Why Your Company Is a Prime Target for Hackers: Understanding the Real Threat
Learn why companies are prime targets for hackers. Understand data breach costs, ransomware threats, and build a resilient security strategy to protect your business.

The digital world has undergone a radical transformation. Your business now not only has to battle for position in the sector, but also to fight the cybercriminals crossing borders and their threats. It does not matter if you are managing a Fortune 500 company or a small to medium enterprise; hackers consider your company to be a goldmine. The real issue is not if an attack will occur, but when. Knowing the reasons why your company is being targeted is the first move in constructing a strong defense that works and actually lasts..
The Financial Reality: Why Hackers Target Businesses

Put bluntly, hackers are after companies because that is where the money is. The average cost of a data breach in the world landed at $4.9 million in 2024, which showed a 10% yearly rise. These costs for large companies go through the roof; losses from a single incident run into hundreds of millions of dollars. Besides the immediate financial loss, a company has to deal with the fallout that comes from a halt in operations, eroding trust among customers, fines imposed by regulators, and long-term reputational damage that may take years to bounce back from.
Manufacturing companies choose the most severe punishments. For example, an automobile manufacturer can lose over $22,000 every minute its production lines are at a standstill. This creates a situation of perfect urgency-the manufacturers want to return to their normal workflow in the shortest time possible, and the cybercriminals are aware of this. They are banking on this urgency, hence demanding huge ransoms, knowing the company would rather pay than suffer losses equivalent to paying the ransom.
This cyber crime has grown so much that it has attained an organized and industrialized level. Ransomware-as-a-Service platforms work just like normal businesses: they have customer support and different price levels. The most prominent business model includes double extortion: invading the victim's data and threatening to expose it unless the money is paid. Also, in Q1 of 2025, the count of victims displayed on data leak sites surged by 213% when compared to the same time in 2024.
Your Data Is Worth More Than You Think

Organizations possess a lot of highly valued data, which hackers can quickly sell for a good amount. Information such as the customer's names, addresses, and financial information is easily sold in large lots on the dark web; it is for this reason that the prices for such datasets are high, affecting millions of customers-thus creating six-figure profits for the criminal syndicates.
The most lucrative, and thus not surprisingly, are the financial records and payment data, which explains why organizations dealing with credit card information and transaction histories are practically sitting on the criminals' goldmines. This is also the reason why financial services always come out as the primary target since they are the ones who literally control access to money.
Yet another category comprises intellectual property and trade secrets. Designs, source code, manufacturing processes, and strategic plans themselves carry enormous value for competitors or other companies involved in such clandestine activities. Even employee data and login credentials can lead to deeper breaches. An employee's password being stolen is not just his or her own problem but also a potentially open gateway to the whole organizational network.
It is hard to imagine the magnitude of credential theft. An 800% rise in credentials stolen via infostealer malware was recorded within the first half of 2025, amounting to 1.8 billion taken off 5.8 million infected devices. The attackers make use of these credentials in their following attacks, and as many people have the habit of reusing passwords across different accounts, one compromised password can open access to both banking systems and corporate tools.
The Attack Surface Has Exploded
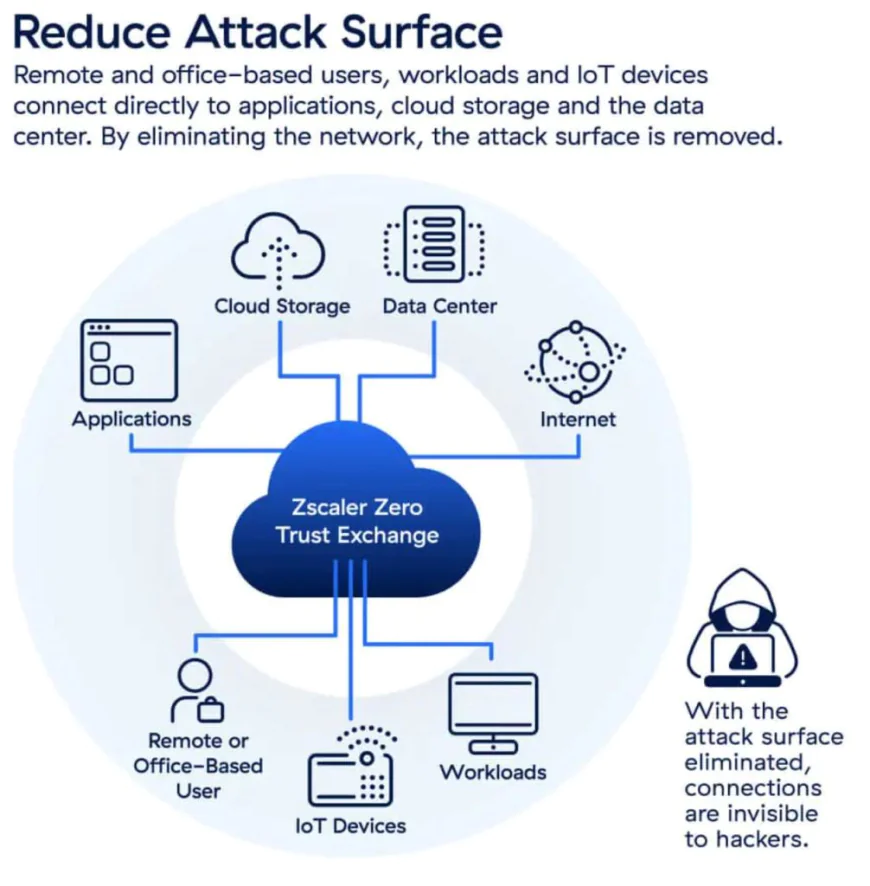
Digital transformation has dramatically increased the attack surface that companies need to protect. Nowadays, organizations are using multiple cloud environments, letting people work from home, connecting with a lot of third-party vendors, and using IoT devices in their operations. Every single thing has the potential to become a weakness.
The hybrid and remote workplace in this regard has been the most significant one shift. Attackers found out that by infecting a worker's home personal device, they could directly get access to a company network. A non-managed personal device, used for both work and personal purposes, was the case for 46% of the systems compromised by infostealers. This changed the game for perimeter-based security models making them no longer suitable.
The cloud infrastructure is just another factor contributing to the complexity. Datadotcom has predicted that 72% of data breaches in 2025 will involve data stored in the cloud, and the ones using multi-cloud will suffer the highest average breach cost of $5.05 million. One of the biggest vulnerabilities is cloud misconfigurations-settings that accidentally expose sensitive data to the internet.
The problem is made worse by the third-party vendors' involvement. It was estimated that 36% of all data breaches in 2024 could be traced back to compromises involving third parties, which is an increase of 6.5% compared to the previous year. Supply chain attacks are increasingly becoming very effective, and that is why they are so widely used; less secure vendors with access to your systems are the victims and then the infiltrators move to the main targets through that access.
The Human Element Remains Your Biggest Vulnerability

Data breaches cannot be prevented by technology alone. In the year 2025, human aspect is going to be the factor in 60% of the data breaches that will occur, where the employees will be getting duped by phishing or the insiders will be obtaining data in the middle of such scams. Negligence of employees is the main cause of data breaches that accounted for 56%, making it the largest category of security incidents.
Phishing is still reigning as the most proficient attack strategy and in one out of six data breaches-so in 16% of them it was the first access route-it's more than any other method. Hackers are sending pretend emails that look like they are from trusted sources, asking for password resets or the download of fake documents that seem to be from reputable companies.
The complexity of these attacks has reached incredibly high levels. Artificial Intelligence is pushing the envelope of social engineering. The attackers now use AI for large-scale phishing campaigns to create hyper-personalized and grammatically accurate phishing emails. There was a 1,265% increment that has been reported in AI-related phishing campaigns. Moreover, apart from email, the deepfake technology is allowing fraudsters to act like top management in video conferencing.
Attacks relying on Business Email Compromise (BEC) impersonating executives with hacked emails are costing companies $4.67 million on average per case. Organizations that have more than 1,000 employees have a weekly BEC scam probability between 83% and 97%.
Your Industry Makes You a Bigger Target
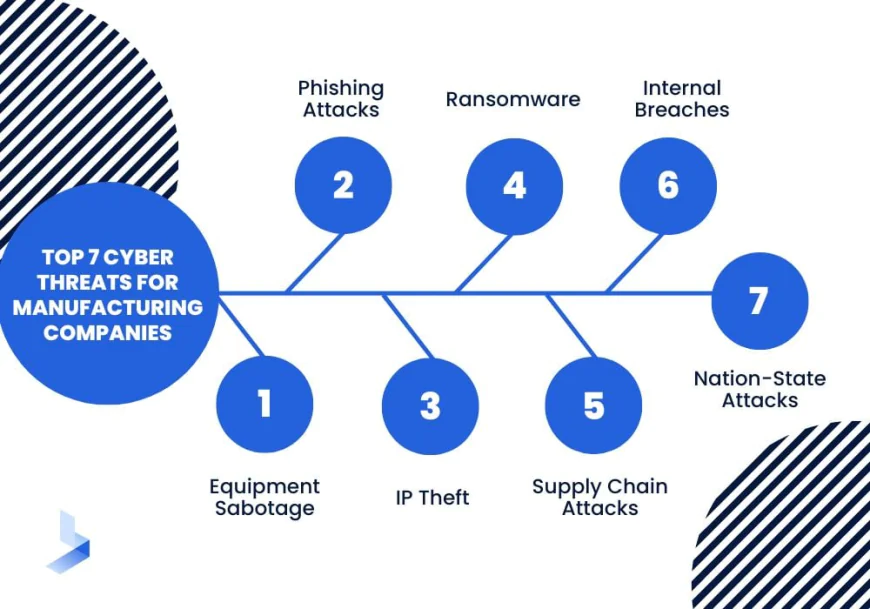
Some areas of the economy draw in attackers more than others. Manufacturing has been the most attacked sector for the last four years in a row and has thus gathered 26% of the total cyber assaults. Manufacturers are particularly hard pressed because any disruption to the production line is very evident, and it is also horrendously costly.
Medical care is another industry that is on the list of attackers' most favored targets. The value of patient information is immensely high, and it is said that a single record in the healthcare database is sold for ten times more than a credit card number on the black market. Furthermore, the healthcare facilities have no choice but to keep operating since any downtime could result in the death of a patient.
The financial industry is a constant target. These companies process daily high-value transactions, maintain large stores of sensitive financial information, and are directly linked to money. The cost incurred by a data breach in the financial sector is on average $4.45 million.
Building a Resilient Defense Strategy
The evolution of the threat landscape is such that organizations have to change their security approach fundamentally. It is no longer possible to completely block every attack. The only way out is to prioritize containment, detection, and recovery in the defense strategy.
Zero Trust architecture has become the principle upon which modern security is built. Unlike the classical models that considered the network perimeter to be secure, Zero Trust model does not trust anything by default. Every access request must be verified explicitly, and authentication involves more than one factor, thus significantly cutting down on lateral movement in case an intruder manages to secure an initial foothold.
Identity and access management requires special focus since credential abuse is responsible for 22% of incidents. Organizations should apply strong authentication, adopt least-privilege access controls, have routine access reviews, and spot unusual login activity.
Training and awareness programs for employees are still a must-have. Technology is an essential aspect of protection, but humans are still the most important defensive asset if they receive proper training. Regular security awareness training greatly decreases the risk of falling for phishing and increases incident reporting.
Managing Risk Across Your Organization
In order to build effective security, it is necessary to have comprehensive risk management frameworks that align security with business objectives. Various frameworks, such as NIST CSF 2.0, offer organized methods for all types of enterprises. The methods help in recognizing the risks, setting up protection, spying on security incidents, managing the occurrence, and getting back to the previous state after a disruption.
Business continuity and disaster recovery planning are vitally important for the resilience of the organization. Well-equipped organizations with verified plans recover quicker and better from breaches causing lesser operational impacts and at the same time ensuring compliance with the regulations that are applicable-be it GDPR, HIPAA, or specific industry requirements.
A Practical Path Forward
To comprehend the reasons behind your company being a target is the first step. The crucial part is converting threat awareness into effective security measures. A vast number of security teams face issues with limited resources, lack of complete visibility into their security posture, and inability to prove ROI to the executive management.
This is the point where holistic security and compliance frameworks bring in their importance. Integrated tools offer one centralized view of security posture, instead of separate tools for compliance tracking, vulnerability management, and incident response. One such platform is IntelligenceX which empowers businesses to design and implement risk-first information security policies that are in line with their particular requirements. It aids in the detection and ordering of risks according to their role in the business, introducing controls in accordance with NIST and ISO 27001 frameworks, concurrently managing compliance evidence for different audits, and delivering reports that show security to stakeholders as being effective.
The amalgamation of these functions results in organizations tackling the issue of complexity, improving the uniformity of their undertaking, and lastly allowing security teams to devote their time to the prioritization of strategies. As a matter of fact, one of the benefits that come with integrated platforms is that they ease the management of compliance audits in a more efficient way. Weeks of manual evidence collection for each audit are eliminated, as the platforms keep a continuous record of control implementations, test results, and evidence documentation, thus significantly cutting down the time for audit preparation while also improving the results.
Conclusion
Your firm is a target for criminal activities, since the latter can convert your priceless assets into money. The danger is not only real but also very sophisticated and more and more automatic. Assisting with this understanding is what makes it possible to set up defenses that work. The idea of security as an impenetrable fortress against attacks is a misconception-in fact, it is impossible to block all of the attacks that could be launched. A different approach is taken by security which consists of identifying the assets that are most important, determining what the threats are against those assets, applying security measures that are in proportion to the risk, monitoring for incidents closely, and rectifying the situation if breaches occur.
The organizations that actually have security that works are the ones that combine technical controls such as zero trust architecture with human-centered training, business resilience planning, and comprehensive risk management frameworks. Your company is among the first to be targeted since crime pays and the market offers a reward for hacks. The companies that will prosper are those that recognize this fact and give the necessary defenses which are in accordance with the level of sophistication of the modern threats.
.