How to Use OPA (Open Policy Agent) for Kubernetes Security
In 2025, Kubernetes has become the backbone of cloud-native applications—but it’s also a prime target for misconfigurations and insider threats. Open Policy Agent (OPA) offers a powerful way to secure Kubernetes by enforcing custom rules like blocking privileged containers, restricting image registries, or requiring labels on deployments. This blog explains how OPA works, how to integrate it with Kubernetes using Gatekeeper, and real-world security use cases every DevSecOps engineer should know.

Introduction
Kubernetes is now the backbone of modern cloud-native applications—but its complexity also makes it risky. A single misconfiguration, like running privileged containers or pulling images from an unverified registry, can lead to a major breach. Traditional security tools often fail to address policy enforcement at scale. This is where Open Policy Agent (OPA) comes in.
OPA is an open-source, policy-as-code framework that lets you define and enforce custom rules in Kubernetes. By combining OPA with Kubernetes admission controllers (like Gatekeeper), you can stop insecure workloads before they’re deployed.
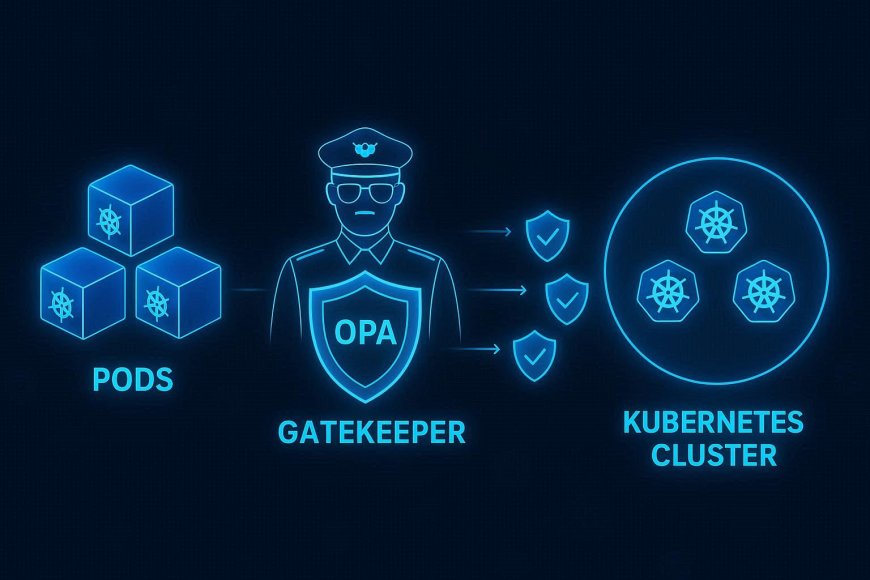
🔹 Why OPA for Kubernetes Security?
· Centralized Policy Enforcement – Apply the same security rules across clusters.
· Prevent Misconfigurations – Block risky deployments (e.g., privileged containers).
· Compliance Support – Enforce PCI DSS, HIPAA, or GDPR requirements in workloads.
· Flexibility – Write rules in Rego language tailored to your environment.
· Shift-Left Security – Catch issues before deployment, not after.
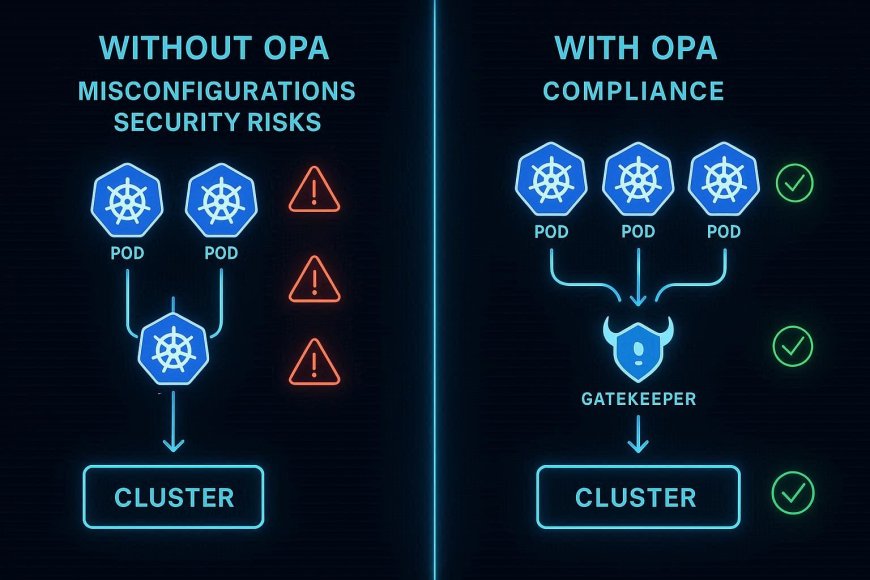
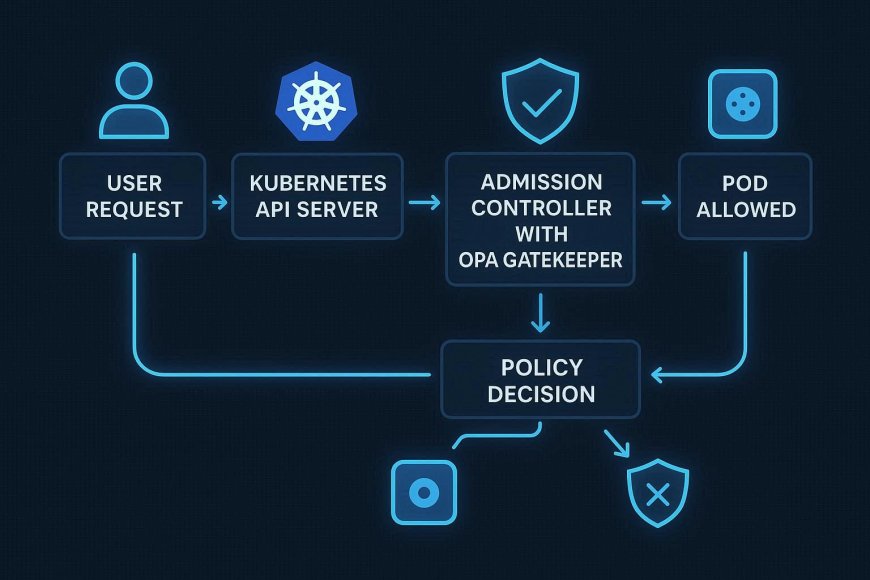
🔹 How OPA Works (Simplified)
OPA uses a policy engine that evaluates requests against your rules:
- A user tries to deploy a Kubernetes pod.
- The Admission Controller intercepts the request.
- OPA checks the request against policies written in Rego.
- If it violates rules → denied. If it passes → approved.
🔹 Step-by-Step: Implementing OPA with Gatekeeper
1. Install Gatekeeper
kubectl apply -f https://raw.githubusercontent.com/open-policy-agent/gatekeeper/master/deploy/gatekeeper.yam
2. Define a Constraint Template (e.g., block privileged containers)
yaml
apiVersion: templates.gatekeeper.sh/v1beta1kind: ConstraintTemplatemetadata: name: k8sprivilegedcontainerspec: crd: spec: names: kind: K8sPrivilegedContainer targets: - target: admission.k8s.gatekeeper.sh rego: | package k8sprivilegedcontainer violation[{"msg": msg}] { input.review.kind.kind == "Pod" input.review.spec.containers[_].securityContext.privileged == true msg := "Privileged containers are not allowed" }
3. Enforce the Policy
yaml
apiVersion: constraints.gatekeeper.sh/v1beta1kind: K8sPrivilegedContainermetadata: name: disallow-privilegedspec: match: kinds: - apiGroups: [""] kinds: ["Pod"]
4. Test It
Try deploying a privileged container—it will be blocked.
🔹 Real-World Use Cases for OPA in Kubernetes
- Restrict Image Registries – Only allow images from trusted registries like ECR/GCR.
- Mandatory Labels – Enforce “owner” or “environment” labels on all deployments.
- Disallow Host Networking – Block pods that request host networking.
- Restrict Resource Limits – Ensure every container has CPU/memory limits.
- Block Deprecated APIs – Prevent workloads using outdated Kubernetes APIs.
Best Practices for Using OPA in DevSecOps
- Treat policies as code (store in Git, use CI/CD for testing).
- Start with audit mode before enforcing hard denials.
- Use version control for policy updates.
- Combine OPA with CIS Benchmarks for Kubernetes.
- Continuously monitor with logging and alerting.
🔹 Conclusion
OPA is a game-changer for Kubernetes security in 2025. Instead of relying on traditional perimeter defences, it gives DevSecOps teams the ability to embed security directly into the Kubernetes admission process. With tools like Gatekeeper, engineers can enforce compliance, consistency, and resilience across clusters—making Kubernetes both agile and secure.