After React2Shell: New DoS & Source Code Leaks Hit React Server Components
Just days after React2Shell (CVE-2025-55182), three new vulnerabilities emerged in React Server Components: CVE-2025-55184 and CVE-2025-67779 (CVSS 7.5) enable denial-of-service attacks via infinite loops, while CVE-2025-55183 (CVSS 5.3) leaks server-side source code. The initial patches were incomplete organizations must upgrade again to versions 19.0.3, 19.1.4, or 19.2.3.
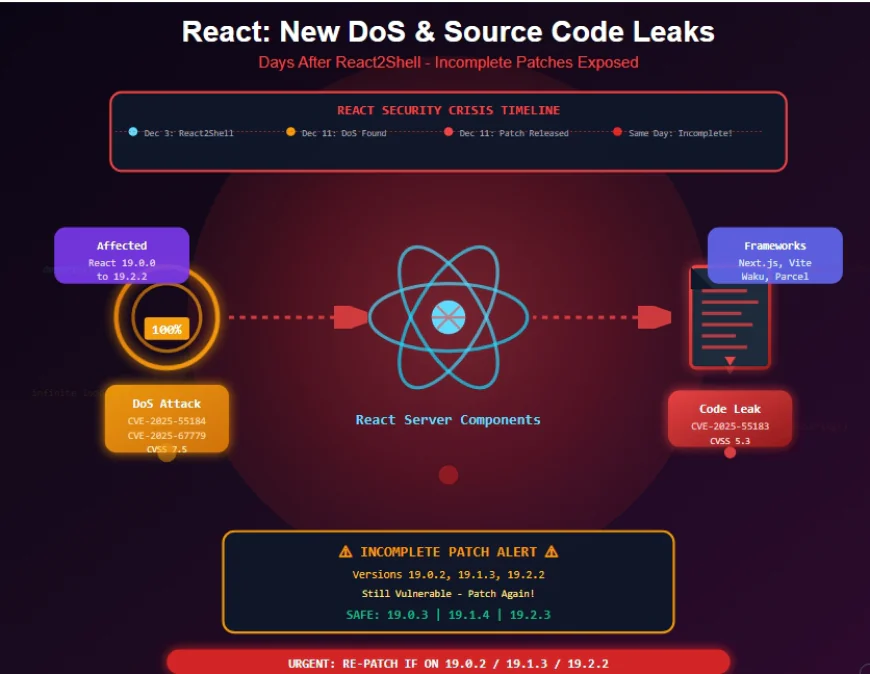
The React security crisis isn't over. Just days after organizations scrambled to patch the critical React2Shell vulnerability (CVE-2025-55182), the React core team disclosed three new vulnerabilities affecting React Server Components—and worse, the initial patches were incomplete, leaving previously "fixed" systems still vulnerable.
On December 11, 2025, the React team released urgent patches for CVE-2025-55184, CVE-2025-67779 (denial-of-service flaws rated CVSS 7.5), and CVE-2025-55183 (source code exposure rated CVSS 5.3). While these vulnerabilities don't enable remote code execution like React2Shell, their impact is serious enough to demand immediate action: service outages and exposure of sensitive source code including API keys and business logic.
What Happened? The Follow-On Discovery Pattern
When a critical vulnerability is disclosed, researchers scrutinize adjacent code paths looking for variant exploit techniques to test whether the initial mitigation can be bypassed. This pattern shows up across the industry, not just in JavaScript.
Following the weaponization of React2Shell, researchers uncovered additional vulnerabilities while analyzing the effectiveness of the initial patches. These newly identified issues do not enable RCE, and the existing fixes successfully block that attack vector. However, they introduce new risks that organizations cannot ignore.
Timeline:
- December 3, 2025: React2Shell (CVE-2025-55182) disclosed
- December 11, 2025: CVE-2025-55184 and CVE-2025-55183 patches published
- December 11, 2025 (same day): Missing DoS case found internally, CVE-2025-67779 disclosed
- Result: Organizations that patched for React2Shell remained vulnerable and needed to patch again
The Three New Vulnerabilities Explained
CVE-2025-55184 & CVE-2025-67779: Denial-of-Service (CVSS 7.5)
Discovery: RyotaK from GMO Flatt Security (CVE-2025-55184); Shinsaku Nomura (CVE-2025-67779)
Security researchers have discovered that a malicious HTTP request can be crafted and sent to any Server Functions endpoint that, when deserialized by React, can cause an infinite loop that hangs the server process and consumes CPU.
Attack Mechanism: A specially crafted HTTP request sent to any App Router endpoint triggers React's deserialization process, leading to an infinite loop. This loop causes the server process to hang and spikes CPU usage to 100%, preventing all future HTTP requests from being served.
Critical Reality: Even if your app does not implement any React Server Function endpoints it may still be vulnerable if your app supports React Server Components. The mere presence of RSC support creates the attack surface.
Impact:
- Single malicious request crashes the entire server
- 100% CPU consumption
- Complete application unavailability
- All legitimate users locked out
- Requires server restart to recover
- Attackers can deny users from accessing the product
- Potential performance impact on shared hosting environments
The Incomplete Fix Problem: The original fix addressing the DoS in CVE-2025-55184 was incomplete. This left versions 19.0.2, 19.1.3, 19.2.2 vulnerable even though they were supposed to be patched. CVE-2025-67779 was filed for these vulnerable "fixed" versions after additional DoS cases were discovered internally on the same day patches released.
CVE-2025-55183: Server-Side Source Code Exposure (CVSS 5.3)
Discovery: Andrew MacPherson
A malicious request can force Server Functions to return the compiled source code of other Server Functions, exposing business logic and any hardcoded secrets.
Technical Explanation: The source code leakage vulnerability apparently was caused by attackers being able to call a ".toString" function over a server function object, this way the values of the server function source code were shown as strings and returned to the attacker.
What Gets Exposed:
- Compiled JavaScript source code of Server Functions
- Business logic and algorithms
- Hardcoded API keys, tokens, and secrets
- Internal endpoint URLs
- Database queries and connection logic
- Authentication and authorization flows
What Stays Protected:
- Runtime environment variables (process.env.SECRET remain safe)
- Variables only accessed at runtime
- Secrets loaded from external configuration
Real-World Risk: If you've ever written something like this in your Server Function:
const API_KEY = "sk-1234567890abcdef";
That key is now exposed to attackers.
Affected Versions: A Broader Range Than You Think
These vulnerabilities are present in the same packages and versions as CVE-2025-55182 (React2Shell), affecting:
Vulnerable React Packages:
- react-server-dom-webpack: 19.0.0 - 19.2.2
- react-server-dom-parcel: 19.0.0 - 19.2.2
- react-server-dom-turbopack: 19.0.0 - 19.2.2
Specifically Vulnerable Versions: 19.0.0, 19.0.1, 19.0.2, 19.1.0, 19.1.1, 19.1.2, 19.1.3, 19.2.0, 19.2.1, 19.2.2
Affected Frameworks:
- Next.js: App Router applications (≥13.3, 14.x, ≥15, ≥16)
- React Router: RSC mode
- Waku
- Vite: RSC plugin
- Parcel: RSC support
- RedwoodSDK
Critical Note: Organizations that upgraded to versions 19.0.2, 19.1.3, or 19.2.2 thinking they were safe from CVE-2025-55184 remained vulnerable and must upgrade again.
The Incomplete Patch Fiasco
This situation highlights a critical problem: the initial fix for CVE-2025-55184 was incomplete, creating a false sense of security.
What Went Wrong:
- CVE-2025-55184 discovered and patched → versions 19.0.2, 19.1.3, 19.2.2 released
- Organizations rushed to upgrade thinking they were protected
- Same day, additional DoS cases discovered internally
- New CVE-2025-67779 filed for the "patched" versions
- Organizations must patch again to actually be secure
Vercel's Strong Warning: "If your application was online and unpatched as of December 4th, 2025 at 1:00 PM PT, we strongly encourage you to rotate any secrets it uses, starting with your most critical ones."
For CVE-2025-55183 specifically, secrets hardcoded in source code should be rotated immediately.
Proof-of-Concept: How the Attacks Work
DoS Attack (CVE-2025-55184/CVE-2025-67779)
Malicious Request Structure:
POST /app-router-endpoint HTTP/1.1
Content-Type: multipart/form-data
[Specially crafted payload that triggers infinite loop in deserialization]
The payload exploits the ReactFlightReplyServer code responsible for handling server responses asynchronously, causing the parsing logic to enter an infinite recursion.
Attack Scenario:
- Attacker identifies any Next.js endpoint using App Router
- Sends crafted HTTP request
- Server begins deserializing the malicious payload
- Infinite loop triggered in React's processing
- CPU maxes at 100%
- Server becomes unresponsive
- All users locked out until manual restart
Source Code Exposure (CVE-2025-55183)
Exploitation Technique:
// Attacker sends specially crafted request that calls:
serverFunction.toString()
// Instead of executing the function, React returns:
"function serverAction() {
const API_KEY = 'sk-1234567890abcdef';
const dbConnection = 'mongodb://admin:password@...';
// ... entire function source code exposed
}"
Fix Implementation: The React team overrode the JavaScript function for server references so whenever the "toString" function is called, it returns an empty function string instead of the original server function code.
Real-World Exploitation Scenarios
Scenario 1: SaaS Platform DoS
A competitor or malicious actor targets a SaaS platform running Next.js:
- Sends single crafted request to public API endpoint
- Entire platform goes down
- Thousands of customers unable to access services
- Revenue loss during downtime
- Reputation damage from service interruption
Scenario 2: API Key Theft via Source Code Leak
E-commerce platform with hardcoded Stripe API keys:
- Attacker exploits CVE-2025-55183
- Retrieves Server Function source code
- Extracts Stripe secret key
- Processes fraudulent transactions
- Exfiltrates customer payment data
- Company faces massive financial and regulatory consequences
Scenario 3: Business Logic Exposure
Fintech application with proprietary algorithms:
- Source code leak reveals trading algorithms
- Competitive advantage lost
- Intellectual property stolen
- Compliance violations (algorithms should be confidential)
Immediate Mitigation: Upgrade Path
The React team released fully patched versions on December 11, 2025.
Upgrade to Fixed Versions
Safe Versions:
- react-server-dom-* 19.0.3
- react-server-dom-* 19.1.4
- react-server-dom-* 19.2.3
Next.js Specific Patches
Patched Next.js Versions:
- 16.0.13
- 15.5.11
- 15.4.12
- 15.3.9
- 15.2.10
- 15.1.13
- 15.0.9
- 14.3.12, 14.4.7
- 13.5.9
Patching Instructions
For React Applications:
# Check current versions
npm list react-server-dom-webpack react-server-dom-parcel
# Upgrade to safe versions
npm install [email protected]
npm install [email protected]
npm install [email protected]
# Verify upgrade
npm audit
For Next.js Applications:
# Check Next.js version
npm list next
# Upgrade to patched version
npm install [email protected]
# Or appropriate version for your major release
# Restart application
npm run build
pm2 restart app
Verification
Confirm You're Safe:
# Check package versions
cat package-lock.json | grep -A2 "react-server-dom"
# Verify no vulnerable versions
npm audit | grep -i "CVE-2025-55184\|CVE-2025-67779\|CVE-2025-55183"
Beyond Patching: Additional Security Measures
1. Secret Rotation
Immediate Actions:
- Rotate all API keys potentially exposed in Server Functions
- Update database credentials hardcoded in source
- Change authentication tokens embedded in code
- Revoke and reissue OAuth client secrets
Priority Order:
- Payment processing keys (Stripe, PayPal)
- Database credentials
- Third-party API keys
- Authentication tokens
- Internal service credentials
2. Move Secrets to Environment Variables
Before (Vulnerable):
// Server Action
export async function processPayment() {
const stripeKey = "sk_live_1234567890"; // ❌ EXPOSED
// ...
}
After (Secure):
// Server Action
export async function processPayment() {
const stripeKey = process.env.STRIPE_SECRET_KEY; // ✅ SAFE
// ...
}
3. Implement Rate Limiting
Protect Against DoS:
// middleware.ts
import { Ratelimit } from "@upstash/ratelimit";
const ratelimit = new Ratelimit({
redis: Redis.fromEnv(),
limiter: Ratelimit.slidingWindow(10, "1 m"),
});
export async function middleware(request) {
const ip = request.ip ?? "127.0.0.1";
const { success } = await ratelimit.limit(ip);
if (!success) {
return new Response("Too Many Requests", { status: 429 });
}
return next();
}
4. WAF Rules and Detection
Deploy Protection Rules:
Organizations should not rely solely on WAF mitigations. While Vercel, Akamai, and other providers deployed blocking rules, these cannot catch all payload variants.
Detection Patterns:
Look for:
- Next-Action headers combined with $@ patterns
- resolved_model strings in request bodies
- _formData.get in POST payloads
- High CPU usage from Node.js processes
- Repeated requests to Server Action endpoints
5. Monitoring and Alerting
Set Up Detection:
// Monitor for exploitation attempts
app.use((req, res, next) => {
if (req.body && typeof req.body === 'string') {
if (req.body.includes('$@') ||
req.body.includes('_formData') ||
req.body.includes('resolved_model')) {
logger.alert('Potential CVE-2025-55184 exploitation attempt', {
ip: req.ip,
body: req.body.substring(0, 200)
});
}
}
next();
});
6. Deployment Environment Protection
Secure Preview Deployments:
- Enable deployment protection on preview environments
- Audit shareable deployment links
- Restrict access to staging/development instances
- Implement authentication on non-production deployments
The Bigger Picture: Post-React2Shell Landscape
The discovery of these vulnerabilities reflects a broader pattern in cybersecurity: major vulnerabilities trigger intensive scrutiny that reveals additional flaws.
The Exploitation Timeline
React2Shell Impact:
- December 3: CVE-2025-55182 disclosed
- Hours later: China-nexus APT groups begin exploitation
- December 4: EtherRAT advanced implant deployed via React2Shell
- Widespread scanning and exploitation attempts
- CISA adds to Known Exploited Vulnerabilities catalog
Follow-On Discoveries:
- Security community analyzes React2Shell patches
- Researchers test bypass techniques
- Additional vulnerabilities discovered in adjacent code
- CVE-2025-55184, CVE-2025-55183, CVE-2025-67779 disclosed
Industry-Wide Implications
This sequence demonstrates several critical lessons:
1. Patches Don't End the Story: Initial fixes may be incomplete—continuous monitoring required.
2. Vulnerability Clustering: One major CVE often signals more issues in the same codebase.
3. Attacker Adaptation: Threat actors quickly pivot from one vulnerability to adjacent attack vectors.
4. Supply Chain Amplification: A single library flaw affects millions of applications instantly.
Long-Term Security Strategy
1. Continuous Dependency Monitoring
Implement Automated Scanning:
# GitHub Dependabot
# Snyk continuous monitoring
snyk monitor
# OWASP Dependency Check
mvn dependency-check:check
2. Security-First Development
Code Review Standards:
- Never hardcode secrets in source code
- Always use environment variables for sensitive data
- Implement secret scanning in CI/CD
- Regular security training for developers
3. Incident Response Readiness
Prepare for Future Vulnerabilities:
- Maintain updated asset inventory
- Document all React/Next.js deployments
- Establish emergency patching procedures
- Test rollback capabilities
- Practice incident response scenarios
4. Defense in Depth
Layer Security Controls:
- WAF protection
- Rate limiting
- Input validation
- Monitoring and alerting
- Network segmentation
- Principle of least privilege
Conclusion: The Never-Ending Patch Cycle
The React Server Components security crisis demonstrates the reality of modern software security: patching is not a one-time event but an ongoing process. Organizations that patched for React2Shell found themselves vulnerable again days later. Those who upgraded to the "fixed" versions 19.0.2, 19.1.3, or 19.2.2 discovered they needed to patch again immediately.
Critical Takeaways:
✅ Patch immediately to versions 19.0.3, 19.1.4, or 19.2.3
✅ Don't assume you're safe - verify your actual installed versions
✅ Rotate secrets - especially those hardcoded in Server Functions
✅ Monitor actively - implement detection for exploitation attempts
✅ Plan for future vulnerabilities - this won't be the last React CVE
The Hard Truth: The React ecosystem experienced React2Shell, three follow-on CVEs, and an incomplete initial patch all within 8 days. Organizations running React Server Components must accept that continuous vigilance and rapid response capabilities are now mandatory.