Secure Supply Chain with Sigstore, Cosign & SLSA Framework
As software supply chain threats continue to evolve, securing every stage of the build process has become a business-critical priority. This blog explores how Sigstore, Cosign, and the SLSA Framework are transforming container security by enabling cryptographic signing, provenance verification, and end-to-end supply chain integrity. Learn how these technologies integrate seamlessly into modern DevOps pipelines to establish trust, transparency, and tamper resistance across your software delivery lifecycle.

1. Introduction: The Supply Chain Problem
Modern software delivery pipelines rely on a complex web of open-source dependencies, CI/CD automation, container registries, and orchestration platforms.
This interconnected ecosystem introduces risks such as:
- Compromised build environments
- Tampered container images
- Malicious third-party dependencies
- Lack of verifiable provenance
Example:
The SolarWinds and Codecov supply chain attacks showed that even signed software can’t be trusted if the build process itself is compromised.
Hence, security is shifting “left” — directly into the build and packaging stages, where trust must begin.
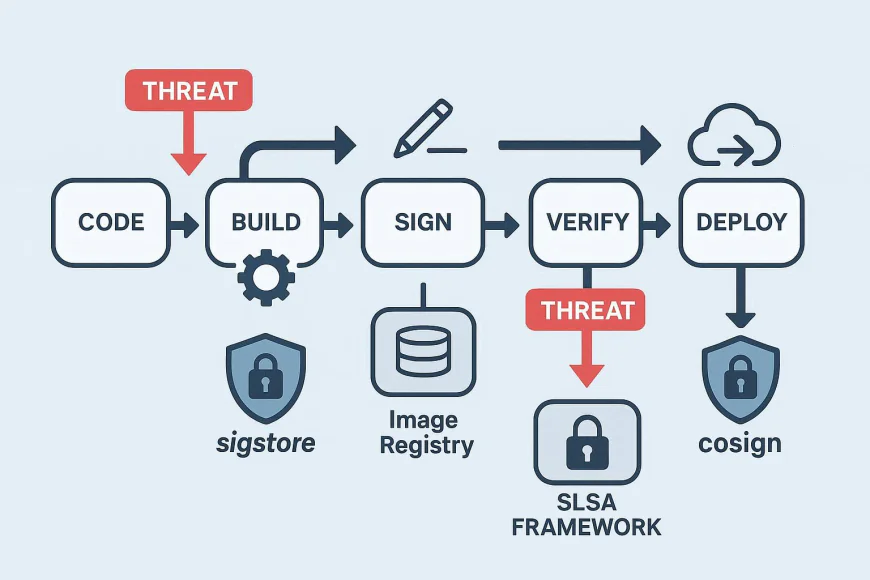
2. Understanding Sigstore and Cosign
Sigstore Overview
Sigstore is an open-source project (backed by Google, Red Hat, and the Linux Foundation) designed to make digital signing and verification of software artifacts easier and more transparent.
It eliminates the traditional complexity of PKI (Private Key Infrastructure) by providing:
- Keyless signing using OIDC identities (e.g., GitHub Actions, Google, etc.)
- Public transparency logs via Rekor (immutable log for signed metadata)
- Fulcio CA for ephemeral certificate issuance
Cosign: Simplifying Container Signing
Cosign (by Sigstore) allows you to sign, verify, and store container image signatures directly inside container registries — right next to the images they secure.
Example workflow:
# Sign a container image
cosign sign --keyless ghcr.io/org/app:latest
# Verify its authenticity
cosign verify ghcr.io/org/app:latest
When integrated into CI/CD (e.g., GitHub Actions, Jenkins, or ArgoCD), Cosign ensures only trusted, verified artifacts are deployed into production.
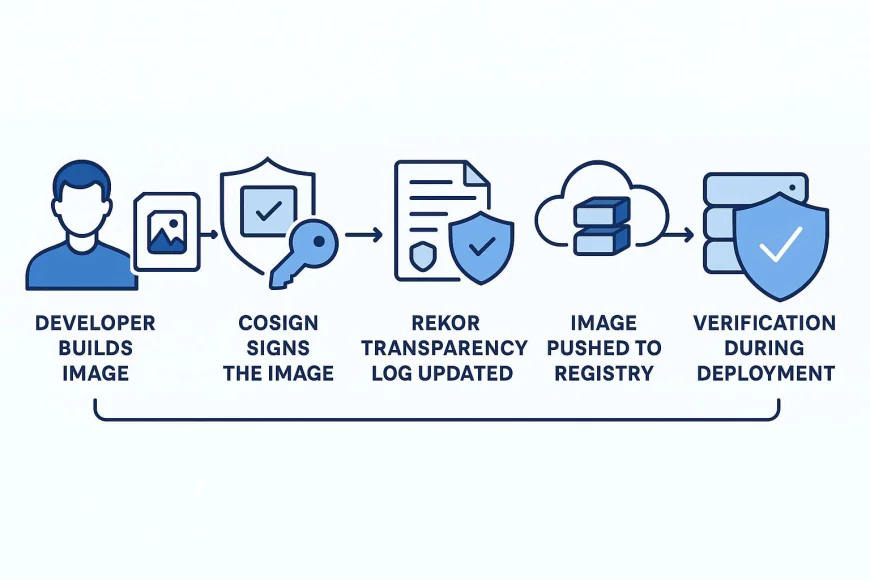
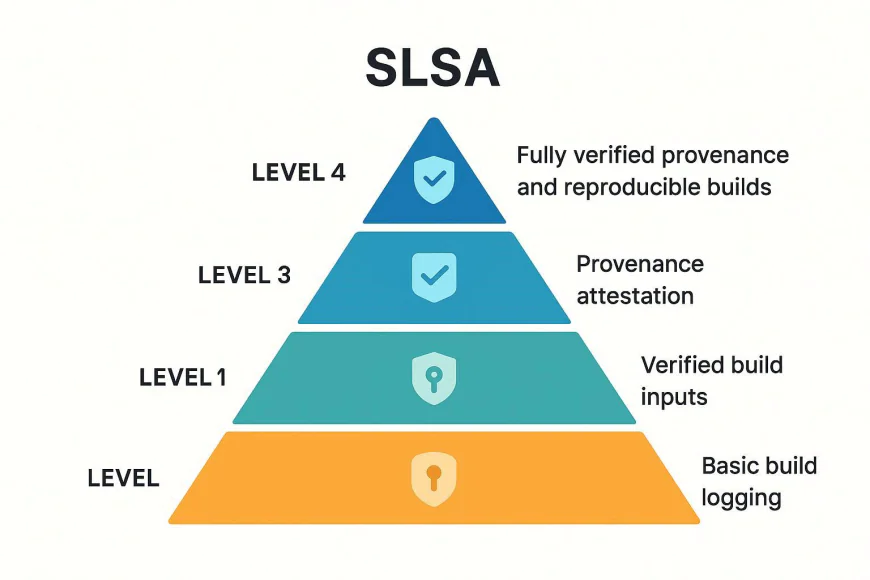
3. The Role of the SLSA Framework
What is SLSA?
SLSA (Supply-chain Levels for Software Artifacts), pronounced “salsa,” is a security framework by Google that defines graduated levels of supply chain integrity — from source to production.
It provides a structured approach with four levels of assurance:
|
Level |
Description |
|
SLSA 1 |
Build process is documented |
|
SLSA 2 |
Build is scripted and automated |
|
SLSA 3 |
Provenance is captured and verified |
|
SLSA 4 |
Reproducible builds and hermetic environments |
Goal: Make it extremely hard for attackers to inject malicious code or modify build outputs without detection.
4. Integrating Sigstore, Cosign & SLSA in DevOps Pipelines
Example Flow:
- Developer commits code → GitHub Action triggers build
- Build produces image + provenance metadata (SLSA)
- Cosign keylessly signs the image → stores signature in registry
- Rekor logs the signature and metadata publicly
- Deployment stage uses Cosign verify before applying manifests
- ArgoCD or Flux enforces admission control (deny unsigned images)
CI/CD Integration Example (GitHub Actions)
name: Secure Build Pipeline
on: [push]
jobs:
build-sign:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Build Docker image
run: docker build -t ghcr.io/org/app:${{ github.sha }} .
- name: Sign with Cosign
run: cosign sign --keyless ghcr.io/org/app:${{ github.sha }}
- name: Upload Provenance (SLSA)
uses: slsa-framework/slsa-github-generator@v1
This ensures end-to-end traceability and trust, linking every artifact to a specific commit and verified signer identity.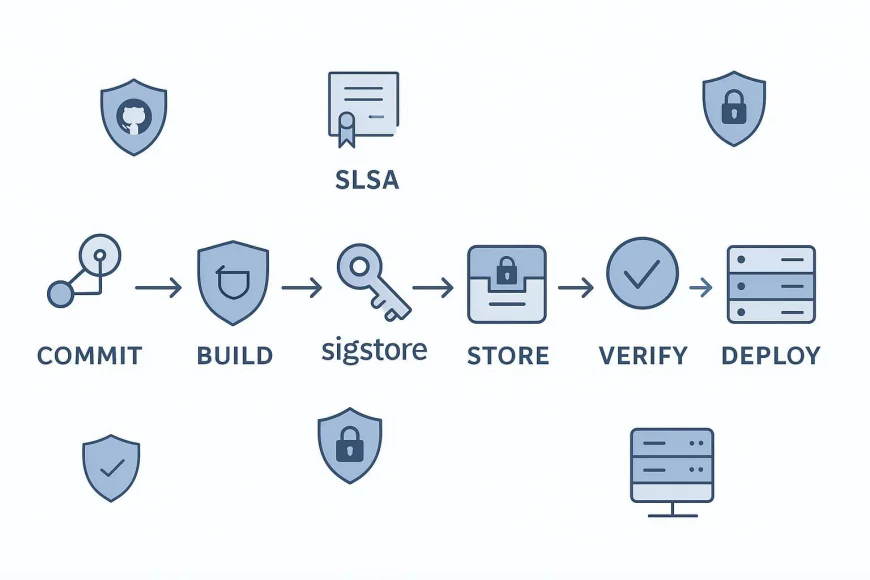
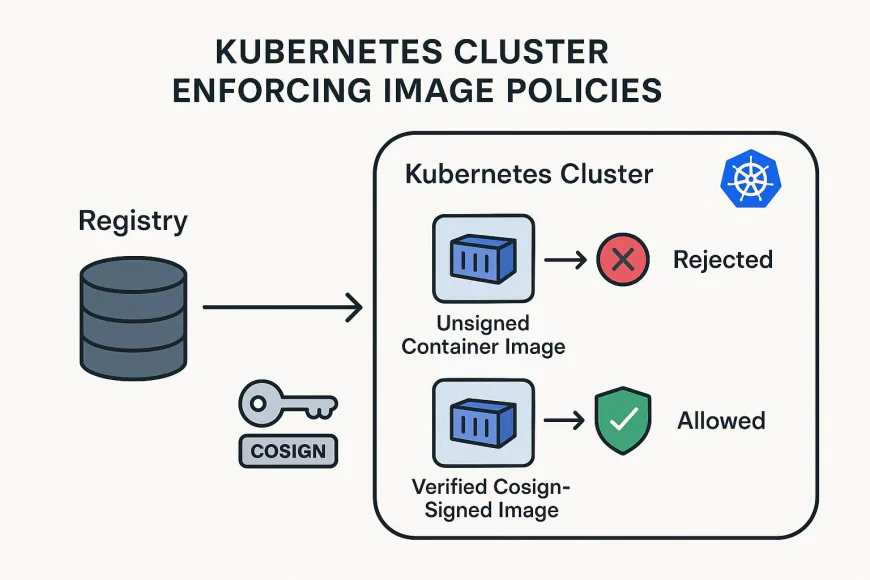
5. Verification and Policy Enforcement
You can enforce security policies using Kubernetes Admission Controllers, OPA/Gatekeeper, or Kyverno to ensure:
- Only signed images are deployed.
- Signatures must be verifiable via Sigstore.
- Provenance metadata must match build source.
Example Kyverno Policy:
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: verify-image-signature
spec:
validationFailureAction: enforce
rules:
- name: check-cosign-signature
match:
resources:
kinds: ["Pod"]
verifyImages:
- image: "ghcr.io/org/*"
keyless: true
issuer: "https://token.actions.githubusercontent.com"
6. The Business Impact
Implementing Sigstore + SLSA strengthens:
- Regulatory compliance (e.g., NIST SSDF, ISO 27001)
- Incident response readiness through transparent logs
- Developer trust in CI/CD pipelines
- Operational resilience across environments
It turns “trust by assumption” into trust by verification.
7. Conclusion
Container signing and provenance verification are no longer optional — they’re fundamental to modern DevSecOps.
By combining Sigstore’s simplicity, Cosign’s flexibility, and SLSA’s structured assurance model, organizations can build a verifiable chain of trust across every stage of their software supply chain.
Your CI/CD pipeline becomes not just fast — but provably secure.