VolkLocker Ransomware Broken: Hard-Coded Master Key Lets Victims Decrypt Files for Free
Security researchers have uncovered a critical flaw in VolkLocker ransomware, revealing a hard-coded master encryption key. This weakness allows victims to decrypt encrypted files without paying the ransom, highlighting serious implementation failures in modern ransomware campaigns.

VolkLocker ransomware, a pro-Russian hacktivist group CyberVolk's newly revealed threat, has undergone a fundamental compromise due to a massive cryptographic implementation error that the SentinelOne scientists found. The VolkLocker crypto flaw shows that the users can decrypt all the files that were encrypted by the malware for free without any negotiations or ransom payments being demanded. This discovery is a giant step backward in the realm of ransomware security, as it has busted the VolkLocker hard-coded master key that was so carelessly kept within the production binaries. The unearthing of the VolkLocker hard-coded decryption key practically makes the whole RaaS operation a loss and has considerably hampered CyberVolk's ability to extract money from their criminal infrastructure.
Understanding CyberVolk and VolkLocker: From DDoS to Ransomware-as-a-Service
CyberVolk, alternatively identified as GLORIAMIST, surfaced as pro-Russian hacktivist group situated in India performing distributed denial-of-service (DDoS) attacks on government and essential infrastructure institutions. The gang eventually became notorious for its cyber activities that were politically-driven and that mainly targeted organizations that were either opposing the Russian interests or supporting Ukraine. After the significant setback of numerous Telegram account suspensions during 2025, CyberVolk reorganized and took up a new criminal business in August 2025: VolkLocker, a ransomware-as-a-service platform that provided encryption payloads and custom-made encryption payloads.
Shifting from hacktivism to ransomware-as-a-service is a move that indicates changing strategies to the more profitable ones. The RaaS model of CyberVolk charges the customers between $800 and $1,100 for single-OS versions or $1,600 to $2,200 for cross-platform binaries that support both Windows and Linux environments. The ransomware has Telegram automation that allows the customer-operators to set the payloads through an automated builder bot, interact with the victims, plan the encryption process, and even conduct ransom negotiations, all through encrypted Telegram channels. Nonetheless, the discovery of the hard-coded master key vulnerability in VolkLocker has immediately ruined the viability of the business model.

The Cryptographic Flaw: How VolkLocker Hard-Coded Master Key Undermines Encryption Security
The encryption used by VolkLocker is AES-256 and it is in Galois/Counter Mode (GCM), the very common one and the strongest symmetric encryption algorithm using 256-bit keys through Golang's "crypto/rand" cryptographic package. UE will be done through the use of a random 12-byte nonce (initialization vector) generation for every encrypted file and each file gets a custom extension like .locked or .cvolk. This strategy seems technically perfect on the face of it AES-256 in GCM mode comes to be the best encryption that no legit computer power can break within any reasonable time frame.
Nevertheless, the hard-coded master key of VolkLocker discovered by the experts at SentinelOne has made the whole strong encryption invalid. The developers did not create a master key for each victim's machine or for each encryption session, but they had hardcoded an encryption key of one master directly into the ransomware binary as a 64-character hexadecimal string. The master key cryptographic material is identical for all the victims of VolkLocker because of this fundamental design flaw.
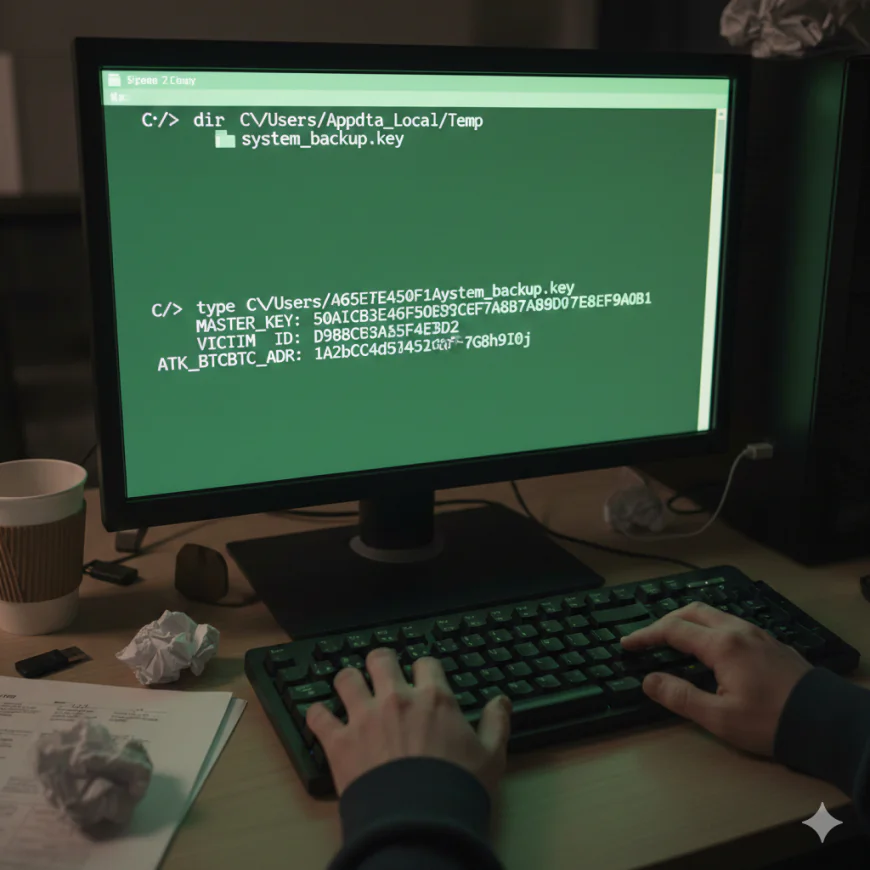
The situation is greatly worsened with the second layer of the VolkLocker hard-coded decryption key flaw. The ransomware copies this master key in plain text to the victim's temporary folder at the path: C:\Users\AppData\Local\Temp\system_backup.key. This file not only has the master encryption key but also the unique identifier of the victim and the Bitcoin address of the attacker for the ransom collection. It seems that the developer of the ransomware planned this backup key file for recovery during testing phases but catastrophically failed to remove this debugging artifact before shipping it to the actual RaaS customers.
The ransomware's plaintext backup file is not deleted during the whole process and thus, the victims who find the system_backup.key file can easily extract the master key and decrypt all their data without the need to interact with the attackers or pay any ransom. This totals up to a complete operation failure of the ransomware's major extortion method.
Technical Impact: Why the VolkLocker Hard-Coded Master Key Destroys Ransom Economics
The VolkLocker hard-coded master key vulnerability has consequences that are far-reaching beyond just the ability to decrypt data. In legitimate ransomware scenarios, criminals earn money from the psychological pressure made by data encryption plus the victims' belief that they cannot get their files back without paying. The encryption is believed to be mathematically unbreakable, thus creating a state of despair which pushes the victim to pay the ransom.
The VolkLocker hard-coded decryption key exposure does away with this psychological pressure completely. Now victims and security experts can recover entire systems without any negotiation, payment, or contact with the attackers. The master key is the same for all victims so the decryption is applicable to all rather than being specific to each breach. This results in a situation where VolkLocker has changed from a working extortion tool to an unproductive data-destruction malware variant with no revenue making method.
SentinelOne experts are of the opinion that the plaintext backup key file is a testing artifact that was unintentionally shipped in the production builds. Generally, during the development stage, ransomware inventors hold backup keys for testing and recovery purposes, planning to get rid of these debugging artifacts before actual deployment. The developers seemingly set up an automated system that would write the master key to a backup file during encryption processes but failed to do the corresponding code to delete this file or stop this feature in production versions.

Operational Characteristics: VolkLocker's Sophisticated Features Undermined by Fundamental Flaw
Apart from the disastrous VolkLocker hard-coded master key vulnerability, the ransomware exhibits other technically sophisticated capabilities that underscore the operational competence gap between CyberVolk's business infrastructure and their cryptographic implementation:
VolkLocker tries to increase its privileges right after it is executed, that is, it tries to run with SYSTEM-level access in order to get the largest possible permissions for encryption. The ransomware carries out very detailed system reconnaissance; this includes, for instance, enumerating MAC address prefixes against known virtualization vendors such as Oracle VMware and VirtualBox, and this is probably done in order to find out the sandbox and testing environments that it should not go to. The malware then makes a list of all the available logical drives and uses a very sophisticated configuration-based file selection algorithm to determine which files are worth encryption.
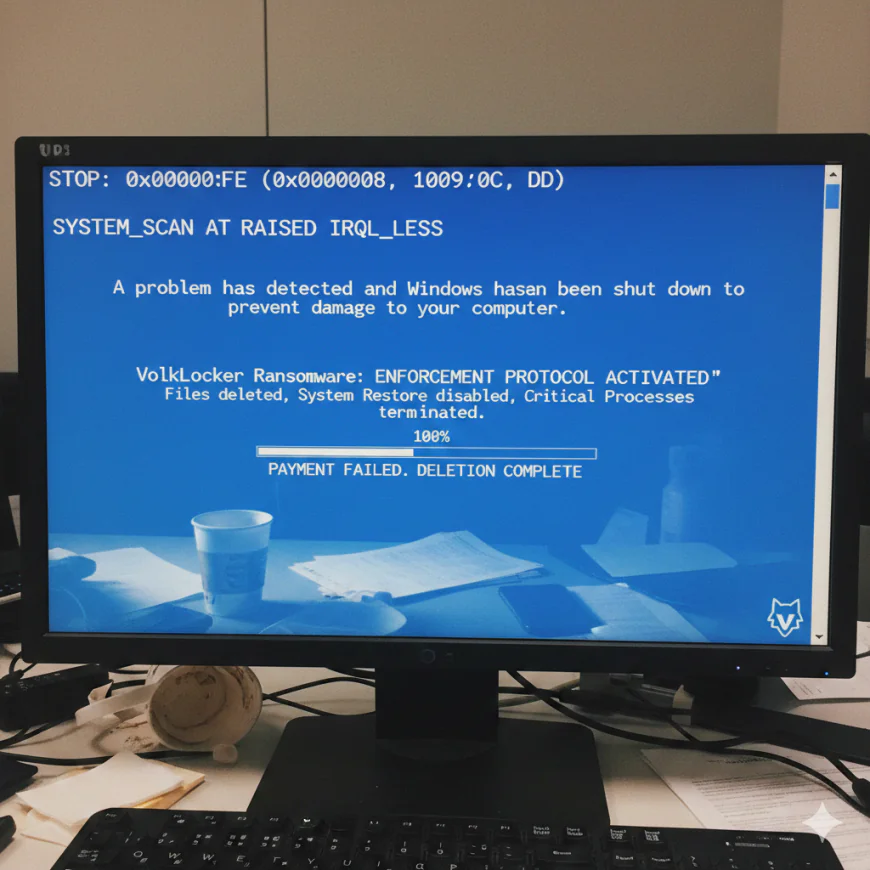
The ransomware utilizes an aggressive enforcement timer based on Golang timer functions which, if a victim does not pay up within 48 hours or inputs an incorrect decryption key more than thrice, then the repercussions will be really severe. The VolkLocker was quite harsh when the enforcement mechanism was activated as it not only deleted the content of the user’s critical directories (Documents, Desktop, Downloads, Pictures) but also got rid of the volume shadow copies thus preventing system restore recovery, killing off the analysis and antivirus processes. In some cases, the ransomware caused a Windows Blue Screen of Death through the NtRaiseHardError() API which left the system utterly non-functional.
To be honest, all these advanced operational features are nothing compared to the basic failure of the VolkLocker hard-coded decryption key design flaw. No amount of technical sophistication in terms of scouting, privilege elevation, or file selection can beat the math behind the impossibility of keeping a universally known, unencrypted master key secret.
The Broader Threat: CyberVolk's Expanding Criminal Service Offerings
The vulnerability of the hard-coded master key in VolkLocker is a spectacular failure of the cryptographic implementation but the larger CyberVolk RaaS operation shows a worrying trend in ransomware democratization. By offering complete ransomware infrastructure, automated customization tools, and Telegram-based command-and-control systems that need very little technical skill to operate, CyberVolk is deliberately bringing down the technical barriers for the would-be cybercriminals.
The gang has not just limited its operations to licensing ransomware, but has also moved into other illegal services. In November 2025, CyberVolk was seen selling a remote access trojan and a keylogger, each for $500, hinting at a system of criminal tool monetization that is integrated. The said tools might be used to infect a system with VolkLocker or to provide the hackers with the necessary credentials for later ransomware attacks.
The operational model based on Telegram is a clear indication of the industry trend among the politically-motivated threat actors. The use of encrypted Telegram channels allows the actors to have a convenient and searchable infrastructure for service advertising, customer relationship management, ransom negotiation, and law enforcement account suspension persistence. The use of the platform by a large number of people in the legitimate sector helps the criminals to hide their operations, and the fact that Telegram does not cooperate with law enforcement makes the criminals' activities less restricted.

Defense Implications: Protecting Against VolkLocker Despite the Decryption Key Exposure
The vulnerability related to the hard-coded master key of VolkLocker ransomware provides a significant chance for organizations to rid themselves of this malware. However, the public revelation of this vulnerability does not mean the end of the VolkLocker threat. CyberVolk might very soon apply a patch to the defective cryptographic implementation in its subsequent editions, and the basic danger of ransomware infection will not be any different, since organizations still face the risks of encryption, data loss, operational disruption, and extortion.
Organizations should make it a priority to completely stop VolkLocker infections and not to depend on the decryption key for recovery. This will involve the establishment of extensive endpoint protection which includes behavioral detection that identifies the execution patterns of Golang-based ransomware, network monitoring that detects the connections to CyberVolk's Telegram infrastructure, and response automation that enables quick isolation of the system upon detection.
Defenders need to keep an eye on VolkLocker's reconnaissance behavior that includes MAC address prefix enumeration trying to find virtual machines, changing registry entries suspiciously, issuing volume shadow copy deletion commands, and attempting to kill Microsoft Defender processes. These signs become visible at the start of the attack chain so that the intervention can be made before the encryption takes place.
Organizations have to set up backup systems that are immutable, isolated, and completely cut off from the production environment. In this way, even if the VolkLocker infections are so far successful, they will not be able to reach the backup infrastructure. Along with quick detection and response capabilities, resilient backups will allow for rapid recovery without negotiating with attackers or paying ransom demands.

SentinelOne's Public Disclosure Decision: Balancing Impact and Practicality
The decision to publicly reveal the vulnerability associated with the hard-coded decryption key of the VolkLocker ransomware raises significant issues concerning the proper conduct of vulnerability disclosure in the context of ransomware research. In the past, security researchers have been advised not to publicly disclose vulnerabilities in the case of ransomware where the threats are still actively working, and to keep the notification limited to law enforcement and ransomware negotiation companies that could help certain victims, so the latter option was preferred.
SentinelOne made public disclosure in support of the specific flaw's nature. The research team argues that the flaw is not in the VolkLocker encryption algorithm but rather in the main key being hard-coded and not even rigorously reproducible in distinct VolkLocker installations and versions. Some of the binaries that are in production may not have the plaintext backup key file at all and the flaw might not be present in upcoming versions as CyberVolk is correcting the implementation mistake. The researchers decided that the public disclosure is more in the interest of the larger cybersecurity community as it will bring organizations to the awareness of the vulnerability instantly and at earlier phase of rapid decryption of compromised systems.
How IntelligenceX Helps Organizations Defend Against Modern Ransomware Threats
Ransomware threats are getting more and more sophisticated, and even though some organizations are trying to prevent them, the ransomware threat has still found a way to bypass their efforts, as in the case of the VolkLocker hard-coded master key vulnerability. Such adversities push organizations to look for expert cybersecurity partners who not only identify threats but also implement detections and rapidly respond through orchestrated actions. However, discovery of vulnerabilities such as the VolkLocker hard-coded decryption key exposure gives only temporary advantages, and on the other hand, relying on the criminals’ operational failures is a very poor security strategy.
IntelligenceX, which is a cybersecurity services provider, offers a whole range of defensive solutions to be able to tackle the most modern ransomware operations such as the detection of Golang-based payloads, behavioral analytics for recognizing reconnaissance and pre-encryption activities, and the fast incident response capability where system isolation happens before encryption ends. If organizations want to improve the security against ransomware attacks, they can count on IntelligenceX's capability of threat intelligence, threat-hunting services for pinpointing CyberVolk infrastructure within their networks, and managed detection services that keep an eye on ransomware indicators round the clock. By collaborating with cybersecurity service providers like IntelligenceX that are renown for their expertise, companies are able to turn their general awareness of threats into substantial improvements in operational security that significantly reduce the probability of ransomware compromises and at the same time make it possible to recover quickly when incidents occur.

Conclusion: The Continuing Threat Despite Implementation Failures
The finding of the VolkLocker hard-coded master key flaw indicates that even the most advanced ransomware attacks have major implementation problems when they are run by people who care more about getting money quickly than about the technical side of things. The VolkLocker hard-coded decryption key leak gives an excellent chance to the victims to get back the stolen data without paying the ransom, which might put CyberVolk's RaaS business model to the test.
Nonetheless, the detection of the vulnerability should not cause a decline in the level of vigilance of organizations with respect to the ransomware threats. CyberVolk is very likely to fix the cryptographic implementation error in the coming releases and the risks that are inherent to ransomware infection such as data encryption, operational disruption, regulatory breach notification requirements and reputational damage will stay the same. Organizations need to completely eliminate the chances of being infected by VolkLocker by implementing a combination of comprehensive endpoint protection, behavioral monitoring, and rapid incident response capabilities, instead of relying on the criminals' operational failures for recovery. Ransomware is still evolving and becoming more and more accessible through RaaS platforms, which means that the organizational defenses need to improve along with the threats in order to be able to effectively maintain the protection against the persistent threats.