WhatsApp Hijacking Malware Maverick Emerges as Major Threat to Brazilian Financial Sector
The Maverick banking malware campaign exploits WhatsApp's massive Brazilian user base to distribute sophisticated banking trojans targeting 26 major Brazilian financial institutions. This represents a watershed moment in Latin American cybercrime, combining WhatsApp message hijacking, dual-channel command-and-control infrastructure, and AI-assisted code development to achieve unprecedented scale-with over 62,000 blocked infection attempts in October 2025 alone. Security researchers from Trend Micro, Kaspersky, and CyberProof have identified this as an evolution of the earlier Coyote banking trojan, indicating sustained, coordinated criminal operations with institutional capability operating within Brazil's cybercriminal ecosystem.

Brazilian users and banks are under a serious risk of cybersecurity as researchers found large connections between two highly developed banking trojans that are being used through WhatsApp. The recently revealed malware called Maverick, is very similar to the previous banking trojan Coyote, both of which are aimed at Brazilian users and institutions with extraordinary operational sophistication.
Kaspersky, Trend Micro, CyberProof, and Sophos have made a joint effort to find out the evolution of banking malware tactics inside the Brazil's cybercriminal ecosystem. The malware, which is attributed to a hacking group that is called Water Saci, shows a major change in the way that the attackers distribute the banking trojans-moving from phishing based on traditional email to exploiting the trust and large network of WhatsApp messaging.
The Infection Chain Disclosed
Initially, the attack is misleading. Users are sent via WhatsApp messages these ZIP file attachments that normally would be unblocked and let through, files, such as invoices, receipts, or forms in Portuguese. When a user decompresses these files, he/she sees a file with an LNK extension, which is the shortcut file associated with Windows.
If this shortcut is clicked, it instigates a complex, multi-step infection that is nearly entirely in RAM, thus lowering detection by standard antivirus software. The assault is performed via a propagating element called SORVEPOTEL that doubles as the distribution for the primary payload, Maverick.
The early phases employ PowerShell and Visual Basic Script to set up residence on the victim's machine. To do so, the menace makes changes to specific entries in the Windows registry or sets up scheduled batch files that will work even when the system is restarted. Critically, SORVEPOTEL does not remain inactive after installation but instead, it takes over the victim's WhatsApp Web session by acquiring the legitimate Chrome profile data that contains the authentication tokens and cookies. As a result, the malware is able to get around WhatsApp Web's authentication protocols completely which leads to instant access to the compromised account without any security alerts or scanning of QR codes.
The malware already present, it calls upon various browser automation tools like ChromeDriver and Selenium to systematically go through the victim's contact list and groups, with the result that the same malicious ZIP files are being sent out to all contacts in an automatic fashion. This worm-like feature is what makes the campaign able to gain ground so quickly among the Brazilian users.
Targeting and Capabilities
Maverick's targeting precision speaks of a very thorough and careful development plus extremely good reconnaissance. One feature of the malware is a geographic check that looks for Brazilian system settings such as language configurations, time zone, region settings, and date formats. The computer that the malware has infected will not be allowed to use its main payload if it doesn't pass the checks. This shows that the perpetrator is so meticulous that the Maverick's impact in Brazil is maximized while the risk of being detected in the neighboring countries is minimized.
Maverick once it is on the Brazilian system, it goes to the other side of the world, aggressive and gets into theft mode. The banking trojan watches all the time very attentively and constantly the active browser tabs and all the URLs visited by the infected user. When ardently the malware detects URLs to the financial institution that is on its hard-coded list, it takes all the necessary actions. Maverick has its sight set on the traffic of 26 major Brazilian banks which include Banco do Brasil, Itaú, Bradesco, Caixa Econômica Federal, and Santander Brasil among others. Moreover, it records the access to six cryptocurrency exchanges and payment platforms.
Once the evil one gets detected, it injects malicious JavaScript into the legitimate banking websites, creating overlay windows that are indistinguishable from the authentic login pages. These phishing interfaces are very effective and capture all kinds of sensitive information such as users' usernames, passwords, etc. Legitimately, the malware installs keyloggers that will record all keystrokes and goes further to screen capture transactions and data besides that. In extreme cases, Maverick restricts the user's access to the actual banking website and presents the fraudulent interface, thus ensuring that the victim's interaction is only with the pages controlled by the attacker.
Command and Control Innovation
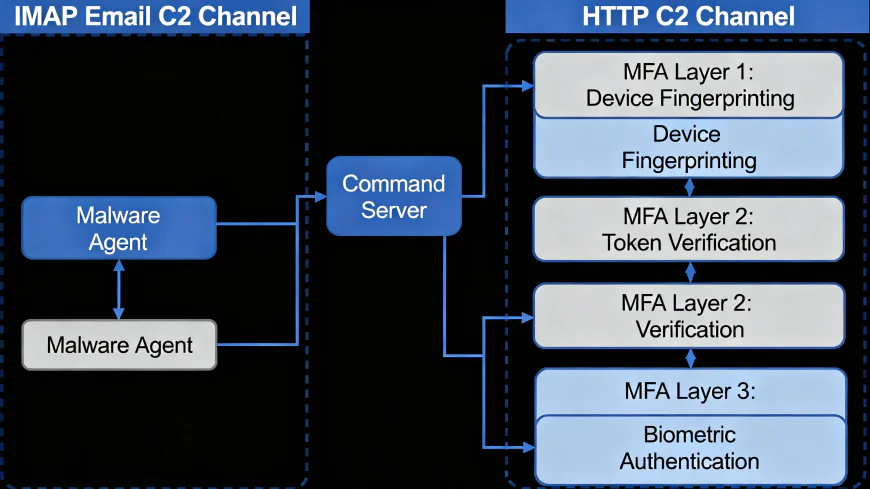
The advanced command-and-control (C&C) structure is the main feature that the campaign shares with the stereotypical banking trojans. SORVEPOTEL has two communication channels for C2, one of which is IMAP connections to hardcoded terra.com.br email accounts and the other one is the regular HTTP-based communication. The email-based infrastructure gives the malware operational resilience as it can switch to email communication in case the conventional HTTP channels go down, and it can retrieve commands and configuration data hidden within the email content.
The attackers have also made this infrastructure more reliable by using multi-factor authentication for the email accounts. This creates operational delays - every login now requires the manual input of one-time authentication codes - but it is an arresting legal or security researcher that can disrupt the campaign infrastructure with difficulty.
The remote-control mechanism gives the attackers unparalleled operational power. The security researchers found more than twenty different commands that the malware can support, which allows the attackers to turn on and off the propagation campaigns as quickly as they want, to get detailed information about the system, to run arbitrary programs, to change files, to take screenshots, to move the mouse, and to install more malware. This is a full-scale transformation of the hacked computers into specialized botnet nodes that are under the control of the operator.
The Coyote Connection
Red flags were raised that Maverick and the old Coyote banking trojan have some things in common, and thus the researchers decided to check if there were any operational linkages. The .NET written malware, which is aimed at Brazilian users and banks specifically, was also one of the features common to the two families. The same functionality was even used for the banking URLs' decryption, which was one of the identifying features between the two families. Another common feature by the two families is their ability to gain access through WhatsApp Web, which is rather sophisticated and indicates that one has evolved into the other over time.
Looking into the decryption operations, both Maverick and Coyote are found to have similar characteristics in that they apply AES encryption coupled with GZIP compression to render the lists of targeted banking URLs, which are stored in base64 encoding, completely unreadable. The technical similarities, along with the concurrent development of the distribution strategies, have led the experts to think that Water Saci and Coyote are probably operating in the same Brazilian cybercrime ecosystem and might be even linked to the same threat actors.
Scale of the Threat
The operational scale has been substantial. Just ten days through the active campaigns in October 2025, cyber security solutions had already blocked more than 62,000 infection attempts aimed at users in Brazil. According to Trend Micro's telemetry, out of a total of 477 observed infections, 457 were in Brazil, and the affected organizations were from the government, public services, manufacturing, education, banking, technology, and construction industries. These early findings also point to attackers having widened their targeting to encompass Brazilian hotel chains, thus indicating the operational flexibility and continuous expansion of the campaign.
Industry Reaction and Consequences
The release of the information has led to the immediate reaction from the largest cybersecurity settlement. Besides, Trend Micro, Kaspersky, Sophos, CyberProof, and others have issued thorough technical analysis reports and have also sent detection signatures to corporate clients. Security experts claim that this campaign is a turning point in the distribution of malware in Latin American banking - malefactors have managed to exploit the most used communication means worldwide for the huge extent and fast spreading of their activities.
The campaign's difficulty - fileless execution, memory-based operations, browser hijacking, developing C2 infrastructure, anti-analysis techniques, and automatic propagation - point to the development of Brazillian cybercriminals' skills. The use of AI in code writing, particularly for decrypting certificates and general malware functions, indicates the criminals are taking advantage of tech that is just coming into place for quicker development and less detection.
Financial services firms and their customers are advised to use strong endpoint protection at all levels, keep antivirus definitions updated, practice very high caution with attachments from messaging services no matter how safe the sender looks, and adopt behavioral analysis systems that can differentiate between normal and abnormal process flows and network communications. Vigilant observation is crucial as the threat keeps changing.











































