Minimal Container Images for Secure Deployments - Optimizing Security in Modern Deployments
In a world where every MB matters and every vulnerability can become a headline, minimal container images have become the new backbone of secure deployments. By stripping containers down to their essentials — no shells, no extra libraries, no bloat — DevOps teams are achieving faster builds, smaller attack surfaces, and simpler compliance. This blog dives deep into how “less” truly means “more” in modern cloud security — exploring real-world practices, tools, and examples that show how lightweight containers are redefining security, performance, and trust in CI/CD pipelines.

Introduction: When Less Becomes More in DevOps
Containerization revolutionized how we package and deploy applications — but it also introduced an unexpected side effect: bloat.
Over time, DevOps teams started building containers that were hundreds of megabytes in size, packed with unnecessary utilities, debugging tools, and dependencies that had nothing to do with production.
This is where minimal container images come into play.
They aren’t just about shaving off size — they’re about shrinking your attack surface, improving supply chain security, and delivering faster, cleaner, and more predictable deployments.

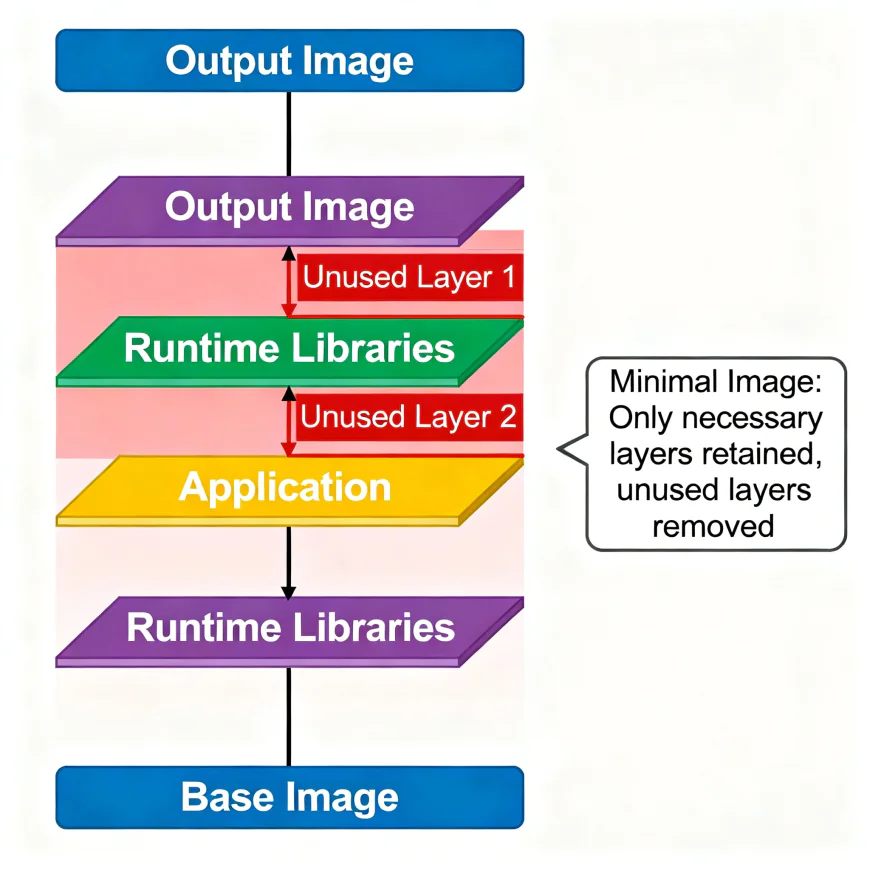
What Are Minimal Container Images?
A minimal container image includes only what’s absolutely necessary for your application to run — nothing more.
Think of it like a production-ready diet plan for your application.
If your app only needs Node.js to run, you don’t need Bash, curl, or vim hanging around inside that image.
Examples of popular minimal base images:
- Alpine Linux — ~5MB, popular for its size and simplicity.
- Distroless Images (Google) — contain only your app and runtime libraries (no shell, no package manager).
- Scratch — the smallest possible base image, literally empty (used for Go or static binaries).
Why Minimal Images Are a Security Game-Changer
- Smaller Attack Surface
Fewer binaries and libraries mean fewer vulnerabilities.
Tools like bash, curl, or apt are common targets — removing them drastically reduces the number of possible exploits. - Reduced CVE Exposure
Vulnerability scanners (like Trivy or Grype) report fewer CVEs on smaller images since they have fewer packages to analyze. - Simplified Compliance & Auditing
Auditors love clarity. When your container only contains your app and its runtime, it’s easier to prove there’s no hidden or unauthorized software. - Immutable & Predictable Deployments
No shells mean no manual tampering. Developers can’t log in and “fix” things in prod — ensuring deployments remain consistent with source code.

Performance Benefits: It’s Not Just About Security
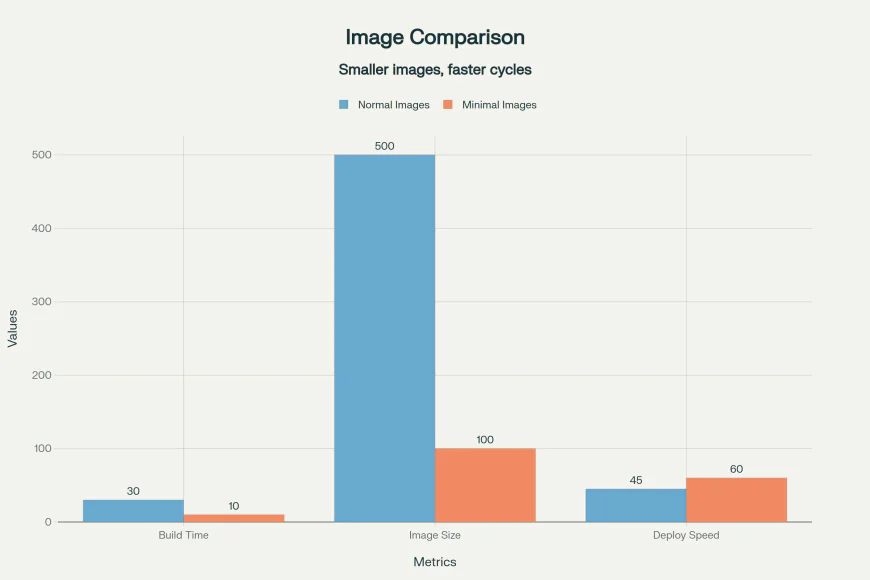
- Faster CI/CD Pipelines: Smaller images build and push faster through registries.
- Faster Scaling: Containers spin up quicker in Kubernetes, improving auto-scaling responsiveness.
- Lower Bandwidth and Storage Costs: You save GBs in container registries and network transfers.
Imagine shaving 200MB off an image that deploys across 50 pods — that’s 10GB saved per release cycle. Multiply that by dozens of pipelines, and you’re looking at serious cost and performance wins.
Best Practices to Build Minimal Container Images
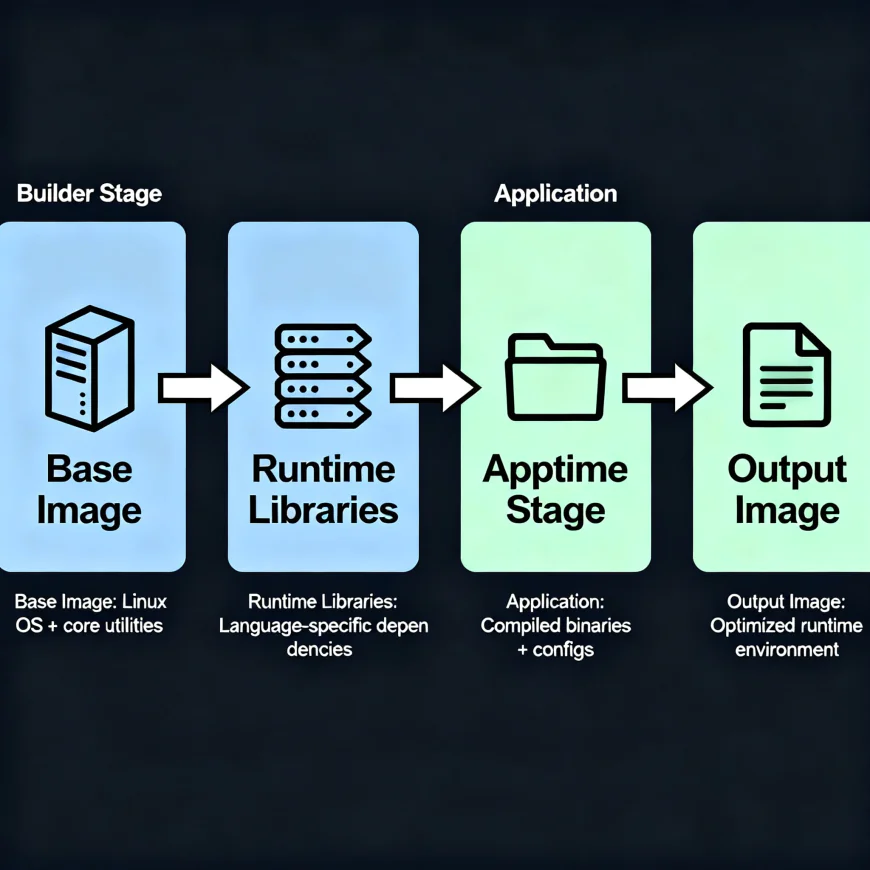
- Use Multi-Stage Builds
Build your app in one stage (with all dependencies), then copy only the final binary or required files into a lightweight base image. # Stage 1: BuilderFROM golang:1.22 AS builderWORKDIR /appCOPY . .RUN go build -o main .# Stage 2: Minimal runtimeFROM scratchCOPY --from=builder /app/main /ENTRYPOINT ["/main"]- Pick the Right Base Image
Choose based on your runtime: - Go → Scratch or Distroless
- Python → Alpine or Slim
- Node.js → Distroless Node or Alpine
- Regularly Scan Your Images
Use security scanners like: - trivy image
- grype
- Avoid Installing Debug Tools in Production
Use observability tools externally — not inside your container.
15. Leverage SBOMs (Software Bill of Materials) Generate SBOMs using tools like Syft or Docker Scout to track exactly what’s in your image.
Real-World Examples
- Google Cloud Distroless Containers — used widely in Google Kubernetes Engine (GKE) for hardened production workloads.
- Netflix & Shopify — both utilize minimal images to speed up build pipelines and reduce CVE exposure.
- GitHub Actions & AWS Lambda — run lighter, faster, and cheaper with minimal image optimizations.
Balancing Minimalism and Debuggability
It’s tempting to go ultra-minimal — but remember, production debugging gets harder without a shell.
A practical approach is to maintain two versions:
- app:latest → Minimal, production-ready.
- app:debug → Includes shell and tools for troubleshooting (not deployed in production).
This balance ensures security without sacrificing visibility during troubleshooting.

Conclusion
Minimal container images are not just about size — they’re about discipline.
By reducing what runs inside your containers, you tighten your security posture, accelerate deployments, and gain predictable, auditable environments.
In modern DevOps, security and performance aren’t trade-offs — they’re partners.
Minimalism brings them together, making your containers lighter, faster, and safer than ever before.