EXPOSED: How Chinese State Hackers Infiltrated European Governments Using a Sneaky Windows Trick
Sophisticated attack chain showing how Chinese hackers use spear-phishing emails with malicious Windows shortcuts to deploy PlugX remote access trojan, giving attackers complete control over European diplomatic networks and enabling massive data theft.

Your Emails Could Be the Next Target-Here's What Actually Happened
The alarm bells are going off all over the diplomatic circles in Europe, and for a valid reason. A hacking group with a connection to China carried out a series of unauthorized accesses to the computer networks of embassies in five European countries, namely Hungary, Belgium, Italy, and the Netherlands, and also the government of Serbia between September and October 2025. This is not merely a case of a cyber incident but rather an alarming reminder that even the most fortified government networks are open to attack by fierce state-sponsored hackers. The identity of the threat actor who did it? UNC6384, and their methods are chillingly straightforward but extremely successful at the same time.

The Attack That Nobody Saw Coming (Until It Was Too Late)
Consider the scenario where you get an email that looks totally legitimate, and it is merely about the meeting of the European Commission or that NATO workshop you were waiting for. Besides, the attachment seems innocent. Hence, you open it. Just in a few seconds, the most sensitive diplomatic communications of your government have been obtained by foreign adversaries. Not a hypothetical situation—several European countries have been affected, and the means of the attack turned out to be jarringly banal: a mere Windows shortcut file.
The primary infiltration was genius in its very simplicity: UNC6384 devised spear-phishing emails full of diplomatic language and themes that were virtually irresistible to their targets. These emails did not include random mass-marketing but were in fact very carefully aimed communications meant to exploit the very specific interests and responsibilities of the diplomats and government officials deeply involved in defense cooperation and coordination of multilateral policy in Europe.
The phishing campaign ramped the victims up through several steps of infection. The final payload, however, was what made the whole thing so fascinating: a weaponized LNK file, which is simply a Windows shortcut of the very same kind that billions of people use every day without a second thought. This fantastic sophistication hidden in the technology we use every day is the reason why modern cyber threats are so hard to defend against.
The Windows Vulnerability That Microsoft Still Hasn't Fully Patched
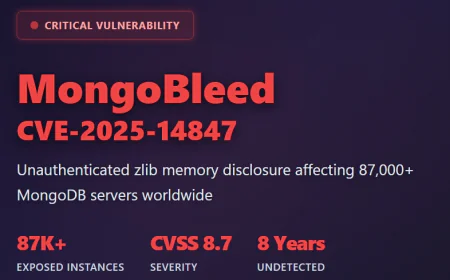
CVE-2025-9491, a Windows shortcut bypass vulnerability, which is the essential core of this campaign, has been the attackers' main technique to covertly execute malignant commands on the target's computer. The security hole has been reported by the researchers Peter Girnus and Aliakbar Zahravi in March 2025 and it has been assigned a CVSS score of 7.0 which categorizes it as a "high risk" issue.
The sad part is that despite being publicly acknowledged for several months before the UNC6384 campaign, the flaw was still very much present in most of the government networks. This is a serious breach of basic cybersecurity. It is like being aware that your front door is not locked and leaving it that way for a long time while the thieves are roaming that area.
The flaw is not something new that has come to be abused. Luckily, the researchers have already discovered that the XDSpy group, which is another cyber-espionage group, was exploiting the vulnerability in March 2025 for distributing a Go-based malware named XDigo against the government of Eastern Europe. The fact that the same flaw has been exploited by more than one advanced persistent threat group shows how very dangerous it is.
PlugX: The Remote Access Trojan That Turns Your Government Laptop Into a Spy Camera
(see the generated image above)
The execution of the harmful LNK file was the point where the actual attack chain started to reveal itself. The killer shortcut got into action at once, opening up the PowerShell command to decode and extract files from the hidden archive while showing the user a harmless decoy PDF to keep him/her unaware. The hidden parts of the archive contained three entities: a real Canon printer utility, a harmful DLL file, and the most valuable thing-an encrypted payload of PlugX malware.
PlugX is a special type of malware. This remote access trojan has many names such as Destroy RAT, SOGU, Korplug, and TIGERPLUG. It has been the most preferred choice of the Chinese state-sponsored hackers for many years because of its excellent features. And a good reason: when PlugX is installed, the attacker gets access to the full system, like a god.
Now think about it: the first thing that comes to mind is that the attackers can execute commands from anywhere, they can see every keystroke you make including the entering of passwords and confidential communications, they can upload and download files whenever they want, they can even set up things in such a way that they survive the rebooting of the system and finally they can also conduct thorough reconnaissance all over your network infrastructure. For diplomatic organizations that deal with sensitive geopolitical intelligence, this is not merely a security breach, but a potential intelligence disaster.
One of the ways this malware employs its anti-analysis and anti-debugging techniques is by causing the reverse engineering process for the security researchers to be extremely difficult. Another way of doing so is by performing persistence through Windows Registry modifications; thus, the malware remains active even after rebooting the infected system.
The Terrifying Part: They're Getting Better at Hiding
Nevertheless, the most disturbing aspect maybe the UNC6384 scenario which is continuously upgrading its weaponry in real-time. The scientists observed the CanonStager malware loader reduced its size by a huge margin-between approximately 700 KB and 4 KB-during the period from early September to October 2025. This reduction in size was a method chosen for reducing the forensic footprint while still having complete malicious functionality rather than being an accidental optimization.
In other words, hackers are learning and adapting faster than defenders are responding. The enemy is testing various methods of delivery including the use of HTML Application files that load external JavaScript code to get payloads from cloud infrastructure. This kind of tactical flexibility indicates that the enemy is not stagnant and they are always changing.
Who's Behind This, and What Do They Want?
The analysis done by the Google Threat Intelligence Group has confirmed that UNC6384 is using the same methods and tools as the Chinese state-sponsored hacking group Mustang Panda, which has been well-documented. The targeting of European diplomatic bodies dealing with defense cooperation, policy coordination across borders, and the setting up of multilateral diplomatic frameworks is really not a coincidence-it actually echoes the Chinese strategic intelligence priorities on the European side in terms of alliance cohesion and defense initiatives.
To put it differently: China is Trying to get the information about the planning in Europe, how united their military alliances are, and what policies they are coordinating. This whole campaign is just one of the many ways to collect the very high-quality intelligence that would eventually give Beijing a good position in the geopolitics negotiations.
The Defense Failed: Microsoft's Response Isn't Enough
In response to the vulnerability disclosure, Microsoft took measures to further secure its system by updating Microsoft Defender so that it can identify and stop this threat activity, and also by highlighting Smart App Control as an additional security layer. These measures seem to be quite good on paper. Nevertheless, they are actually the least that could be done.
The situation where highly skilled threat actors managed to break into a number of diplomatic institutions even after the security measures were there indicates a deep-rooted issue, and that is the reliance on detection-based defenses which turns out to be inadequate against persistent nation-state adversaries. The overreliance on detection-based defenses is the major reason why too many organizations are using such security measures without having them correctly set up, without realizing their limitations, and without practicing the necessary security hygiene to actually fight off attacks.
What This Means for Your Organization
If hackers supported by the state are able to penetrate the networks of European governments, then your organization is not safe either. This initiative should be a reality check for all organizations irrespective of their location. The consequences are obvious:
Phishing mails still work remarkably well as they play on people's weaknesses. No matter how advanced the technical security systems are, social engineering risks can never be ruled out completely. Your workers are the source of your biggest risk but also the first to protect you.
Networks are killed by known vulnerabilities. The time span between the public disclosure of CVE-2025-9491 in March and its exploitation in September shows a patch management failure. What is the number of known vulnerabilities in your environment that remain unpatched?
A series of attacks is the standard procedure. Attackers do not depend on single exploits anymore, they combine various techniques like phishing, file downloads, legitimate utility abuse, and DLL side-loading to get past layered defenses. Your security design has to be strong enough to withstand the entire chain and not just a few components.
The struggle for persistence continues forever. Your enemy, having gained entry into your system through the Registry modifications, will continue to have access forever unless you discover and remove him explicitly. This means that a breach can remain undetected for several months or even years.
How to Protect Your Organization
The lessons from this campaign demand immediate action:
Implement advanced email security that goes beyond simple signature detection. Your email system should analyze URLs, attachments, and sender reputation with behavioral analysis and machine learning algorithms.
Deploy comprehensive security awareness training that treats phishing simulation as an ongoing program, not a checkbox exercise. Employees must understand that diplomatic lures and official-looking communications are precisely what attackers use.
Execute rigorous vulnerability management. This means not just identifying vulnerabilities, but prioritizing them based on active exploitation, applying patches within defined timeframes, and maintaining an accurate asset inventory of what needs protection.
Implement endpoint detection and response (EDR) solutions that monitor system behavior in real-time. EDR platforms can identify suspicious activity patterns that signature-based defenses miss, such as unusual Registry modifications or unexpected command execution.
Segment your network so that a compromise in one segment doesn't automatically grant access to your most sensitive systems. If attackers breach a workstation, they shouldn't automatically have access to your classified file servers.
Conduct regular security assessments and penetration testing to identify weaknesses before adversaries do. Red team exercises simulate real attack scenarios and reveal blind spots in your defenses.
The Bottom Line: This Is Just the Beginning
The UNC6384 campaign represents a watershed moment in cyber espionage. It demonstrates that sophisticated nation-state actors can successfully breach even well-defended government networks using relatively conventional attack vectors—nothing exotic, nothing that requires zero-day exploits, just good old-fashioned social engineering combined with a known vulnerability that organizations failed to patch.
More troubling is the evidence that these attackers are continuously refining their techniques, reducing their malware footprints, and experimenting with new delivery mechanisms. They're not slowing down; they're accelerating.
For diplomatic organizations, government agencies, and enterprises handling sensitive information, the message is clear: the cyber threat landscape has evolved beyond detection-based security. Organizations must adopt proactive, assumption-of-breach mentalities that assume attackers will succeed at the initial compromise and prepare accordingly.
The Chinese hackers who targeted European diplomats in September and October 2025 weren't using exotic exploits or revolutionary techniques. They were using the fundamental playbook of cyber espionage: social engineering, a known vulnerability, sophisticated malware, and persistent access. The fact that they succeeded should alarm everyone responsible for network security.
The question isn't whether your organization will be targeted next. The question is: when attackers do come for you, will you be ready?