"Isn’t OSINT Just Glorified Googling?"
Many people think OSINT (Open-Source Intelligence) is just “fancy Googling,” but it’s much more than that. OSINT is a structured way of gathering and analyzing information from many sources — not just Google. It covers the surface web, social media, public records, the deep web, and even parts of the dark web. Unlike casual searching, OSINT involves careful verification, spotting patterns, connecting dots, and using advanced tools like Maltego or SpiderFoot. This makes it a powerful method for investigations such as cybercrime, human rights, and war crimes.

When I tell people what I do for a living, the usual reaction is: “Wait a minute, you mean you get paid to just Google stuff all day?!” Well, no, not quite.
Though it’s true that Open Source Intelligence (OSINT) does involve gathering information using the Internet, it’s much more than just Google (or Bing, or Yahoo, or Yandex) searches on steroids.
Not convinced yet? Fair enough; here’s my list of 8 key differences between OSINT-ing and Googling:
1. Scope
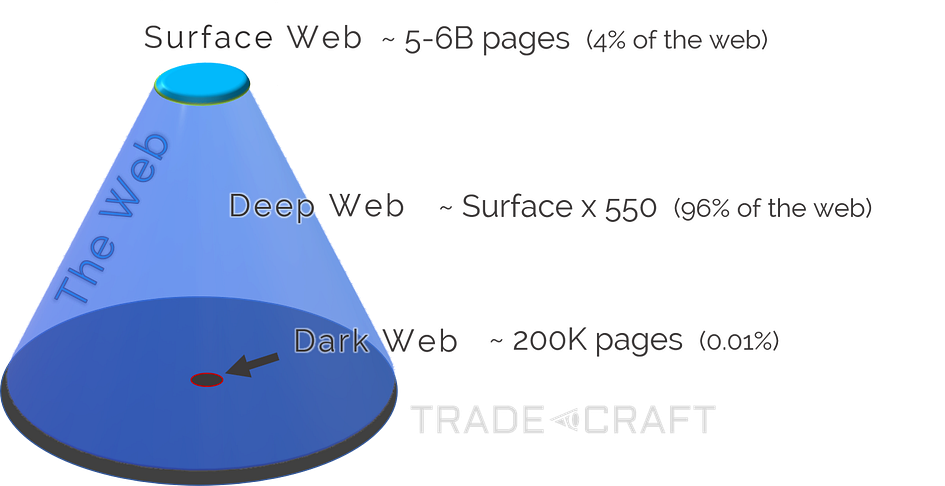
A search engine is a useful tool for finding information on the Internet and specifically on the Surface Web (the 4% of the Internet that’s actually visible and accessible to search engines), OSINT is a more systematic and comprehensive approach to gathering and analyzing information from the entire Internet and beyond.
Besides the Surface Web, an OSINT investigation typically involves Deep Web sources, which aren’t accessible to Google (and friends) and therefore don’t appear in search results, as well as Dark Web sources that can only be accessed using special browsers, such as TOR for example.
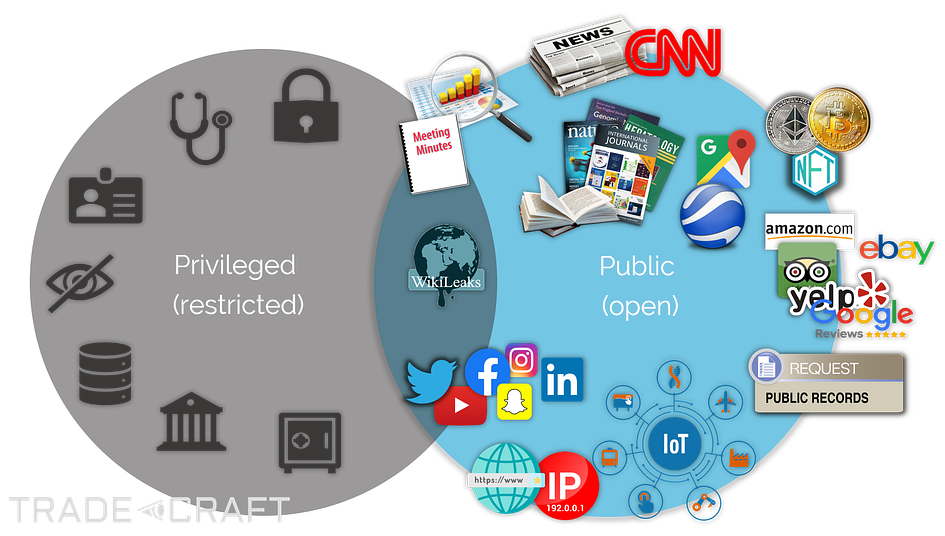
To find the information they need, OSINT investigators may spend hours, days, or even weeks trawling through social media and content-sharing platforms, e-commerce and review sites, public records and databases, leaked information and breached data, crypto exchanges and marketplaces, FTP servers, Dark Web sources, hardcopy publications (books, newspapers, magazines, and even pamphlets/fliers on occasion), radio and television broadcasts, or various other public sources.
2. Uses
Most people use search engines to quickly answer a simple question or find a specific piece of information such as events in the news, information about celebrities, sports results, recipes, and so on.
OSINT is used in cases where a quick search isn’t enough because the questions it seeks to answer are more complex or because the information needed to answer them is more difficult to find.
For example, OSINT is frequently used to investigate issues like human and civil rights violations, environmental and other disasters, criminal activity including cybercrime, and even military actions and war crimes, as has been made abundantly clear during the current war between Russia and Ukraine.
3. Verification
Any intelligence is only as good as the data it’s based upon. The massive amount of false information that’s generated daily on every topic imaginable, from celebrity gossip to critical health and safety advisories, means that OSINT must verify the accuracy and reliability of all its information before reaching any conclusions.
So while most people don’t normally question the truthfulness or accuracy of the search results they’re looking at, skepticism and a critical eye are second nature to OSINT investigators, who do everything possible to confirm the accuracy of any information they find by checking multiple sources and using various fact-checking techniques.
4. Analysis
Unlike search engines that tend to find individual pieces of information, OSINT’s primary goal is to gather all relevant information about a subject from any available sources and analyze the data to find connections, trends, and patterns that lead to useful intelligence. After all, that’s what puts the INT in OSINT.
For example, to find out whether a person is affiliated with a particular group or organization, you might seek specific news articles mentioning such an affiliation. An OSINT investigator, on the other hand, might decide to map out that person’s entire social network based on a detailed exploration of their online activity and their social media contacts and interactions to conclusively prove such ties exist and how deep they run.
5. Methods
OSINT also frequently involves using techniques such as platform-specific search strings; image and video analysis; metadata and source code exploration; network analysis; and link analysis, sometimes combined with specialized reconnaissance tools such as Maltego, SpiderFoot, and Recon-ng.
Search engines, on the other hand, rely on algorithms to generate lists of results that they deem most relevant to your search query.
For example, while an average searcher might use reverse image search to find where on the web a particular photograph appeared, an OSINT investigator could pick up on details in the photo’s foreground, background, or metadata that tell them a lot about where and when the photo was taken, and in some cases even reveal the identities of the people involved.
6. Expertise
To effectively do their work, OSINT practitioners usually need at least some knowledge of the different tools and techniques that are out there. And since the OSINT landscape is fluid and constantly evolving, most professionals in this field spend a considerable amount of time educating themselves on the latest changes and developments to stay at the top of their game.
Sometimes, investigators may have more advanced training in skills like data mining, imagery analysis, or programming or even have specific subject matter expertise in disciplines such as geopolitics, cybersecurity, or criminology.
Google searches, by comparison, don’t really require any special expertise and can be done by anyone with an Internet connection.
7. Anonymity
To avoid compromising their investigations or unintentionally revealing their identity, OSINT practitioners will usually take extra precautions to protect their anonymity and privacy, minimize their digital footprint, and prevent the subjects of their investigations from becoming aware of their presence and activity.
These precautions include the use of things like VPNs to mask or spoof IP addresses, Virtual Machines to keep investigations separate and to protect the host computer against malware, and “sock puppets” — i.e. fake social media accounts — to avoid using real accounts.
Average web searchers don’t usually resort to such measures (even though using a VPN is highly recommended for everyone these days).
8. Documentation
For all but the simplest searches, an average search engine user can’t easily track their search steps to show how they went from point A to point B to point X, nor what the full results were at each step. They might be able to dig through their search engine or browser history, but it might still be quite difficult to accurately retrace their path.
In OSINT, documentation is an integral part of the process that enables investigators or their clients to access the original information later on (and usually see it just as it appeared when it was first discovered), to show how the investigative process unfolded, and to preserve the findings as evidence for use in legal or other proceedings.
To achieve such comprehensive and accurate documentation, an OSINT investigator will use methods and tools such as timestamped screenshots, webpage snapshots and archiving, and note-taking and mind-mapping applications.
OSINT ≠ Googling
The bottom line? Doing OSINT and “Googling it” are not equivalent activities. The first is a process, the second is an event.
And though OSINT may (and often does) use search engines, it takes searches many steps further and goes much deeper than a regular web search. It usually also involves many more sources, approaches every step methodically (including documenting its processes and findings), and requires a unique blend of expertise, skills, and tools.






































