Kubernetes Secrets Management Best Practices
Kubernetes (K8s) has revolutionized application deployment, scaling, and orchestration. However, securing sensitive data within clusters remains a challenge. Secrets in K8s—like API keys, database passwords, TLS certificates—are critical for application functionality but are highly sensitive. Improper handling can lead to data breaches, privilege escalation, or cluster compromise. This blog explores practical, industry-proven best practices for managing secrets in Kubernetes environments, ensuring both security and operational efficiency. Introduction Kubernetes (K8s) has revolutionized application deployment, scaling, and orchestration. However, securing sensitive data within clusters remains a challenge. Secrets in K8s—like API keys, database passwords, TLS certificates—are critical for application functionality but are highly sensitive. Improper handling can lead to data breaches, privilege escalation, or cluster compromise. This blog explores practical, industry-proven best practices for managing secrets in Kubernetes environments, ensuring both security and operational efficiency.

Introduction
Kubernetes (K8s) has revolutionized application deployment, scaling, and orchestration. However, securing sensitive data within clusters remains a challenge. Secrets in K8s—like API keys, database passwords, TLS certificates—are critical for application functionality but are highly sensitive. Improper handling can lead to data breaches, privilege escalation, or cluster compromise.
This blog explores practical, industry-proven best practices for managing secrets in Kubernetes environments, ensuring both security and operational efficiency.
1. Understanding Kubernetes Secrets
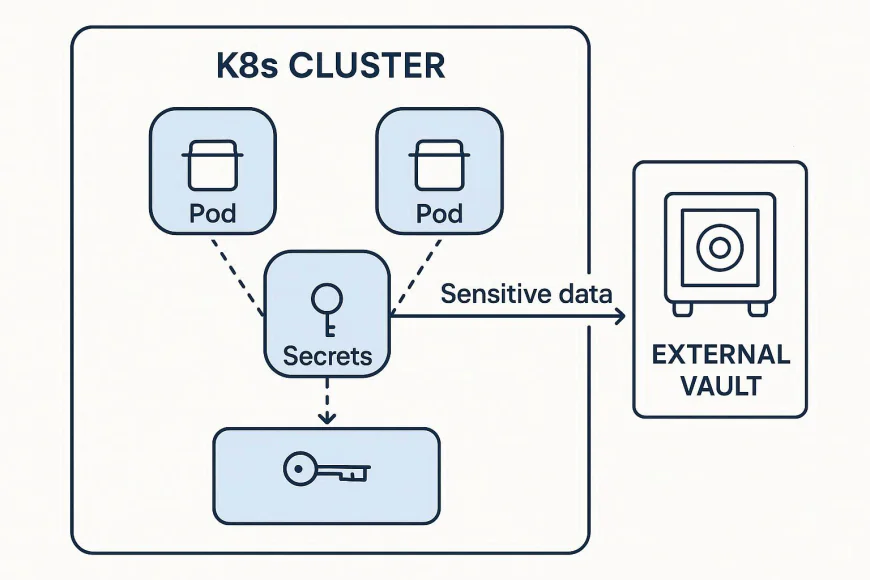
Kubernetes Secrets are objects designed to store sensitive information separately from container images and application code. There are several types:
- Opaque Secrets: Generic secrets storing key-value pairs.
- Docker Registry Secrets: Store credentials for pulling private images.
- TLS Secrets: Certificates and private keys for secure communication.
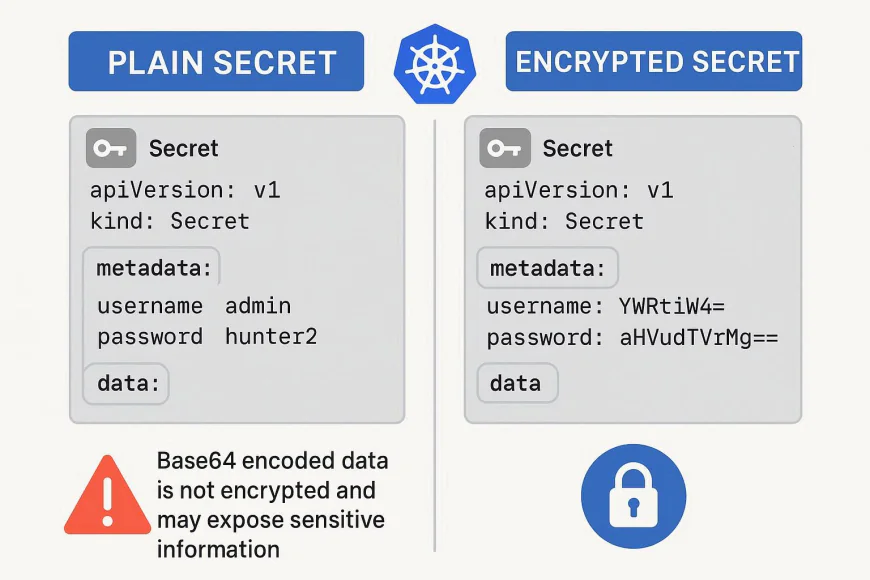
By default, Secrets are base64 encoded, not encrypted. This makes raw etcd access or misconfigured RBAC a potential risk.
Technical Tip:
Always enable encryption at rest for etcd, and restrict access with strict RBAC policies.
2. Best Practices for Managing Secrets in Kubernetes
2.1 Enable Encryption at Rest
- By default, secrets are stored in etcd unencrypted (base64 encoded).
- Enable AES-256 encryption for secrets stored in etcd.
- Update EncryptionConfiguration in the K8s API server.
apiVersion: apiserver.config.k8s.io/v1
kind: EncryptionConfiguration
resources:
- resources:
- secrets
providers:
- aescbc:
keys:
- name: key1
secret:
- identity: {}
2.2 Restrict Access Using RBAC
- Use Role-Based Access Control to ensure only authorized pods or users can read specific secrets.
- Example: limit access for service accounts to required namespaces only.
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: prod
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "list"]
2.3 Avoid Hardcoding Secrets
- Never embed secrets in config maps or container images.
- Use environment variables injected via Secrets or volume mounts.
Technical Insight:
Mounting secrets as files instead of env variables reduces exposure in container runtime logs.
2.4 Integrate External Secret Management Tools
- Consider HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault.
- Benefits: automatic rotation, audit logging, fine-grained access controls, dynamic secrets.
Example Flow:
- Vault generates dynamic DB credentials.
- Kubernetes pod requests credentials via CSI driver.
- Secrets are injected at runtime and never stored in etcd.
2.5 Use Secret Rotation & Expiration
- Rotate secrets regularly to reduce attack windows.
- Integrate rotation into CI/CD pipelines to automatically update deployments without downtime.
2.6 Monitor & Audit Secret Access
- Enable audit logs in Kubernetes API server.
- Monitor access attempts for anomalies and enforce alerting for unauthorized attempts.
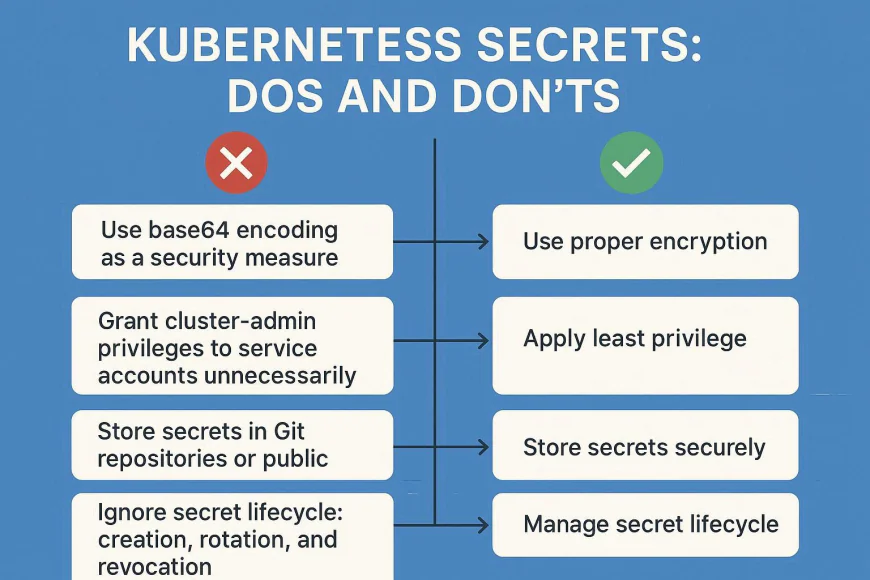
3. Common Mistakes to Avoid
- Using base64 encoding as a security measure.
- Granting cluster-admin privileges to service accounts unnecessarily.
- Storing secrets in Git repositories or public Docker images.
- Ignoring secret lifecycle: creation, rotation, and revocation.
Conclusion
Managing secrets in Kubernetes is critical for secure cluster operations. By following best practices like encryption at rest, RBAC, secret rotation, and integrating external vaults, teams can significantly reduce the attack surface and ensure compliance.
Security should not be an afterthought—it must be embedded into the CI/CD and deployment lifecycle.