Akira Ransomware: The Lightning-Fast SonicWall Attack That Encrypts in Under an Hour
Akira ransomware exploits year-old SonicWall CVE-2024-40766 vulnerability in aggressive 2025 campaign, deploying ransomware in as little as 55 minutes, bypassing MFA, and targeting 40+ organizations globally with sophisticated multi-vector attacks combining unpatched devices, misconfigurations, and credential abuse. Akira ransomware targets SonicWall SSL VPN devices via CVE-2024-40766 exploitation. Learn about the July 2025 attack surge, 55-minute encryption timeline, MFA bypass techniques, and critical mitigation strategies to protect your organization from this aggressive threat.
In July 2025, cybersecurity teams worldwide faced a devastating reality: organizations were being completely encrypted by Akira ransomware in less than one hour from initial breach. This wasn't a sophisticated zero-day attack - it was the exploitation of a year-old patched vulnerability that organizations simply failed to secure properly.
The Akira ransomware group's aggressive SonicWall campaign represents a masterclass in opportunistic exploitation, combining technical sophistication with stunning speed. With encryption occurring in as little as 55 minutes and attackers successfully bypassing multi-factor authentication, this campaign demonstrates that patch management failures can be just as deadly as zero-day vulnerabilities.
The Attack Timeline: Speed Kills
Between July 22 and September 2025, Arctic Wolf observed a surge of intrusions targeting SonicWall SSL VPN devices. What made this campaign particularly dangerous wasn't just the volume, it was the velocity.
Attack Speed Metrics:
- Initial Access to Encryption: Under 4 hours in most cases
- Fastest Attack: 55 minutes from breach to full encryption
- Typical Dwell Time: Measured in hours, not days
- Response Window: Exceptionally narrow
In late July 2025, Arctic Wolf Labs began observing a surge of intrusions involving suspicious SonicWall SSL VPN activity, where malicious logins were followed within minutes by port scanning, Impacket SMB activity, and rapid deployment of Akira ransomware.
This speed fundamentally changes incident response dynamics. Traditional security playbooks assume days or at least hours to detect and respond to ransomware. Akira's methodology compresses that timeline to minutes, rendering many defensive strategies obsolete.
CVE-2024-40766: The Vulnerability That Won't Die
At the heart of this campaign lies CVE-2024-40766, a critical improper access control vulnerability in SonicWall's SonicOS with a CVSS score of 9.3.
Vulnerability Details:
- Affected Systems: SonicWall Gen 5, Gen 6, and Gen 7 devices
- Vulnerable Versions: SonicOS version 7.0.1-5035 and earlier
- Discovery Date: August 23, 2024
- Patch Release: August 23, 2024 (same day)
- CISA KEV Addition: September 2024
- Active Exploitation: July 2025 - present
The vulnerability allows attackers to achieve unauthorized access to SonicWall firewalls through improper access control in the management interface. Once exploited, it enables abuse of administrative functions including configuration backup, creating opportunities for credential harvesting.
The Triple Threat: How Akira Combines Attack Vectors
SonicWall initially investigated claims of a zero-day vulnerability being used in the attacks. However, research revealed something more insidious—Akira wasn't relying on a single flaw but combining three distinct security risks.
Attack Vector 1: Unpatched CVE-2024-40766
Many organizations never applied the August 2024 patch, leaving devices vulnerable to direct exploitation. Evidence collected during Rapid7's investigations suggests that the Akira group is potentially utilizing a combination of all three of these security risks to gain unauthorized access and conduct ransomware operations.
Why Devices Remain Unpatched:
- Patch management backlogs
- Fear of operational disruption
- Lack of vulnerability prioritization
- Inadequate asset inventory
- Migration complications
Attack Vector 2: Password Migration Failures
Organizations migrating from Gen 6 to Gen 7 firewalls frequently carried over local user passwords without resetting them - a critical step outlined in SonicWall's original advisory.
SonicWall confirmed that many incidents relate to migrations from Gen 6 to Gen 7 firewalls, where local user passwords were carried over during the migration and not reset, which was a critical step outlined in the original advisory.
Attack Methodology:
- Credentials harvested from devices vulnerable to CVE-2024-40766
- Credentials reused against patched devices
- Successful authentication due to unchanged passwords
- Full device compromise
Attack Vector 3: SSLVPN Default Users Group Misconfiguration
A subtle but dangerous misconfiguration in SonicWall's SSLVPN Default Users Group setting automatically grants broad access to authenticated LDAP users.
The Misconfiguration: This setting automatically adds every successfully authenticated LDAP user to a predefined local group, regardless of their actual membership in Active Directory. If that default group has access to sensitive services—such as SSL VPN, administrative interfaces, or unrestricted network zones—then any compromised AD account, even one with no legitimate need for those services, will instantly inherit those permissions.
Risk Scenario:
- Attacker compromises low-privilege AD account
- Account auto-added to privileged local group
- Full SSL VPN and administrative access granted
- Complete network compromise possible
Attack Vector 4: Virtual Office Portal Abuse
Threat actors discovered they could access SonicWall's Virtual Office Portal to configure MFA/TOTP on previously compromised user accounts, effectively weaponizing the security feature against victims.
Attack Flow:
- Obtain valid credentials (via CVE-2024-40766 or credential stuffing)
- Access Virtual Office Portal
- Set up TOTP/MFA on compromised account
- Authenticate with self-configured MFA
- Bypass intended MFA protections
Bypassing Multi-Factor Authentication: The Harsh Reality
One of the most concerning aspects of the Akira campaign is the successful bypass of MFA. a security control often considered the gold standard of authentication protection.
MFA Bypass Methods Observed:
1. OTP Seed Theft: SonicWall confirmed that devices running versions of SonicOS prior to 7.3 may have been susceptible to brute force attacks affecting MFA credentials. If OTP seeds are obtained by threat actors, they can be used to generate valid OTP tokens.
2. Configuration Takeover: Attackers accessing the Virtual Office Portal can configure MFA on compromised accounts before victims realize their credentials are stolen.
3. Brute Force Attacks: SonicWall noted increased threat activity from actors attempting to brute-force user credentials, including MFA challenges on older firmware versions.
The Lesson: MFA is not infallible. It's a critical security layer, but implementation matters enormously, and it must be combined with other controls.
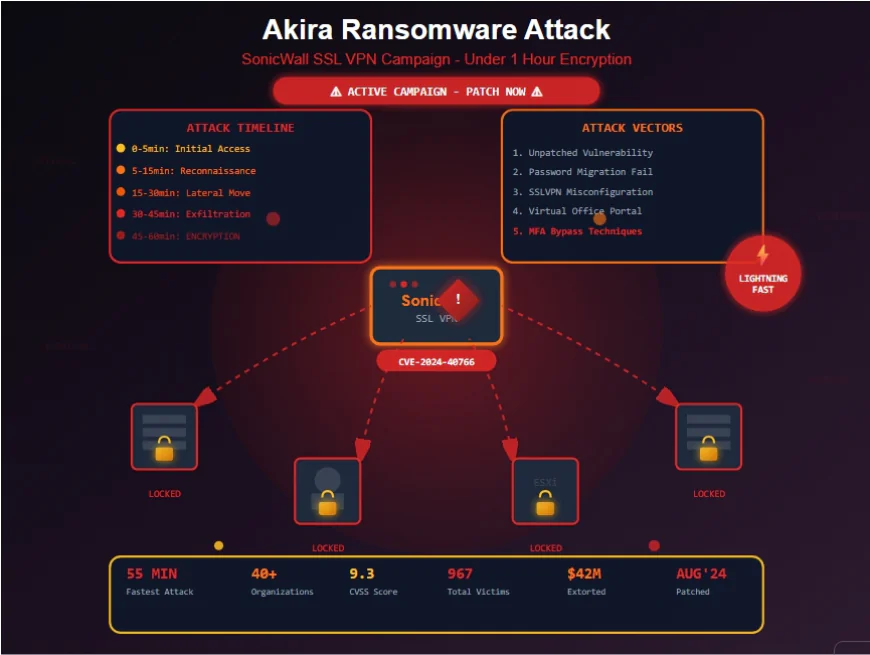
The Attack Chain: From Login to Lockout
Understanding Akira's methodology reveals a well-orchestrated attack sequence designed for maximum speed and impact.
Phase 1: Initial Access (Minutes 0-5)
- Malicious SSL VPN login via compromised credentials
- Authentication through SonicWall device
- Successful MFA challenge completion
- Establishment of foothold in network
Indicators:
- VPN logins from VPS hosting providers (not typical broadband ISPs)
- Suspicious authentication patterns
- Logins from unusual geolocations
Phase 2: Reconnaissance (Minutes 5-15)
- Network scanning using port scanning tools
- Impacket SMB activity for endpoint discovery
- Active Directory enumeration
- Identification of high-value targets
Tools Used:
- Impacket for SMB operations
- Native Windows commands
- LDAP queries for AD reconnaissance
Phase 3: Lateral Movement (Minutes 15-30)
- Privilege escalation to elevated accounts
- Service account compromise
- Movement to domain controllers
- Access to backup systems
Techniques:
- Credential dumping
- Pass-the-hash attacks
- Exploitation of trust relationships
- RMM tool deployment (Datto observed in some cases)
Phase 4: Data Exfiltration (Minutes 30-45)
- Identification of sensitive data
- Exfiltration to external servers
- Typical exfiltration: ~2GB via SSH
- Use of known Akira infrastructure
Known Exfiltration IOCs:
- IP: 66.165.243[.]39 (AS29802 HVC-AS)
- Protocol: SSH for encrypted transfer
- Volume: Varies by target value
Phase 5: Ransomware Deployment (Minutes 45-60)
- Backup deletion and stopping
- ESXi hypervisor targeting
- Ransomware binary deployment
- Rapid encryption execution
Ransomware Characteristics:
- Binary names: akira.exe, locker.exe, w.exe
- Deployment locations: C:\lock, C:\ProgramData
- ESXi-specific Linux variant
- Ransom notes dropped in encrypted directories
Total Time: 55 minutes to 4 hours from initial access to complete encryption.
Target Profile: Who's at Risk?
Akira's campaign demonstrates opportunistic mass exploitation rather than targeted attacks against specific organizations.
Victimology:
- 40+ confirmed organizations (as of August 2025)
- Multiple sectors: Manufacturing, education, healthcare, finance, transportation
- Geographic spread: North America, Europe, Asia-Pacific, Australia
- Organization size: Small to enterprise-level
High-Risk Industries:
- Manufacturing: 10% of Akira victims globally
- Healthcare: Critical data and low tolerance for downtime
- Education: Limited security budgets and resources
- Finance: High-value targets with payment capacity
Geographic Targeting: Italy shows disproportionate targeting, with 10% of Akira's victims from Italian companies compared to 3% in the general ransomware ecosystem.
The Akira Group: Background and Capabilities
Akira ransomware first emerged in March 2023 and quickly established itself as a major player in the ransomware-as-a-service (RaaS) ecosystem.
Key Statistics:
- 967 total victims as of September 2025 (Ransomware.Live)
- $42 million in extorted proceeds as of early 2024
- 143 victims in Q2 2025 alone (second most active group after Qilin)
- 40 attacks in July 2025 (third most active group)
Operational Characteristics:
- Operates double-extortion model (encryption + data leak threats)
- Ransom demands: $200,000 to $4 million
- Maintains leak site for victim pressure
- Targets both Windows and Linux (ESXi) systems
- Sophisticated affiliate network
Technical Capabilities:
- Multi-platform ransomware (Windows, Linux/ESXi)
- Hypervisor targeting for maximum disruption
- Living-off-the-land techniques
- Pre-installed legitimate tool abuse
- Advanced evasion capabilities
Detection and Response: The Narrow Window
With dwell times measured in hours rather than days, detecting Akira intrusions early is critical but challenging.
Early Warning Indicators
Network Indicators:
- SSL VPN logins from VPS hosting providers
- Authentication from suspicious ASNs
- Unusual login times or patterns
- Geographic anomalies in access
Behavioral Indicators:
- Impacket SMB activity over the network
- Rapid sequential endpoint scanning
- Active Directory enumeration
- Backup service manipulation
- Large data transfers via SSH
Host Indicators:
- Unusual process execution on domain controllers
- RMM tool installation (Datto, others)
- Credential dumping activity
- Lateral movement tools
Detection Tools and Techniques
SIEM Rules: Monitor for:
- Multiple failed then successful VPN authentications
- VPN access from hosting provider ASNs
- Rapid port scanning activity
- SMB enumeration patterns
- Backup service stops/deletions
EDR Monitoring:
- Impacket tool signatures
- Credential access attempts
- Ransomware binary hashes
- Suspicious PowerShell execution
- ESXi shell commands
Network Security:
- Anomalous SSH data transfers
- Connections to known Akira infrastructure
- Unusual outbound traffic volumes
- VPN usage pattern analysis
Critical Mitigation Strategies
Organizations using SonicWall devices must take immediate action to protect against this ongoing campaign.
Immediate Actions (Do Now)
1. Credential Rotation:
- Reset ALL SSL VPN credentials on SonicWall devices that have EVER run vulnerable firmware
- Change Active Directory passwords for accounts used for SSL VPN access
- Rotate LDAP synchronization credentials
- Remove unused or inactive local accounts
2. Patch and Update:
- Update to latest SonicOS version
- Apply all available security patches
- Verify patch application across all devices
- Document patch status for compliance
3. MFA Configuration Review:
- Audit current MFA implementation
- Verify MFA on all administrative accounts
- Review Virtual Office Portal access
- Check for unauthorized MFA configurations
4. Access Control Hardening:
- Review SSLVPN Default Users Group settings
- Implement least privilege principles
- Remove excessive permissions
- Audit group memberships
Short-Term Actions (This Week)
1. Network Segmentation:
- Place remote access infrastructure in dedicated VLANs
- Implement strict firewall rules
- Limit lateral movement paths
- Isolate critical systems
2. Monitoring Enhancement:
- Deploy EDR on systems adjacent to SMA deployments
- Configure SIEM alerts for IOCs
- Enable detailed VPN logging
- Implement real-time alerting
3. Virtual Office Portal Security:
- Restrict access to internal network only
- Disable if not operationally required
- Implement IP whitelisting
- Monitor for unauthorized access
4. Backup Verification:
- Verify backup integrity
- Test restoration procedures
- Implement air-gapped backups
- Ensure immutable backup copies
Long-Term Actions (This Month)
1. Architecture Review:
- Evaluate zero-trust implementation
- Review authentication architecture
- Assess defense-in-depth measures
- Plan infrastructure improvements
2. Incident Response:
- Develop Akira-specific playbooks
- Conduct tabletop exercises
- Train response teams
- Establish communication procedures
3. Vulnerability Management:
- Implement automated patching where possible
- Establish patch testing procedures
- Create patch priority matrix
- Document patching workflows
4. Threat Intelligence:
- Subscribe to SonicWall security advisories
- Monitor Akira group activity
- Track IOC feeds
- Participate in information sharing
If You're Already Compromised
If you suspect or confirm an Akira ransomware intrusion:
Immediate Response:
- Isolate affected systems (don't power off—forensics matter)
- Disable SSL VPN access
- Engage incident response team
- Contact law enforcement (FBI, local authorities)
- Notify cyber insurance provider
Do Not:
- Immediately pay ransom (83% who pay get attacked again)
- Delete logs or forensic evidence
- Restore from backups before investigation
- Communicate via compromised systems
Critical Investigation Points:
- Review VPN logs dating back to October 2024
- Check for data exfiltration to 66.165.243[.]39
- Examine authentication logs for suspicious patterns
- Identify all compromised credentials
- Assess backup system integrity
The Broader Implications: Lessons for Cybersecurity
The Akira SonicWall campaign offers critical lessons for the cybersecurity community:
1. Patch Management Is Critical: A year-old vulnerability remains devastating. Organizations must prioritize timely patching, especially for internet-facing devices.
2. Migration Security Matters: System migrations are high-risk periods. Security steps like credential rotation cannot be skipped or delayed.
3. Configuration Is Security: Misconfigurations like SSLVPN Default Users Group can be as dangerous as unpatched vulnerabilities.
4. MFA Is Necessary But Not Sufficient: MFA must be properly implemented and cannot be the only security control.
5. Speed Demands Detection: When attackers move in minutes, detection and response must be automated and immediate.
Conclusion: The Ongoing Threat
As of September 2025, the Akira SonicWall campaign remains active with new infrastructure continuously identified. Organizations cannot afford complacency.
Current Status:
- New IOCs identified: As late as September 20, 2025
- Active exploitation: Ongoing across multiple regions
- Victim count: Growing steadily
- Attack speed: No signs of slowing
Key Takeaways:
- Akira deploys ransomware in under an hour
- Multiple attack vectors beyond CVE-2024-40766
- MFA bypass techniques actively used
- 40+ organizations confirmed compromised
- Campaign shows no signs of stopping
Your Action Items:
- Audit all SonicWall devices immediately
- Rotate credentials on any device that ran vulnerable firmware
- Review and harden configurations
- Enhance monitoring for early detection
- Test incident response procedures