Beyond Firewalls: Practical Threat Modeling and Risk Assessment for Modern DevOps Pipelines
In an era where pipelines deploy faster than security teams can blink, traditional defenses like firewalls and scanners simply aren’t enough. Modern DevOps pipelines demand security that moves with the code not after it. This is where threat modeling and risk assessment step in, helping teams visualize potential attack paths long before they become incidents. This blog dives deep into real-world approaches to integrating threat modeling into CI/CD workflows, bridging the long-standing gap between development speed and operational safety. You’ll learn how to identify high-risk assets, prioritize realistic attack vectors, and embed continuous risk assessment right into your delivery process turning DevOps into DevSecOps by design, not by accident.

Introduction: Why Firewalls Aren’t Enough Anymore
Once upon a time, security meant a good firewall, a strong password policy, and a weekly scan.
But fast forward to today — code is deploying dozens of times a day, APIs talk to APIs, containers spin up and die within seconds… and your traditional firewall? It’s still sitting at the perimeter, guarding a castle that doesn’t exist anymore.
Modern DevOps pipelines move too fast for static defences.
Security now needs to be part of the code, not a gate after the code.
That’s where threat modelling and risk assessment come in — they help us think like attackers before attackers even show up.

What Exactly Is Threat Modelling (and Why DevOps Teams Should Care)
Threat modelling isn’t about filling spreadsheets or writing 50-page reports.
It’s a thinking process a way to understand:
“What can go wrong in my system?”
“Who might attack it?”
“How can I defend smartly without slowing delivery?”
In DevOps terms, threat modelling means:
- Identifying critical assets (like source code, credentials, deployment tokens, production databases)
- Mapping data flows across your pipeline (from commit → build → deploy → monitor)
- Spotting weak points (for example: exposed secrets, misconfigured runners, open ports)
- Creating mitigation actions (add IAM rules, enforce least privilege, add scanning, etc.)
Instead of patching reactively, you’re now designing security proactively baked right into the development cycle.
Integrating Threat Modelling into Your DevOps Pipeline
Threat modelling becomes powerful when it’s continuous not a one-time workshop.
Here’s a practical breakdown:
Step 1: Identify Your Critical Assets
List everything attackers would love to steal or tamper with your code, secrets, API keys, build server credentials, etc.
Step 2: Map Your Data Flow
Draw how your data moves from developer machines → GitHub → CI/CD runners → cloud → production.
Where data flows, threats follow.
Step 3: Identify Potential Threats
Use frameworks like STRIDE or PASTA, or even simple brainstorming:
- Where can data be intercepted?
- Can someone inject malicious code in builds?
- Is there a chance of privilege escalation in containers?
Step 4: Define Mitigations
Add realistic defences:
- Enable MFA for repos and CI/CD tools
- Use secrets managers (AWS Secrets Manager, Vault, etc.)
- Integrate SAST/DAST scans in CI/CD
- Enforce policy-as-code (e.g., OPA, Checkov)
Step 5: Automate & Review Regularly
Automate risk checks inside your pipelines:
- Scan Docker images before deployment
- Run IaC misconfiguration checks
- Auto-report new risks via Slack or Jira
When new microservices or features are added, re-run the model.
Security evolves just like your application.
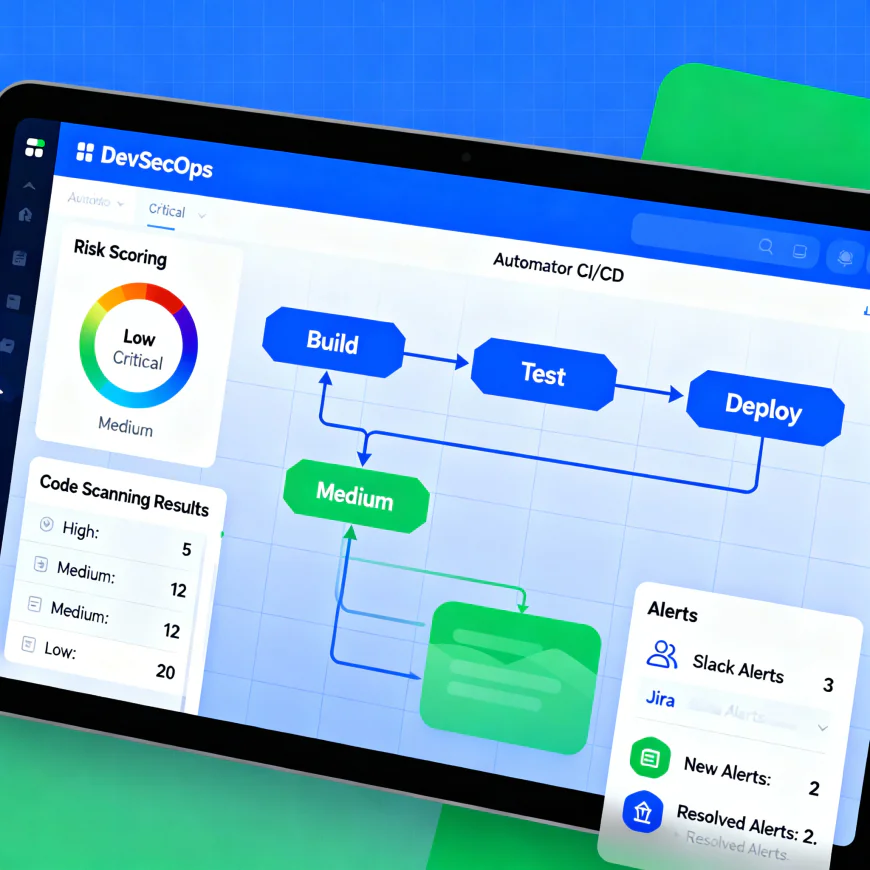
Risk Assessment: The Reality Check
Risk assessment answers a crucial question
“Out of all the threats, which ones actually matter right now?”
Every risk has two faces:
- Likelihood (How likely is it to happen?)
- Impact (How bad will it be if it happens?)
For example:
|
Threat |
Likelihood |
Impact |
Risk Level |
|
Hardcoded AWS Keys |
High |
Critical |
High |
|
Outdated Dependency |
Medium |
Medium |
Moderate |
|
Slow CI/CD Runner |
High |
Low |
Low |
Focus your limited time on the High and Critical ones.
Risk-based prioritization makes sure security doesn’t slow down development it guides it.
Bringing It All Together DevSecOps by Design
Imagine this workflow:
- Developer commits code
- Pipeline auto-runs static scans
- Threat model dynamically updates
- Risk report gets pushed to Slack
- Only safe builds move to staging
That’s not fantasy.
That’s modern DevSecOps security built-in, not bolted on.
Teams who implement this approach notice:
- Faster patching
- Fewer production incidents
- Better collaboration between Dev, Sec, and Ops
- Clearer visibility into where the real risks are
The goal isn’t to make pipelines slower it’s to make security invisible yet powerful.
Conclusion: Shift Left, But Think Forward
Threat modelling and risk assessment aren’t about paranoia they’re about clarity.
They help your team see the system the way attackers would, before those attackers ever do.
When integrated into DevOps pipelines, they become your silent security engineers always watching, always learning, always adapting.
So, the next time you push code to production, ask yourself
“Did my pipeline think like a hacker today?”
Because in modern DevOps, that’s what keeps your systems truly safe.











































