Triple Threat Alert: 29.7 Tbps DDoS Record, React's Critical RCE, and RansomHouse's Global Rampage
December 2025 brings unprecedented cyber threats: Cloudflare blocks record-shattering 29.7 Tbps DDoS attack from Aisuru botnet, React Server Components expose millions to CVSS 10.0 RCE vulnerability nicknamed React2Shell, and RansomHouse ransomware group escalates attacks across multiple sectors with data-only extortion tactics. Critical cybersecurity update: 29.7 Tbps DDoS attack sets new record, CVE-2025-55182 React vulnerability threatens 39% of cloud environments with remote code execution, RansomHouse ransomware targets global organizations with pure data extortion. Immediate action required.
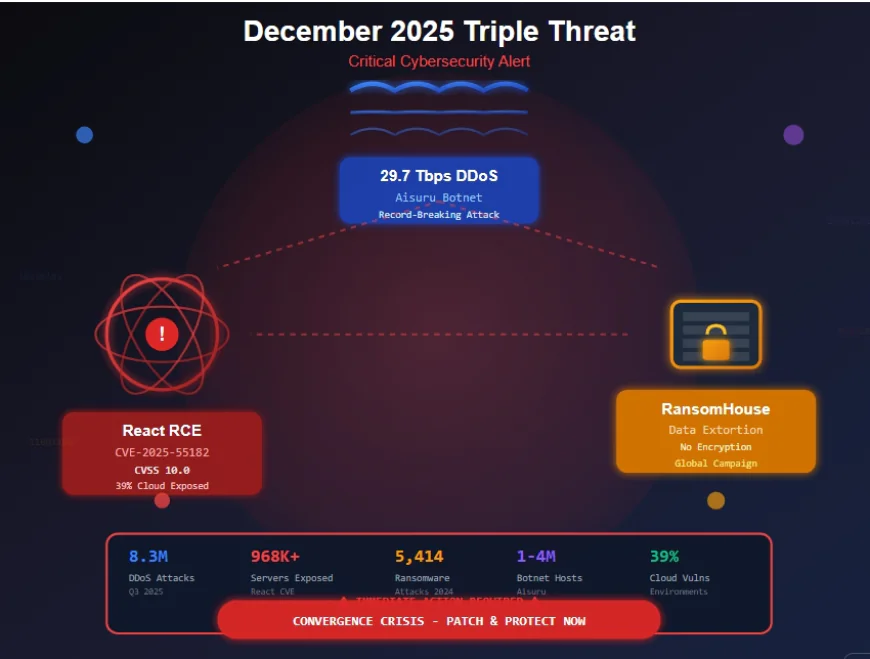
December 2025 is proving to be one of the most tumultuous months in recent cybersecurity history. Three major threat categories have converged simultaneously, creating a perfect storm that demands immediate attention from security teams worldwide. Organizations are facing record-breaking DDoS attacks exceeding 29 Terabits per second, a maximum-severity vulnerability exposing millions of React applications to unauthenticated remote code execution, and an aggressive ransomware campaign targeting global enterprises with pure data extortion tactics.
This convergence isn't coincidental—it represents the evolving sophistication of modern cyber threats and the expanding attack surface that organizations must defend. Let's break down each threat and understand what security teams need to do right now.
Threat #1: The 29.7 Tbps DDoS Monster - Aisuru Botnet Rewrites the Record Books
The New Normal: Hyper-Volumetric Attacks
Just when we thought DDoS attacks couldn't get any larger, the Aisuru botnet shattered all previous records with a devastating 29.7 terabits per second attack in Q3 2025. This wasn't an isolated incident, it represents a fundamental shift in the DDoS threat landscape.
Key Statistics:
- The 29.7 Tbps attack was a UDP carpet-bombing attack bombarding an average of 15,000 destination ports per second
- In Q3 2025, Cloudflare mitigated 1,304 hyper-volumetric Aisuru attacks, representing a 54% increase quarter-over-quarter
- The distributed attack randomized various packet attributes in an attempt to evade defenses
- The latest record-breaking attack also reached 10.6 billion packets per second and lasted only 40 seconds
The Aisuru Arsenal: Unprecedented Scale
The Aisuru botnet represents the apex of DDoS capabilities, with an estimated 1-4 million infected hosts globally. This massive army of compromised devices enables sustained, hyper-volumetric attacks that can overwhelm even the most robust defenses.
Attack Characteristics:
- Multi-vector attacks: 99.996% UDP floods combined with reflection amplification
- Port carpet-bombing: Targeting thousands of ports simultaneously
- Evasion techniques: Randomized packet attributes to bypass detection
- Sustained campaigns: Average of 14 hyper-volumetric attacks daily
Industry Impact: No Sector Is Safe
DDoS attacks against AI companies surged by as much as 347% month-over-month in September 2025, demonstrating how attackers adapt to target emerging technologies. The Mining, Minerals & Metals industry also saw significant targeting during escalating EU-China trade tensions.
Economic Reality:
- Average DDoS attack cost in 2024: $6,000 per minute
- Average attack duration: 39 minutes = $234,000 per incident
- In Q1 2025 alone, there were 20.5 million DDoS attacks almost matching all of 2024
What Changed: The IoT Threat Multiplier
The explosive growth of IoT devices has created an unlimited supply of potential botnet recruits. The largest Q4 2024 attack involved over 13,000 IoT devices and peaked at 5.6 Tbps, demonstrating how connected devices with weak security become weapons in attackers' arsenals.
Immediate Defense Actions
For Security Teams:
- Capacity Planning: Ensure DDoS mitigation can handle multi-Tbps attacks
- Cloud-Based Protection: On-premise appliances cannot handle this scale
- Multi-Layer Defense: Combine network-layer and application-layer protection
- Real-Time Monitoring: Implement automated detection and mitigation
- Incident Response: Prepare playbooks for hyper-volumetric attacks
Critical Insight: The rise in attack size renders capacity-limited cloud DDoS protection services or on-premise DDoS appliances obsolete. Organizations must upgrade to unlimited, cloud-based protection immediately.
Threat #2: React2Shell – The CVSS 10.0 Nightmare Affecting 39% of Cloud Environments
The Critical Vulnerability: CVE-2025-55182
On December 3, 2025, the cybersecurity world received devastating news: a critical vulnerability CVE-2025-55182 rated CVSS 10.0 was disclosed in React Server Components. This maximum-severity flaw enables unauthenticated remote code execution—the holy grail of vulnerabilities for attackers.
Vulnerability Profile:
- CVE ID: CVE-2025-55182 (React), CVE-2025-66478 (Next.js)
- CVSS Score: 10.0 (Maximum Severity)
- Attack Vector: Network, unauthenticated
- Impact: Complete server compromise
- Nickname: React2Shell
How Bad Is It? Catastrophically Bad.
Wiz data indicates that 39% of cloud environments contain instances of Next.js or React in versions vulnerable to CVE-2025-55182 and/or CVE-2025-66478. This represents a massive attack surface spanning millions of applications worldwide.
Scope of Exposure:
- React has over 1.97 billion total downloads and is downloaded over 20 million times weekly
- In 2024, React was used by 82% of JavaScript developers
- 61% of cloud environments have publicly exposed Next.js instances
- More than 968,000 servers running modern frameworks like React and Next.js have been identified
The Technical Reality: Unsafe Deserialization
The vulnerability allows unauthenticated remote code execution by exploiting a flaw in how React decodes payloads sent to React Server Function endpoints. Even worse, even if your app does not implement any React Server Function endpoints, it may still be vulnerable if your app supports React Server Components.
Attack Mechanics:
- Attacker crafts malicious HTTP request
- React Server Components deserialize payload unsafely
- Arbitrary JavaScript executes on server with full privileges
- Complete server compromise achieved
Wiz constructed a fully working RCE proof-of-concept with near-100% reliability, meaning exploitation is trivial once technical details are analyzed.
Affected Versions and Frameworks
Vulnerable React Packages:
- react-server-dom-webpack (19.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-parcel (19.0, 19.1.0, 19.1.1, 19.2.0)
- react-server-dom-turbopack (19.0, 19.1.0, 19.1.1, 19.2.0)
Affected Frameworks:
- Next.js (versions >=14.3.0-canary.77, >=15, >=16)
- React Router
- Waku
- Expo
- Redwood SDK
- @parcel/rsc
- @vitejs/plugin-rsc
Fixed Versions Available
React Patches:
- 19.0.1
- 19.1.2
- 19.2.1
Next.js Patches:
- 16.0.7
- 15.5.7
- 15.4.8
- 15.3.6
- 15.2.6
- 15.1.9
- 15.0.5
Why This Matters: The Master Key Exploit
"This newly discovered flaw is a critical threat because it is a master key exploit, succeeding not by crashing the system, but by abusing its trust in incoming data structures," said Justin Moore of Palo Alto Networks Unit 42.
The system executes malicious payloads with the same reliability as legitimate code, making detection extremely difficult.
Exploitation Timeline
"Exploitation is imminent" according to watchTowr CEO Benjamin Harris. As of December 3, there were no confirmed public exploits, but unconfirmed reports of exploitation are circulating.
Critical Window: Organizations have days, not weeks, before widespread exploitation begins.
Emergency Response Protocol
Immediate Actions (Next 24 Hours):
- Identify exposure: Scan all applications for vulnerable React versions
- Emergency patching: Upgrade to fixed versions immediately
- WAF deployment: Cloudflare's Web Application Firewall protects against the flaw if traffic is proxied through it
- Access monitoring: Watch for suspicious requests to Server Function endpoints
- Incident investigation: Review logs for potential exploitation attempts
For Applications Without Immediate Patching:
- Implement WAF rules to block suspicious payloads
- Restrict Server Function endpoint access
- Monitor for unusual server-side execution patterns
- Consider temporary service isolation
The Bigger Picture: Supply Chain Security
This vulnerability demonstrates the cascading risk of modern software dependencies. A single flaw in a widely-used library affects millions of applications instantly, with most developers unaware they're vulnerable until it's too late.
Threat #3: RansomHouse Ransomware – Data Extortion Without Encryption
The Unique Threat Model
While most ransomware groups encrypt data and demand payment for decryption keys, RansomHouse follows a Ransomware-as-a-Service business model where affiliates often skip encryption entirely, preferring to just steal data and threaten to release it.
This approach minimizes immediate operational disruption while maintaining extortion pressure through data exposure threats—a tactic that's proving devastatingly effective.
Recent High-Profile Attacks
November 2025 - Askul Corporation (Japan): RansomHouse claimed to have stolen 1.1 terabytes of data from Askul, a major Japanese retailer. The attack disrupted Askul's main e-commerce platforms (Askul, Lohaco, and Soloel Arena), affecting logistics networks that support major retailers including Muji and The Loft.
February 2025 - National Technology Co., Ltd. (China): RansomHouse attacked this leading Chinese semiconductor firm, with theft of TPM designs critical for securing connected vehicles and smart grids, potentially enabling state-sponsored reverse engineering or supply chain compromises.
2025 - Cell C (South Africa): RansomHouse compromised Cell C telecom data, claiming to have stolen 2TB of customer data, affecting one of South Africa's major telecommunications providers.
Supreme Administrative Court of Bulgaria: RansomHouse claimed responsibility for stealing sensitive legal and government data, demonstrating the group's willingness to target government institutions.
Attack Methodology and TTPs
Initial Access:
- Vulnerability exploitation in internet-facing systems
- Credential compromise through phishing or brute force
- Third-party and supply chain compromises
Data Exfiltration Focus:
- Proprietary business information
- Customer databases and PII
- Financial records and payment data
- Intellectual property and trade secrets
- Legal documents and confidential communications
Extortion Tactics:
- Threaten public data release
- Leverage data protection regulations (GDPR, etc.)
- Contact customers directly about breach
- Escalating pressure over time
The RansomHouse Network
Analysis reveals that RansomHouse appears to collaborate with other ransomware groups, with 11 out of 73 claimed victims also cross-claimed by groups like BianLian, Snatch, Stormous, ALPHV, LockBit 3.0, and RagnarLocker.
This suggests either:
- Shared affiliate networks
- Data trading between groups
- Coordinated campaigns
- Rebranding and restructuring
Why Data-Only Extortion Works
Advantages Over Traditional Ransomware:
- No operational disruption: Victims remain functional during extortion
- Backups irrelevant: Stolen data can't be un-stolen
- Regulatory pressure: GDPR fines add financial motivation
- Reputational damage: Public exposure fears drive payment
- Multiple extortion opportunities: Can sell data or extort multiple times
Victim Dilemma:
- Paying doesn't guarantee data deletion
- Data may already be copied/sold
- In 2024, 84% of victims paid ransoms but only 47% got their data back uncorrupted
- Public disclosure often happens regardless of payment
Sectors at Highest Risk
Primary Targets:
- Healthcare (sensitive patient data)
- Financial services (transaction records)
- Legal firms (privileged communications)
- Technology companies (intellectual property)
- Government agencies (classified information)
- Education (student and research data)
Defense Strategy Against Data Extortion
Prevention:
- Data classification: Know what sensitive data you have and where
- Access controls: Implement least-privilege principles
- Network segmentation: Limit lateral movement potential
- Data loss prevention: Monitor and block unauthorized transfers
- Encryption at rest: Protect data even if stolen
Detection:
- Anomaly detection: Unusual data access patterns
- Exfiltration monitoring: Large outbound transfers
- Behavioral analytics: Detect reconnaissance activities
- Endpoint monitoring: Track file access and copying
Response:
- Incident response plan: Pre-plan data breach scenarios
- Legal consultation: Understand regulatory obligations
- Communication strategy: Prepare stakeholder notifications
- Law enforcement: Report to FBI/IC3 immediately
- Forensic investigation: Determine scope of compromise
The Convergence Crisis: Why All Three Threats Matter Now
These three threats aren't isolated incidents—they represent the evolving sophistication and diversification of modern cyber attacks:
DDoS Evolution: Attacks have grown 817% in capacity since 2020, from 35 Tbps to 321 Tbps network capacity needed for defense.
Supply Chain Risk: A single vulnerability in React affects 39% of cloud environments instantly, demonstrating cascading dependency risks.
Extortion Innovation: Ransomware groups evolve beyond encryption to pure data theft, making traditional backup strategies insufficient.
Common Themes
- Scale and Automation: All three leverage massive scale (botnets, software dependencies, global campaigns)
- Evasion Sophistication: Advanced techniques to bypass traditional defenses
- Economic Motivation: Financially driven with professional operations
- Critical Timing: Exploitation windows measured in hours/days, not weeks
- Systemic Impact: Affect entire industries, not just individual organizations
Strategic Response: Building Resilient Security
Investment Priorities for 2025
Technology:
- Cloud-based DDoS protection with unlimited capacity
- Advanced application security testing
- Data loss prevention and encryption
- Security orchestration and automation
- Threat intelligence platforms
People:
- Security team training and certifications
- Incident response capability building
- Red team/purple team exercises
- Security awareness programs
- Executive cybersecurity education
Process:
- Continuous vulnerability management
- Automated patch management
- Regular security assessments
- Tabletop exercises and simulations
- Security metrics and KPI tracking
Conclusion: The New Normal Requires New Approaches
December 2025's triple threat demonstrates that cybersecurity has entered a new era of complexity, scale, and sophistication. Organizations can no longer rely on periodic security assessments, traditional perimeter defenses, or reactive incident response.
The Hard Truths:
- DDoS attacks will continue breaking records as botnets grow
- Supply chain vulnerabilities affect millions instantly
- Data extortion makes encryption backups insufficient
- Attack windows are measured in hours, not days
- Every organization is a potential target
The Path Forward: Organizations must embrace continuous security validation, automated defense systems, and defense-in-depth strategies. The question isn't whether you'll face these threats it's whether you'll be prepared when they arrive.
Take Action Now:
- Patch React/Next.js immediately if affected
- Verify DDoS protection adequacy
- Audit data security and exfiltration controls
- Test incident response procedures
- Don't wait for the next headline to be about your organization
The convergence of these three major threats in a single month should serve as a wake-up call: the cybersecurity landscape has fundamentally changed, and security strategies must evolve to match.










































