A07:2025 - Authentication Failures: The Identity Crisis Threatening Modern Applications
Authentication failures occur when applications allow attackers to compromise passwords, keys, session tokens, or exploit implementation flaws to assume users' identities. From credential stuffing and brute force attacks to session hijacking and weak password recovery mechanisms, these vulnerabilities enable unauthorized access that bypasses all other security controls. This article provides security professionals and development teams with an in-depth analysis of authentication attack vectors, the emerging threat of hybrid credential stuffing attacks, and the paradigm shift toward passwordless authentication using FIDO2 passkeys that achieve 30% higher sign-in success rates and 73% faster authentication times.
Understanding Authentication Failures in 2025
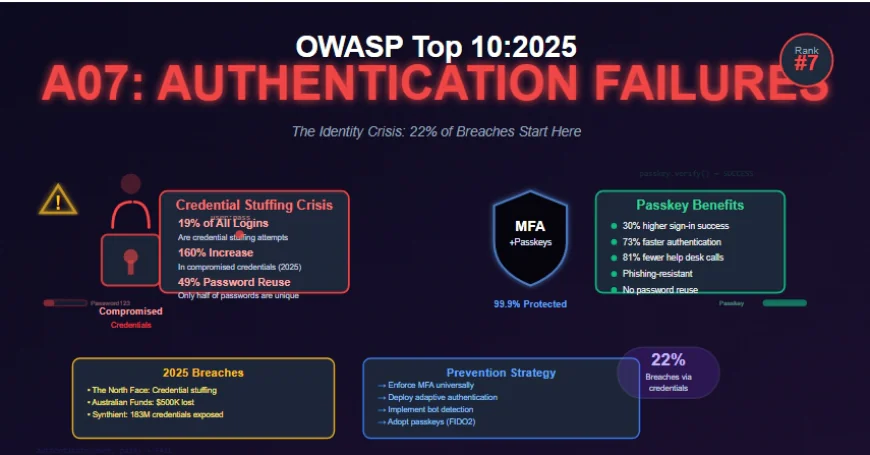
Authentication Failures maintains its position at number seven in the OWASP Top 10:2025, with a slight name change from "Identification and Authentication Failures" to more accurately reflect the 36 Common Weakness Enumerations in this category. Despite the stable ranking from 2021, the authentication landscape has deteriorated dramatically, with attacks becoming more sophisticated, automated, and successful.
When an attacker is able to trick a system into recognizing an invalid or incorrect user as legitimate, this vulnerability is present. Confirmation of the user's identity, authentication, and session management is critical to protect against authentication-related attacks. The category includes notable CWEs such as CWE-259 Use of Hard-coded Password, CWE-297 Improper Validation of Certificate with Host Mismatch, CWE-287 Improper Authentication, CWE-384 Session Fixation, and CWE-798 Use of Hard-coded Credentials.
The statistics paint a stark picture of the authentication crisis. According to the 2025 Verizon Data Breach Investigations Report, compromised credentials were an initial access vector in 22% of breaches. More alarmingly, credential stuffing accounted for 19% of all authentication attempts in the median case, rising to 25% in enterprise-sized companies while small businesses experience it at 12%. Recent reports suggest the volume of compromised credentials has shot up by 160% so far in 2025, giving hackers more access to stolen data than ever before.
The Credential Stuffing Epidemic
Credential stuffing has evolved from a blunt brute-force tactic into a precision weapon that represents one of the most persistent and successful attack vectors against modern applications.
- What is Credential Stuffing?
- Credential stuffing is the automated injection of stolen username-password pairs into login forms to gain unauthorized access. The key word is stolen, not guessed. Attackers reuse credentials from previous breaches, knowing full well how common password reuse is. Infostealer malware infection data shows that in the median case, only 49% of a user's passwords across different services were distinct from each other.
- The attack leverages automation and scale. Attackers use lists of compromised credentials called ComboLists, often collected, shared, and sold in marketplaces or cybercrime-related Telegram channels. These lists are tested en masse against numerous websites with the assumption that many users reuse usernames and passwords across multiple services. Even a 1-3% success rate is catastrophic when firing millions of attempts per day.
- The Mechanics of Modern Credential Stuffing
- Credential stuffing has evolved into a stealth, data-driven identity threat that slips past traditional perimeters. Attackers now use sophisticated bot frameworks to mimic real user behavior by rotating IP addresses through residential proxies, spoofing device fingerprints, and leveraging custom configuration files that detail the authentication endpoint being targeted along with any associated headers.
- These configurations are fine-tuned for specific login flows to defeat each company's unique defenses. Many have custom configs built for business logic manipulation and API exploitation. Over 100 threat scripts published between late 2024 and mid-2025 showed these trends becoming standard practice.
- Artificial intelligence has become a co-conspirator. Attackers use AI agents to optimize credential selection, adapt login flows in real-time, and predict which accounts are most likely to reuse passwords. Machine learning models analyze previous successes and re-target high-value domains, trimming away wasted attempts and maximizing payoff. The result is fewer brute-force floods and more quiet infiltrations that look legitimate until it's too late.
- Hybrid Credential Stuffing: The Evolution
- More recently, this type of attack has been expanded to include hybrid password attacks credential stuffing, also known as password spray attacks, where the attacker uses variations or increments of spilled credentials to gain access. For instance, attackers try Password1!, Password2!, Password3! systematically, or adjust passwords based on common human behavior like changing Winter2025 to Winter2026, or ILoveMyDog6 to ILoveMyDog7 or ILoveMyDog5.
- This adjusting of password attempts makes hybrid credential stuffing attacks even more effective than traditional versions because they exploit predictable human password creation patterns rather than requiring exact matches from breach databases.
- Why Credential Stuffing Works
- Given that these types of attacks will only try to authenticate once against a specific user account and can hide their attack by modifying headers, they are often successful in hiding amongst regular authentication traffic. There are two main weaknesses that enable credential stuffing attacks to be successful: password reuse across services, and the lack of robust automated threat detection.
- According to authentication logs from SSO providers, credential stuffing is everywhere. Some folks might think their users aren't at risk, but there's actually a wide variety of different organizations being targeted—it's not just the major streaming platforms that need to worry. By the powers of automation and scale, it likely costs very little to an attacker to simply try each password against numerous websites.
Real-World Attacks in 2025
The consequences of authentication failures extend far beyond theoretical vulnerabilities, with devastating real-world impacts throughout 2025.
- The North Face Data Breach (April 2025)
- On April 23, 2025, The North Face website was targeted by a credential stuffing campaign using previously leaked credentials. The attacker gained access to customer accounts and exposed data including names, email addresses, shipping addresses, phone numbers, purchase history, and dates of birth. While no payment card data was compromised since the company uses third-party processors, this marked the fourth credential stuffing incident affecting VF Corporation brands since 2020.
- Australian Superannuation Fund Attacks (March 2025)
- Multiple Australian retirement funds—including AustralianSuper, Rest Super, Hostplus, Australian Retirement Trust, and Insignia Financial—detected coordinated credential stuffing attempts over March 29-30, 2025. Although most funds repelled the attacks, some members of AustralianSuper lost a combined AUD $500,000, and approximately 8,000 Rest Super members had personal data accessed. The attacks demonstrated that even financial institutions with presumably strong security can be vulnerable to credential-based attacks.
- Roku Credential Stuffing (2024)
- Over 500,000 Roku accounts were compromised through credential stuffing attacks in 2024. Attackers used stolen credentials to access user accounts, demonstrating the scale at which these attacks can successfully compromise systems when users reuse passwords across services.
- Norton Password Manager Breach
- Even security companies themselves aren't immune. Norton—a company literally in the security business—had to notify thousands of users because attackers were stuffing stolen credentials into their password manager vaults. This ironic breach highlighted that no organization is safe from credential-based attacks.
- The Synthient Stealer Log (2025)
- The Synthient Stealer log for 2025 exposed nearly 183 million unique email addresses with associated passwords. The dataset meticulously captured each credential pair—email addresses linked explicitly to websites where they were entered and the exact passwords used. After normalization and deduplication, the final count stood at 182,962,095 breached accounts, creating a vast landscape of compromised identities vulnerable to exploitation.
- The data was integrated into Have I Been Pwned, making it searchable and demonstrating the scale of credential exposure available to attackers in 2025.
Common Authentication Weaknesses
Applications may have authentication weaknesses if they exhibit any of the following characteristics.
- Automated Attacks Without Defense
- The application permits automated attacks such as credential stuffing, where the attacker has a breached list of valid usernames and passwords. If an application does not implement defenses against automated threats—brute force, scripts, or bots—or credential stuffing protection, the application can be used as a password oracle to determine if credentials are valid and gain unauthorized access.
- Weak Password Practices
- The application permits default, weak, or well-known passwords such as Password1 or admin/admin. It uses weak or ineffective credential recovery and forgot-password processes, such as knowledge-based answers, which cannot be made safe according to NIST 800-63b, OWASP ASVS, and OWASP Top 10 guidance.
- Organizations often encourage what were once considered best practices: password rotation and complexity requirements. However, these practices actually encourage users to both reuse passwords and use weak passwords. Most successful authentication attacks occur due to the continued use of passwords as the sole authentication factor.
- Cryptographic Failures in Password Storage
- The application uses plain text, encrypted, or weakly hashed passwords in data stores. This connects directly to A04:2025 Cryptographic Failures. Without proper password hashing using algorithms like Argon2id, bcrypt, or scrypt with appropriate work factors, password databases become treasure troves for attackers who gain database access.
- Missing or Ineffective Multi-Factor Authentication
- The application has missing or ineffective multi-factor authentication, or allows use of weak or ineffective fallbacks if multi-factor authentication is not available. Once considered optional, MFA has moved from being a recommended option to an essential safeguard. Yet many applications still don't require it, or implement it poorly with weak second factors like SMS that can be intercepted.
- Session Management Failures
- The application exposes session identifiers in URLs, hidden fields, or other insecure locations accessible to clients. It reuses the same session identifier after successful login rather than generating a new one. It does not correctly invalidate user sessions or authentication tokens (mainly single sign-on tokens) during logout or after a period of inactivity.
- Application session timeouts represent a common vulnerability. A user uses a public computer to access an application and instead of selecting logout, simply closes the browser tab and walks away. An attacker using the same browser later finds the user still authenticated. Another example involves Single Sign-On sessions that cannot be closed by Single Logout—a single login logs you into your mail reader, document system, and chat system, but logging out only affects the current system.
- Inadequate Scope Verification
- The application does not correctly assert the scope and intended audience of provided credentials. For JSON Web Tokens, this means failing to validate aud (audience), iss (issuer) claims, and scopes. Without proper validation, tokens can be misused across different services or contexts.
The Financial and Operational Impact
The consequences of authentication failures extend beyond technical compromises to severe business impacts.
- Direct Financial Losses
- The global average cost of a data breach reached $4.45 million in 2023, with credential-based breaches often at the high end. Direct financial losses from credential stuffing include refunds, chargebacks, gift card laundering, and loyalty point restitution. According to recent industry reports, compromised credentials are involved in a huge chunk of all breaches, and the average cost is a staggering $4.81 million.
- Operational Disruption
- Operational drag includes help desk queues surging with lockouts and forced resets. Peak credential stuffing events can triple call volume, driving overtime costs or SLA penalties. Authentication costs mount as organizations send OTP codes, process password resets, and handle support tickets.
- Reputation and Trust Damage
- Frequent or high-profile breaches caused by authentication failures severely damage an organization's reputation, causing customers to lose trust and seek more secure alternatives. This long-term impact hurts revenue and market position far beyond immediate incident response costs.
- Regulatory and Compliance Violations
- Failing to implement proper authentication controls increases the risk of non-compliance with regulatory standards like GDPR, PCI-DSS, HIPAA, and others. This leads to additional penalties, legal fees, and enforcement actions that compound financial losses.
- Intellectual Property Theft
- Unauthorized access to internal systems through compromised credentials allows attackers to steal proprietary data, including trade secrets or intellectual property, potentially giving competitors an unfair advantage and causing long-term competitive damage.
Prevention: Building Robust Authentication
Preventing authentication failures requires a comprehensive, defense-in-depth approach combining multiple complementary security controls.
- Implement Multi-Factor Authentication
- Where possible, implement and enforce use of multi-factor authentication to prevent automated credential stuffing, brute force, and stolen credential reuse attacks. MFA adds an extra layer of security by requiring two or more forms of verification before granting account access. After entering your password, you may be prompted to provide a code sent to your phone, respond to an app notification, or use another authentication method.
- MFA significantly reduces the risk of unauthorized account access even if your password is compromised. When you combine SSO with MFA, you're stopping 99.9% of automated attacks in their tracks according to OWASP guidelines and industry research.
- Adopt Passkeys for Phishing-Resistant Authentication
- Passkeys represent the future of authentication, eliminating passwords entirely. Passkeys are phishing-resistant credentials based on public-key cryptography, offering a secure and user-friendly alternative to passwords. They eliminate the shared-secret model of passwords, so there's nothing that can be shared or stolen in a breach.
- Passkeys use FIDO2 and WebAuthn standards to create device-bound or synced credentials. Device-bound passkeys (security keys) are physical devices like YubiKeys used as authentication factors. Synced passkeys use credential managers from providers like Google, Apple, Microsoft, 1Password, Dashlane, and Bitwarden, leveraging built-in biometric authenticators like Touch ID on MacBooks or Face ID on phones.
- Organizations implementing passkeys report significant benefits. According to the FIDO Alliance Passkey Index, platforms using passkeys report up to 81% reduction in sign-in related help desk incidents. Companies surveyed by FIDO and Liminal showed 30% higher sign-in success rates compared to other MFA methods and 73% reduction in sign-in time (8.5 seconds average versus 31.2 seconds for other methods).
- Major cloud providers have embraced passkeys. AWS now supports passkey multi-factor authentication for root and IAM users across all regions. Microsoft Entra ID supports passkeys in Authenticator for Android 14+ and iOS 17+. Snowflake added passkey support in May 2025. The momentum behind passkeys is undeniable, with 63% of IT professionals surveyed ranking passkeys as their top authentication investment priority for 2026.
- Implement Adaptive and Risk-Based Authentication
- Rather than applying static MFA challenges to every login, implement adaptive authentication that evaluates risk factors such as device type, user behavior patterns, login frequency, historical access locations, and impossible travel scenarios. Anomalous login attempts—such as a sudden login from an unusual country or multiple failed attempts followed by success—should trigger additional verification steps dynamically.
- This approach provides frictionless authentication for legitimate users while automatically increasing security barriers for suspicious attempts. Legitimate users experience one-click logins while attackers face escalating challenges that make attacks uneconomical.
- Deploy Advanced Bot Detection
- Credential stuffing attacks rely on bots to perform high volumes of login attempts. Utilize bot detection solutions such as device fingerprinting, browser behavior analysis, machine learning-trained anomaly detection, and behavioral biometrics to distinguish between human users and automated traffic.
- Blocking or rate-limiting suspicious login activity based on such analysis is essential for reducing credential stuffing success rates. Anomaly analysis can detect subtle variations in login behavior like unusual access locations, odd sign-in times, or simultaneous logins from multiple IPs.
- Enforce Strong Password Policies
- While passwords remain necessary during the transition to passwordless authentication, organizations must enforce modern, evidence-based password policies. Do not ship or deploy with any default credentials, particularly for admin users. Implement weak password checks, testing new or changed passwords against lists of known breached credentials using services like Have I Been Pwned.
- Align password length, complexity, and rotation policies with NIST 800-63b guidelines in section 5.1.1 for Memorized Secrets. Modern guidance recommends longer passwords without forced complexity requirements or mandatory rotation, as these practices encourage weak, reused passwords. Do not force human beings to rotate passwords unless you suspect a breach.
- Where possible, encourage and enable the use of password managers to help users make better choices. Password managers generate and store strong, unique passwords for each service, eliminating password reuse—the primary weakness enabling credential stuffing.
- Implement Rate Limiting and Account Lockout
- Limit or increasingly delay failed login attempts, but be careful not to create a denial of service scenario. Implement exponential backoff so that each successive failed attempt increases wait time. After a threshold of failures, temporarily lock the account or require additional verification.
- Log all failures and alert administrators when credential stuffing, brute force, or other attacks are detected or suspected. These logs provide visibility into attack patterns and enable proactive response.
- Secure Session Management
- Use a server-side, secure, built-in session manager that generates a new random session ID with high entropy after login. Session identifiers should not be in the URL, must be securely stored in secure cookies with HttpOnly, SameSite, and Secure flags, and must be invalidated after logout, idle timeouts, and absolute timeouts.
- Implement continuous session analytics after authentication. Watch for impossible travel (access from geographically distant locations within impossibly short timeframes), sudden privilege escalation, off-hours API abuse, or other anomalous session behavior. Evict suspicious sessions instantly rather than waiting for the next login attempt.
- Credential Screening and Breach Monitoring
- Compare email addresses and usernames against breach corpora at account creation and login. Services like Have I Been Pwned provide APIs for checking whether credentials appear in known breaches. When detected, require users to reset passwords before proceeding, or shift them to passkey enrollment to eliminate the vulnerability entirely.
- Monitor dark web marketplaces and breach databases for your organization's domains. When employee or customer credentials appear in breaches of other services, proactively require resets to prevent credential stuffing attacks before they occur.
- Secure Password Recovery Flows
- Harden password reset and email-change requests with the same adaptive policy used for authentication. These recovery flows are often the weakest link, allowing attackers to compromise accounts after they've been secured. Avoid knowledge-based answers which NIST, OWASP ASVS, and OWASP Top 10 explicitly prohibit as insecure.
- Use multi-channel verification for sensitive account changes. Require email confirmation plus SMS or authenticator app verification before allowing password resets or email address changes. This prevents re-compromise moments after cleanup.
- Use Established Authentication Systems
- Ideally, use a premade, well-trusted system to handle authentication, identity, and session management. Transfer this risk whenever possible by buying and utilizing a hardened and well-tested system. Established solutions like Auth0, Okta, AWS Cognito, Azure AD, and others have invested enormous resources in securing authentication flows that most organizations cannot replicate internally.
- These systems provide battle-tested implementations of authentication best practices, regular security updates, and compliance with evolving standards. Building authentication from scratch almost always introduces vulnerabilities that mature solutions have already addressed.
Emerging Authentication Technologies
The authentication landscape continues evolving with new technologies addressing fundamental weaknesses of password-based systems.
- Behavioral Biometrics
- Behavioral biometrics analyze how users interact with applications—typing patterns, mouse movements, touchscreen gestures, and other unique behaviors. These passive checks operate silently in the background, detecting anomalies without adding friction to legitimate users.
- Unlike traditional MFA that requires explicit user action, behavioral biometrics continuously authenticate throughout the session. If behavior suddenly changes mid-session (suggesting account takeover), the system can trigger step-up authentication or session termination.
- Device Trust and Attestation
- Modern authentication systems assess device trust before granting access. Device fingerprinting, hardware attestation, and secure enclave verification ensure that authentication occurs on trusted, uncompromised devices.
- For passkeys, attestation verifies the legitimacy of the authenticator being used. iOS uses App Attest service while Android uses Play Integrity API and key attestation to ensure passkeys are created by legitimate applications on uncompromised devices, not emulators or rooted systems used by attackers.
- Continuous Authentication
- Traditional authentication makes a binary decision at login: trusted or untrusted. Continuous authentication reassesses trust throughout the session based on behavior, context, and risk signals. This prevents scenarios where attackers gain initial access through stolen credentials but then exhibit anomalous behavior that would have been caught by ongoing monitoring.
- The Passwordless Future; Credential stuffing will not disappear until reused passwords do. Passkeys eliminate these costs and attacks by fundamentally changing the authentication model.
- Why Passkeys Solve the Problem
- Breaches of password databases no longer pose a threat when there are no passwords to steal. No reused passwords means no credential stuffing—the attack simply doesn't work. Passkeys use public-key cryptography where the private key never leaves the user's device. Even if an attacker compromises a service's authentication database, they gain nothing useful for accessing accounts.
- According to Gartner analyst James Hoover, the most secure types of authentication are those classed as phishing-resistant MFA, which includes device-bound passkeys. For device-bound FIDO2 keys, there is not currently a proven method of stealing them, as the private key itself does not leave the device.
- Real-World Adoption and Results
- Early adopters report transformative results. Amazon, Google, Microsoft, PayPal, Target, and TikTok participated in confidential surveys showing 30% higher sign-in success rates, 73% reduced sign-in time, and up to 81% fewer sign-in related help desk incidents.
- If you're in the business of selling things or content, easier, faster access leads to increased revenues. Passkeys help consumer-facing businesses eliminate shopping cart abandonment due to people getting frustrated with the time it takes to check out. Organizations also find decreased costs as passkeys reduce help-desk calls, eliminate password reset tickets, and reduce authentication infrastructure costs.
- Of those who have already adopted passkeys, 85% reported strong satisfaction with their decision and the business results seen thus far. The momentum is clear: 63% of IT professionals ranked passkeys as their top authentication investment priority for 2026.
Implementation Roadmap
Organizations shouldn't attempt to transform authentication overnight. A phased approach ensures security improvements without disrupting operations.
- Phase 1: Foundation (Immediate)
- Enable MFA across all user accounts, prioritizing administrators and privileged users. Implement rate limiting on all authentication endpoints. Deploy credential monitoring to detect passwords in known breaches. Harden session management with secure cookies and appropriate timeouts.
- Phase 2: Advanced Controls (0-6 Months)
- Deploy adaptive authentication that adjusts security based on risk signals. Implement bot detection and behavioral analytics. Enable passkey support as an optional authentication method. Integrate with Have I Been Pwned or similar breach monitoring services.
- Phase 3: Passwordless Transition (6-18 Months)
- Actively encourage passkey adoption through user education and incentives. Gradually deprecate weak authentication methods like SMS-based MFA. Implement continuous session monitoring and risk-based step-up authentication. Move toward requiring passkeys for privileged access.
- Phase 4: Password Elimination (18+ Months)
- Make passkeys the default authentication method for new accounts. Begin sunsetting password-based authentication for existing accounts. Eliminate password storage infrastructure. Achieve true passwordless authentication across the organization.
Conclusion
✅ Authentication Failures at position seven in OWASP Top 10:2025 represents not just a technical category but an identity crisis affecting organizations worldwide. With credential stuffing accounting for 19-25% of all authentication attempts, compromised credentials involved in 22% of breaches, and a 160% increase in compromised credential volume in 2025, the authentication landscape has never been more dangerous.
✅ The fundamental problem is clear: passwords are broken. Users reuse them across services, making credential stuffing inevitable. Attackers have industrialized credential theft through infostealers, automated massive testing through sophisticated bots, and AI-optimized their attacks to maximize success rates.
✅ Traditional defenses—strong password policies, rate limiting, even basic MFA—provide incremental improvements but cannot solve the fundamental problem. SMS-based MFA can be bypassed through SIM swapping. TOTP authenticators can be phished. Knowledge-based authentication is explicitly prohibited by modern standards yet still appears in recovery flows.
✅ The solution is a paradigm shift toward passwordless authentication. Passkeys using FIDO2 and WebAuthn standards eliminate the shared secret model entirely. There are no passwords to steal, no credentials to stuff, no phishing attacks to conduct. Early adopters report 30% higher sign-in success rates, 73% faster authentication, 81% reduction in help desk incidents, and 85% satisfaction with the decision.
✅ Major platforms have embraced this future. AWS, Microsoft, Google, Apple, and countless others now support passkeys. Discord, Snowflake, and enterprise platforms are rolling out passkey support. The technology is ready, proven, and delivering results.For security professionals and development teams, the path forward is clear. Implement MFA universally and immediately. Deploy adaptive authentication and bot detection. Enable passkey support as an option. Actively encourage adoption. Gradually deprecate password-based authentication. The journey toward passwordless authentication isn't optional anymore it's survival.
✅ Authentication in 2025 is an identity crisis, but it's also an opportunity. Organizations that embrace passkeys and modern authentication practices will not only defend against current threats but position themselves for a more secure future. Those that cling to password-based authentication will continue suffering breaches, losing customers, and falling behind competitors who've made the shift.









































