CVE-2025-14847 (MongoBleed): The Critical MongoDB Memory Leak Affecting 87,000+ Servers
Comprehensive analysis of CVE-2025-14847 (MongoBleed), a critical unauthenticated memory leak in MongoDB affecting 87,000+ internet-exposed servers. Explore technical mechanics, exploitation techniques, detection strategies, and search dorks for identifying vulnerable instances.
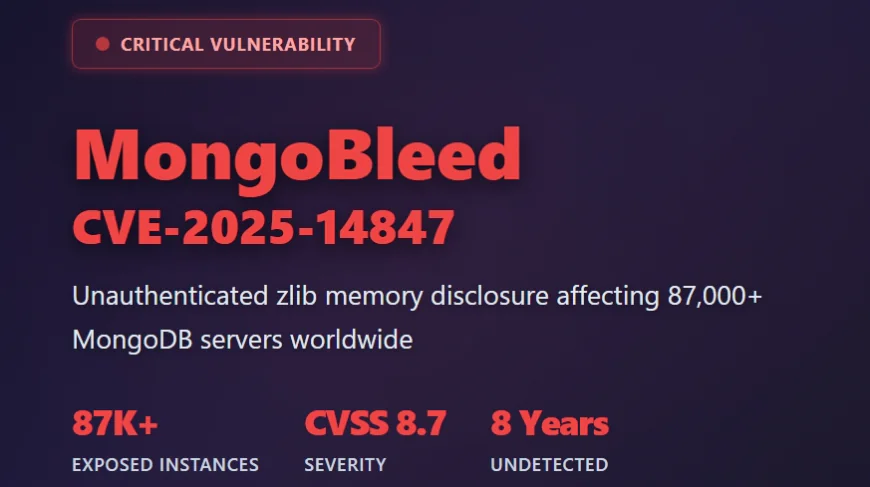
On December 19, 2025, security researcher Joe Desimone disclosed a vulnerability that would ripple through the database world. CVE-2025-14847, nicknamed MongoBleed in a deliberate reference to HeartBleed, exposed a fundamental flaw in how MongoDB handles compressed network messages. The vulnerability scored 8.7 on the CVSS scale, landing squarely in critical territory.
What makes MongoBleed particularly terrifying is its simplicity and scope. Unlike complex exploits requiring multiple steps or special conditions, this vulnerability is trivial to trigger. More importantly, it requires no authentication whatsoever. An attacker on the internet can extract uninitialized heap memory from a vulnerable MongoDB server without providing any credentials.
By December 27, just eight days after disclosure, security research firm Censys had identified 87,000 potentially vulnerable MongoDB instances exposed on the public internet. Wiz's telemetry data showed that 42 percent of cloud environments contain at least one vulnerable MongoDB instance. A public proof-of-concept exploit became available on December 26, and exploitation in the wild was reported within hours.
The numbers don't lie. This is a widespread, easily exploitable, actively targeted vulnerability affecting millions of data records globally.
Understanding MongoDB and Zlib Compression
To understand the vulnerability, you need to understand why MongoDB uses compression in the first place.
MongoDB communicates using a wire protocol where clients send queries and servers send responses. As data volumes grow, network bandwidth becomes a bottleneck. To optimize performance, MongoDB supports optional compression of network messages using the zlib library, which implements the DEFLATE compression algorithm.
When compression is enabled, which is often the case in production environments for performance optimization, MongoDB wraps messages in a special compression frame. This frame contains metadata including the original message length before compression. The receiving server uses this metadata to know how large a buffer to allocate for decompression.
This is where the vulnerability lives.
The Technical Mechanics: Out-of-Bounds Memory Read
The vulnerability stems from how MongoDB handles inconsistencies between the claimed uncompressed message size and the actual decompressed data.
Here's what happens during normal operation:
An attacker sends a specially crafted OP_COMPRESSED message to the MongoDB server. This message claims in its header that the uncompressed payload will be 10,000 bytes. MongoDB allocates a 10,000-byte buffer. The attacker provides actual zlib-compressed data that decompresses to only 100 bytes. Zlib decompresses the data, filling the first 100 bytes of the allocated 10,000-byte buffer. The remaining 9,900 bytes of the buffer remain uninitialized, containing whatever data was previously allocated in that memory region.
Here's the critical flaw: MongoDB's code treats the entire allocated buffer as valid decompressed data, not just the portion actually filled by decompression. When BSON parsing begins on this buffer, the parser reads beyond the decompressed data boundary into uninitialized heap memory. The server returns this uninitialized memory in error messages or responses, and the attacker receives heap data containing fragments of previous database operations, session tokens, credentials, API keys, internal pointers, and more.
The vulnerability exists in the file message_compressor_zlib.cpp within MongoDB Server. The affected code returned output.length() (the allocated buffer size) instead of the actual decompressed data length when processing the OP_COMPRESSED opcode. This length mismatch is the entire attack surface.
Critically, this flaw exists before authentication. The zlib decompression path is executed on incoming messages prior to authentication checks. An unauthenticated attacker can trigger this code path immediately upon connection without providing any credentials.
Affected Versions and Timeline
The vulnerability's historical scope is shocking. The original commit introducing the bug was merged on June 1, 2017. This means some MongoDB instances have contained this vulnerability for nearly eight years without anyone discovering it.
Affected versions include:
Version 8.2.0 through 8.2.2
Version 8.0.0 through 8.0.16
Version 7.0.0 through 7.0.27
Version 6.0.0 through 6.0.26
Version 5.0.0 through 5.0.31
Version 4.4.0 through 4.4.29
All MongoDB Server v4.2, v4.0, and v3.6 versions
The timeline of disclosure and patching was chaotic:
✅ June 1, 2017: The vulnerable code was committed and merged into MongoDB's codebase
✅ December 17, 2025: The fix code was written by MongoDB engineers
✅ December 19, 2025: The CVE was officially published
✅ December 22, 2025: The fixed code was merged into MongoDB's repository
✅ December 24, 2025: MongoDB announced that all Atlas (cloud-hosted) databases were patched
✅ December 26, 2025: Public proof-of-concept code became available
✅ December 27 2025: Active exploitation reported in the wild
The gap between CVE publication and MongoDB's public disclosure was five days. During this window, MongoDB Atlas customers were protected through automatic patching, but self-hosted instances remained vulnerable. The company stated there is no workaround, only patching or disabling zlib compression entirely.
How the Exploitation Works in Practice
Understanding exploitation requires understanding what an attacker actually receives from the vulnerability.
An attacker connects to a vulnerable MongoDB server and immediately sends a malformed OP_COMPRESSED message before authentication. The message claims an uncompressed size of 8,192 bytes but contains only a small amount of actual compressed data. MongoDB allocates the 8,192-byte buffer, decompresses the minimal actual data into it, and treats the entire buffer as valid message content.
When BSON parsing processes this "message," it encounters the actual decompressed data followed by uninitialized heap memory. The parser attempts to interpret this memory as BSON field names and values. It reads bytes sequentially until encountering a null terminator. This process extracts whatever was previously allocated in that memory region.
A successful attack might reveal:
✅ Session authentication tokens and credentials from previous connections
✅ API keys and secrets stored in memory
✅ Password hashes from database operations
✅ Internal configuration data and IP addresses
✅ Fragments of previous queries and data operations
✅ System information and memory statistics
✅ Database connection parameters and internal infrastructure details
The public proof-of-concept exploit demonstrates this by probing different offsets within the heap. By sending thousands of requests with different memory offset targets, an attacker systematically reconstructs larger portions of heap memory. The PoC can generate over 8,700 bytes of leaked data across 42 separate fragments in a single exploitation session.
The attack generates distinctive traffic patterns. The PoC exploit generates 50,000 to 100,000+ connections per minute to a single target. Each connection lasts only seconds as the attacker extracts a memory chunk and disconnects. Legitimate MongoDB drivers never operate this way.
Search Dorks: Finding Vulnerable Instances
Security researchers and malicious actors alike are actively hunting for vulnerable MongoDB instances using search engines and specialized scanning platforms. Here are the search dorks being used:
Shodan Search Queries
Find exposed MongoDB instances using Shodan:
```
port:27017 MongoDB product:"MongoDB"
```
Find specifically vulnerable MongoDB versions:
```
port:27017 MongoDB version:8.0.
port:27017 MongoDB version:7.0.
port:27017 MongoDB version:6.0.
```
Find MongoDB instances with specific banners:
```
port:27017 "MongoDB" "zlib"
```
Combine with geographic filters:
```
port:27017 MongoDB country:US
```
Find MongoDB instances that respond to specific commands:
```
port:27017 "ismaster" OR "isMaster"
```
Google Dork Queries
Find potentially vulnerable MongoDB documentation or configuration pages:
```
site:mongodb.com zlib compression OR OP_COMPRESSED
"MongoDB" filetype:conf zlib
"mongodb.conf" zlib compression
```
Find exposed configuration or deployment information:
```
site:github.com MongoDB zlib vulnerability
site:*.amazonaws.com "mongodb" port:27017
```
Find MongoDB instances on cloud providers:
```
site:*.azurewebsites.net mongodb
site:*.herokuapp.com mongodb OR mongo
```
Censys Search
Censys provides more granular protocol analysis:
```
services.service_name:"MongoDB"
services.service_name:"MongoDB" AND services.mongodb.version:"8.0"
services.service_name:"MongoDB" AND location.country:"US"
```
BinaryEdge
BinaryEdge provides detailed service information:
```
"service":"mongodb"
"service":"mongodb" AND "version":"8.0"
ZoomEye
ZoomEye's search syntax for MongoDB:
```
service:mongodb
service:mongodb version:7.0
service:mongodb asn:AS15169
```
Detection: Identifying Active Exploitation
The challenge for defenders is that exploitation generates distinctive patterns that can be detected with proper logging.
The single most important indicator of MongoBleed exploitation is a massive spike in connection attempts. The PoC generates 50,000 to 100,000+ connections per minute. This is extremely unusual for MongoDB, which typically sees steady-state connection counts in the hundreds or thousands at most.
Legitimate MongoDB drivers always send client metadata immediately after connecting. The metadata includes driver name, version, operating system, application name, and other identifying information. MongoDB logs this as event ID 51800 in JSON logs. Crucially, the MongoBleed PoC never sends this metadata. It connects, probes for memory, and disconnects without metadata.
This creates a perfect detection signature: Connections without metadata at abnormally high velocity.
MongoDB generates specific error logs when receiving malformed messages. The errors include InvalidBSON errors with messages like "incorrect BSON length in element with field name." A spike of over 1,000 such errors within a short time window is virtually diagnostic of MongoBleed exploitation.
Defenders should implement the following logging and alerting:
Enable JSON logging on all MongoDB instances to capture connection and metadata events
Monitor for connection velocity spikes exceeding 1,000 connections per minute from single source IPs
Alert on patterns of connections without client metadata (event ID 51800)
Alert on spikes of InvalidBSON errors exceeding 1,000 occurrences within 5-minute windows
Correlate high-velocity connections with InvalidBSON errors for confirmed exploitation
Implement time-windowed aggregation to avoid false positives from legitimate connection pools
Log the source IP of all exploitation attempts for incident response and threat intelligence
Security researcher Eric Capuano developed a Velociraptor artifact called Linux.Detection.CVE202514847.MongoBleed that automates this detection logic, parsing MongoDB JSON logs and calculating the metadata rate for each source IP over configurable time windows.
Vulnerable Data and Real-World Impact
The specific data exposed by MongoBleed depends entirely on what MongoDB instances contain and what happens to be in heap memory at the moment of exploitation.
In financial services, MongoDB instances contain transaction records, account numbers, balances, and customer PII. Heap memory might reveal session tokens for administrative accounts, API keys for third-party financial services, or encryption keys.
In healthcare systems, MongoDB stores patient records with names, dates of birth, medical histories, and treatment information. Exploitation could expose de-identification tokens or encryption keys that unlock patient privacy.
In SaaS applications, MongoDB contains user account data, authentication credentials, API keys for integrated services, and sometimes source code or configuration secrets accidentally stored in databases.
The nature of heap memory is that it contains fragments rather than complete records. An attacker might extract partial API keys, session tokens with missing bytes, or database credentials with characters missing. However, even fragmentary information combined across hundreds of exploitation attempts can often be reconstructed or used for lateral movement.
A single production MongoDB instance might handle millions of queries daily. The heap memory contains fragments from all of these operations. An attacker conducting sustained exploitation over hours or days can accumulate enormous amounts of data.
Immediate Mitigation and Patching
MongoDB released patched versions on December 19, 2025:
✅ Version 8.2.3 and later
✅ Version 8.0.17 and later
✅ Version 7.0.28 and later
✅ Version 6.0.27 and later
✅ Version 5.0.32 and later
✅ Version 4.4.30 and later
All organizations must upgrade to these patched versions immediately. Patching should take priority over normal maintenance windows given the severity and active exploitation.
MongoDB Atlas customers received automatic patching and need no action. Self-hosted instances and containerized deployments must be patched manually.
If immediate patching is impossible due to operational constraints, MongoDB recommends disabling zlib compression entirely. This removes the attack vector while systems are being upgraded. To disable zlib compression, start MongoDB with the following configuration:
mongod with the net.compression.compressors option set to exclude zlib, or using command line argument --networkMessageCompressors without zlib specified.
Restricting network access to MongoDB instances to only trusted IPs is another essential mitigation. MongoDB should never be exposed to untrusted networks without authentication and encryption. Use firewall rules to restrict access to a whitelist of known application servers.
Enable verbose JSON logging to detect exploitation attempts. Monitor for the specific patterns described above indicating active attacks.
Incident Response and Forensics
Organizations discovering evidence of exploitation should immediately:
✅ Isolate affected MongoDB instances from the network to prevent further data exfiltration
✅ Preserve MongoDB logs for forensic analysis, including connection logs and query logs
✅ Identify the source IP addresses of exploitation attempts for threat intelligence and law enforcement reporting
✅ Analyze heap memory dumps if available to determine what data was exposed
✅ Audit access logs and application logs for signs of secondary compromise using stolen credentials
✅ Reset all administrative credentials and API keys
✅ Rotate encryption keys that might have been exposed
✅ Conduct vulnerability scanning of network segments containing the MongoDB instance
✅ Review firewall and network access control rules to determine how the instance became internet-exposed
✅ Implement network segmentation to prevent MongoDB from being directly exposed in the future
Document the incident for compliance and regulatory reporting requirements
The Bigger Picture: MongoDB Security and Database Hardening
MongoBleed is a wake-up call for organizations using MongoDB in production. The vulnerability has existed for eight years without detection, suggesting that many organizations lack visibility into the security posture of their databases.
Best practices for MongoDB deployment include:
✅ Never expose MongoDB directly to the internet. Always place it behind application servers with firewall restrictions.
✅ Enforce authentication on all MongoDB instances using strong credentials.
✅ Use network segmentation and VPCs to restrict database access to authorized applications.
✅ Enable encryption in transit and at rest.
✅ Implement database activity monitoring and audit logging.
✅ Conduct regular security assessments and penetration testing of database infrastructure.
✅ Monitor for unusual connection patterns or query behavior.
✅ Keep MongoDB updated to the latest stable version.
✅ Implement principle of least privilege for database user accounts.
✅ Backup critical databases regularly with encrypted backup storage.
✅ Regular security training for operations and development teams.
Conclusion: The Urgency of Patching
CVE-2025-14847 represents one of the most critical database vulnerabilities discovered in recent years. It combines easy exploitation, unauthenticated access, widespread affected infrastructure, and real-world data exposure risks.
The fact that 87,000+ internet-exposed instances remain vulnerable days after patching demonstrates that many organizations either haven't yet deployed patches or remain unaware of the vulnerability's existence. This window of vulnerability is precisely when attackers are most active, systematically scanning for and exploiting exposed instances.
If you operate MongoDB in any capacity, this is an emergency. Patch immediately. Disable zlib compression if patching is delayed. Restrict network access. Enable logging and monitoring. Assume that if your instance was internet-exposed with compression enabled, it has been scanned at minimum.
The MongoDB community dodged a massive bullet with this vulnerability being discovered and disclosed responsibly. Now it's up to organizations worldwide to perform the unglamorous work of patching, monitoring, and hardening their infrastructure before attackers compromise critical systems.