Secure SDLC Integration Across Dev and Ops -How DevSecOps Is Redefining Software Security Without Slowing Innovation
In modern software delivery, speed without security is a ticking time bomb. As DevOps continues to blur the lines between development and operations, integrating security throughout the Software Development Life Cycle (SDLC) is no longer optional — it’s a cultural necessity. This blog explores how leading organizations are weaving security into every phase of their DevOps pipelines — from code commit to production rollout — using practical, automation-driven techniques. We’ll break down how DevSecOps transforms SDLC into a living, secure ecosystem, ensuring teams ship faster and safer without slowing innovation.
Introduction: The Shift from Reactive to Proactive Security
For years, software security used to be like the last-minute seatbelt check — applied just before deployment. But today, with continuous delivery, cloud-native workloads, and microservices, waiting until the end of the pipeline to test security is a luxury no team can afford.
Modern DevOps teams are deploying code multiple times a day. That speed demands a new philosophy: security must move left — starting right from the design and development stages.
This isn’t just about tools; it’s about a culture of shared responsibility where developers, ops engineers, and security analysts all play equal roles in protecting the software ecosystem.
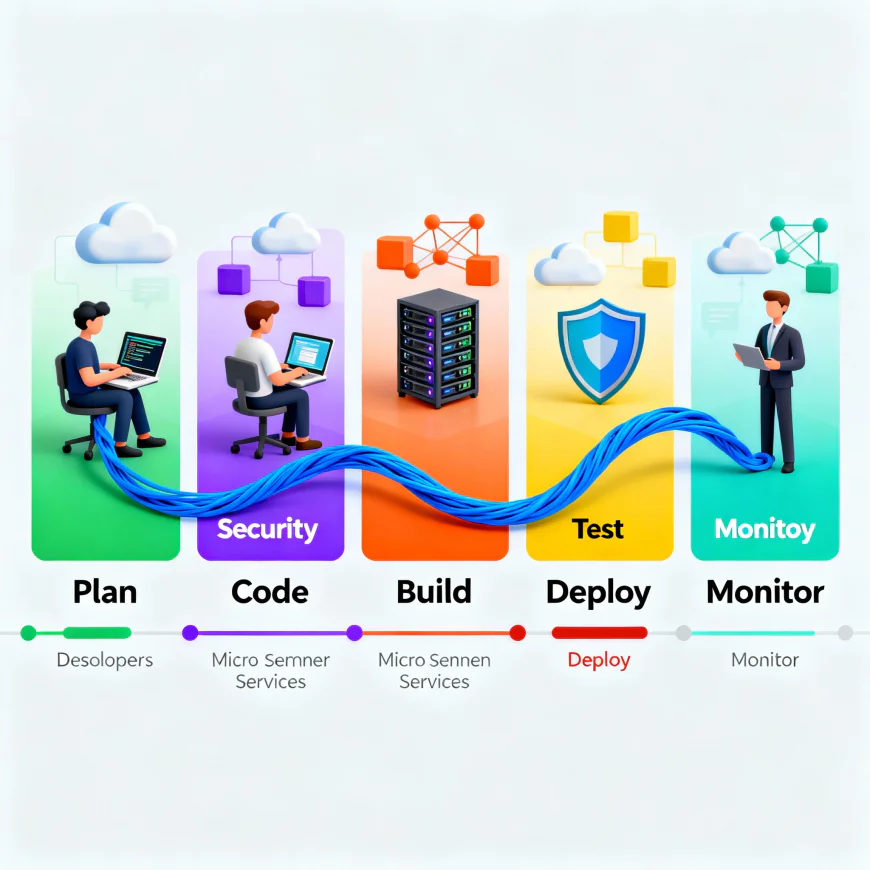
Embedding Security Early: The “Shift-Left” Approach
“Shift left” is more than a buzzword — it’s the backbone of Secure SDLC (SSDLC). The idea is to identify and fix security flaws early, when it’s cheaper, easier, and less disruptive.
In a typical DevOps workflow:
- Developers commit code →
- CI pipeline runs →
- Security scans execute automatically alongside builds →
- Any vulnerabilities are flagged in real-time.
For example, SAST (Static Application Security Testing) tools like SonarQube, Checkmarx, or Semgrep integrate directly into CI pipelines, scanning every code commit for vulnerabilities.
Automated Security in CI/CD Pipelines
Automation is where DevSecOps truly shines. Every security gate should be a part of the CI/CD lifecycle — not an afterthought.
Some best practices include:
- Automated Dependency Scanning: Tools like Snyk or Trivy check open-source dependencies for known CVEs.
- Container Image Scanning: Before pushing to registries, images are scanned for vulnerabilities using Clair or Grype.
- Infrastructure as Code (IaC) Security: Policies enforce secure Terraform or Kubernetes configurations (using Checkov or OPA Gatekeeper).
This way, security tests run as automatically as unit tests — giving feedback without slowing down developers.

Policy as Code: Guardrails, Not Roadblocks
Security can’t be manual anymore. In fast-paced environments, policy as code ensures consistent, repeatable enforcement.
For instance:
- Use Open Policy Agent (OPA) to automatically deny insecure Kubernetes manifests.
- Enforce secrets management policies via HashiCorp Vault or AWS Secrets Manager.
- Apply tagging and least-privilege IAM policies dynamically through Terraform pipelines.
The goal? To make security invisible — guardrails that protect, not walls that slow down.

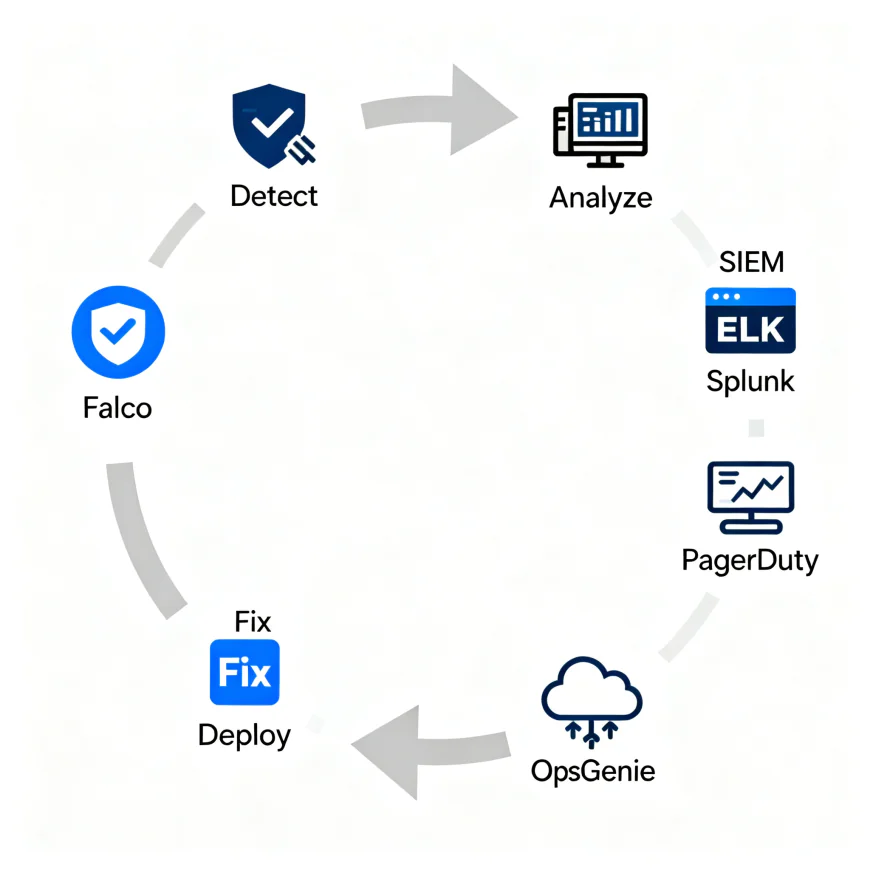
Continuous Monitoring and Feedback Loops
A Secure SDLC doesn’t end at deployment — it extends into production. Continuous monitoring ensures systems remain secure even as new threats evolve.
Integrate:
- Runtime Security Tools like Falco for Kubernetes intrusion detection.
- SIEM Platforms like Splunk or ELK Stack for centralized log analysis.
- Incident Response Automation through tools like PagerDuty or OpsGenie.
Security alerts should loop back into development sprints, creating a continuous feedback cycle — not a one-time audit.
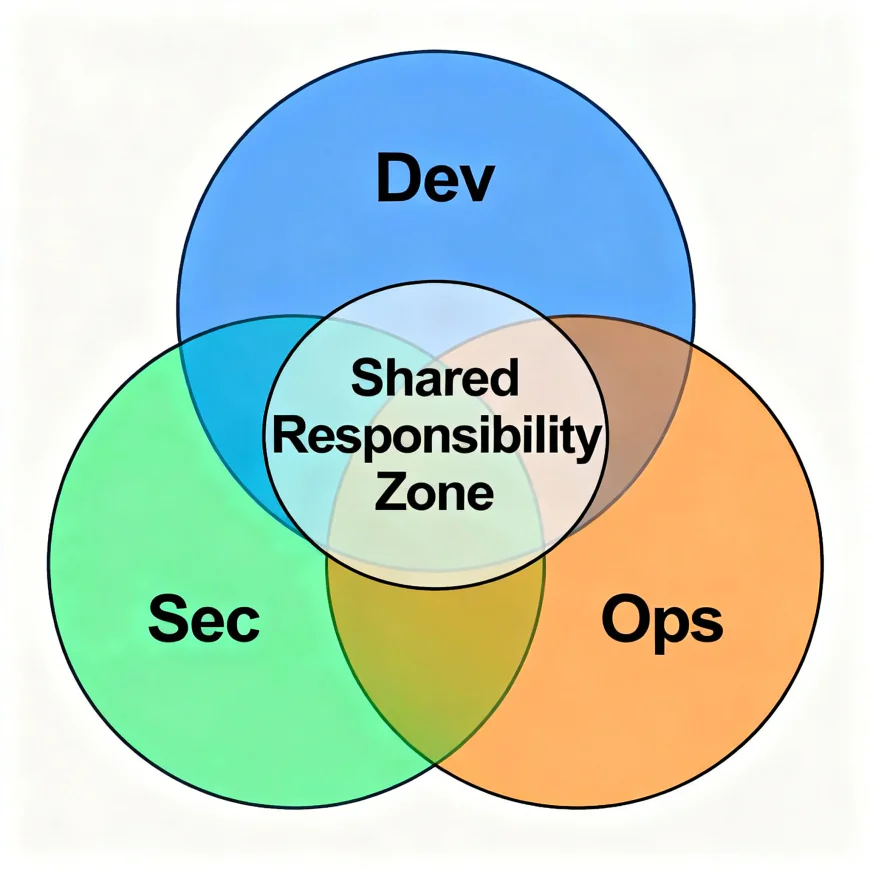
Culture and Collaboration: The Human Element
The biggest shift in Secure SDLC isn’t technical — it’s cultural.
Security can’t live in silos anymore. Developers, Ops, and Security must communicate in real time, share visibility, and collaborate through shared dashboards and alerts.
Practical steps include:
- Regular security standups within DevOps teams.
- Security champions inside development teams.
- Gamified training to encourage proactive learning (e.g., simulated attacks via OWASP Juice Shop).
When security becomes a shared language, it stops being a blocker and starts being an enabler.
Conclusion: Building Trust into Every Commit
Integrating security across Dev and Ops isn’t a one-time task — it’s an ongoing mindset shift. A truly Secure SDLC doesn’t just produce safe code; it builds trust — between teams, users, and systems.
As automation takes care of the repetitive work, humans can focus on what matters most: thinking ahead, anticipating risks, and architecting resilience.
In a world of accelerating deployments and evolving threats, the future of DevOps isn’t just faster — it’s secure by design.











































