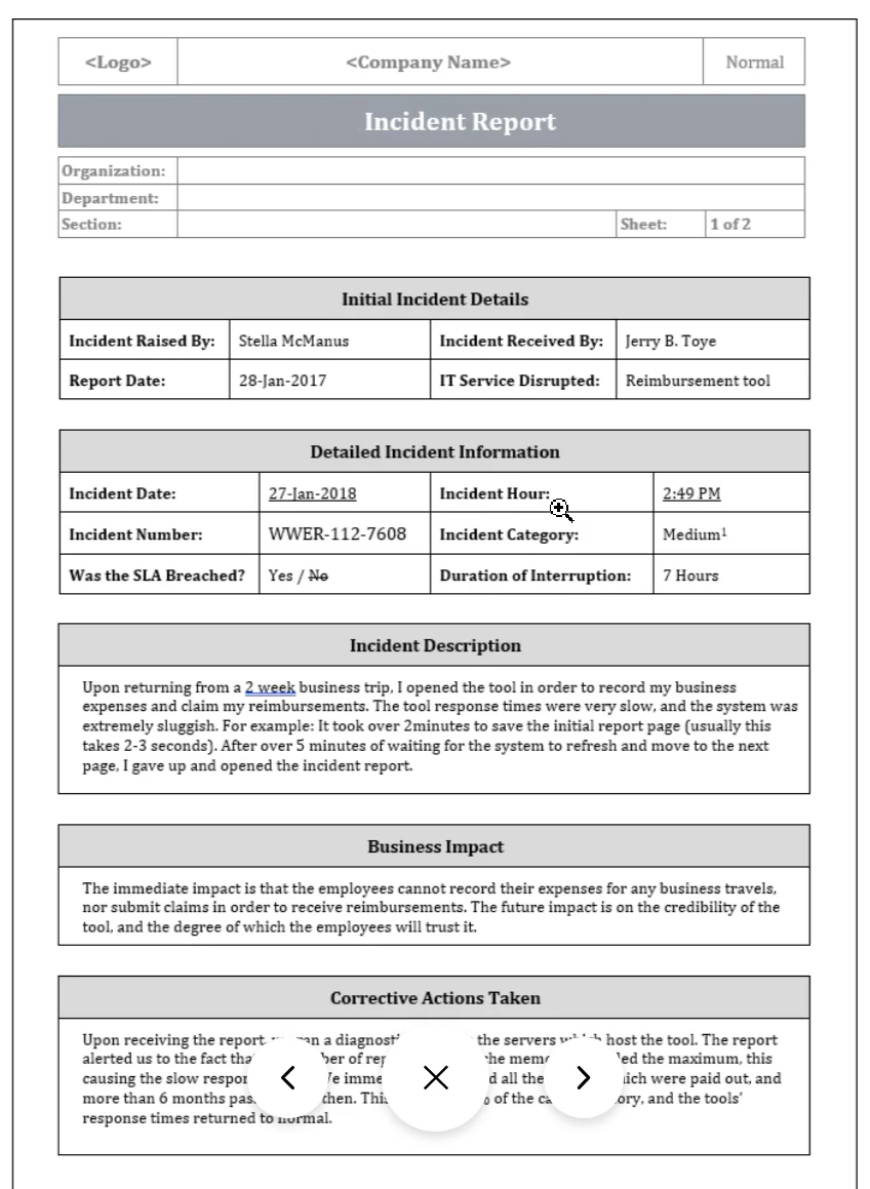
Executive Summary : This section provides a high level , non-technical overview of the incident for the management . It will include
- Incident ID : A unique identifier for tracking.
- Incident type : example : malware, physhing , data breach , denial - of - service (DDOS) .
- Summary : A breif description of what happened and its impact.
- Status : The current status of the incident (example : Contained , Eradicated , Resolved)
Incident details : This is the core of the report containing the factual account of the event.
- Timeline : A chronological account of key events , from the time of occurrence to discovery and beginning of response.
- Attack Vector : How the attacker gained access ,such as phishing email , week credentials or an unpatched vulnerability.
- Affected data : Details as any sensitive , protected , or cofidential data that was compromised.
- Observed symptoms : A description of any unusual behavior such as a system slowdown , strange log entiries or account lockouts.
Impact Assessment : The section outlines the full scope of the damage caused by the incident .
- Operational impact : Disruptions to business processed or serivce.
- Data impact : The type and volume of data lost , exposed , or corrupted.
- Financial impact : Cost associated with recovery , remediation and potential fines.
- Reputation impact : The effect on customer trust and the company's public image .
- Regulatory / Legal implications : Required notifiactions under laws like GDPR or HIPAA.
Response and Remediation : This part details the actions taken to manage the incident and fit the underlying issues.
- Containment actions : Immediate steps taken to stop the attack from spreading , such as isolating affected systems or resetting credentials.
- Eradication efforts : Measures to remove the root cause and any malicious code.
- Recovery steps : Action taken to restore systems and data from backups.
- Evidence Preservation : How digital evidence , such as system logs was collected and stored for potential forensic analysis.
Post - incident review : This section focuses on learnring from the incident and strengthening future defences.
- Root causes analysis : An investigation into the fundamental reasons why the incident occured.
- Lession learned : What the organization can take away from the experience including what worked and what didn't
- Recommendations : Proposed actions to improve future security controls and incident respose processed.
Communication Logs : A detailed record of all internal and external communication related to the incident.
- Notifications : Who was informed when and through what channel.
- Regulatory reporting : Any required notifications to goverment bodies.
- Stakeholder Communication : Customers , business partners or law enforcement.
Conclusions : This includes lessons learned from cyber events , improvement , recommendations, refrences and citation links etc. We can also attach evidences screenshots logs etc.