GoBruteforcer Botnet Exploits Weak Credentials to Target Crypto Databases
GoBruteforcer malware is targeting cryptocurrency and blockchain project databases by abusing weak credentials, exposed FTP services, and legacy XAMPP stacks.

A new type of cyberattack has appeared, which focuses on the infrastructure of cryptocurrency and blockchain projects. The attackers are taking advantage of weak credentials and exposed services to create a botnet that is now becoming larger. The attack is based on a malware written in Golang and called GoBruteforcer, which is currently infiltrating Linux servers and copying login credentials through brute-force across various services.
According to security experts at Check Point Research, the main reasons for the attacks being so successful lie in bad security practices, outdated web technologies, and the use of default credentials that were not changed -many of which come from AI-generated deployment illustrations and obsolete documentation.
What Is GoBruteforcer?
The GoBruteforcer malware family, known as GoBrut as well, was detected by Palo Alto Networks Unit 42 for the first time in March 2023. It was developed to work on Unix-like systems and is compatible with x86, x64, and ARM architectures.
The malware, once it gets installed, brings about the following:
- An IRC-controlled bot for command and control (C2) purposes
- A web shell to facilitate remote access with persistence
- A brute-forcing module which locates the vulnerable systems by scanning the internet
Through this modular format, the hackers are permitted to promptly increase the size of the botnet by converting the invaded servers into the attack nodes.
A More Advanced Variant Emerges
In the middle of the year 2025, Check Point's scientists noticed a more advanced version of GoBruteforcer. The new variant consists of:
- The IRC communication is extremely obfuscated and hard to trace
- The use of more advanced methods to ensure the virus stays in the system
- Detection Evaded by using Process Masking Techniques
Different attack campaigns with the use of dynamic credential rotation
Black Lotus Labs (Lumen Technologies) had earlier done research work which also indicated that a certain number of infected machines had been co-infected with the SystemBC malware, thus demonstrating the possibility of collaboration or sharing of infrastructure among the different threat actors.
Why Crypto and Blockchain Projects Are Prime Targets
It seems that the hackers deliberately aimed at crypto infrastructure, like databases and admin panels. Most of the usernames identified in the brute-force credential lists are linked either to crypto projects or widely adopted deployment methods that are quite common.
Examples include:
- cryptouser
- crypto_app
- appcrypto
- crypto
- root, wordpress, and wpuser for phpMyAdmin access
Researchers pointed out that a big number of these usernames come from online tutorials, vendor documents, and code samples created by AI. As large language models use such material for their training, insecure defaults are continuously created and used in production which is a real-world scenario.
Exploiting Legacy XAMPP and FTP Services
The exposed FTP services running XAMPP-based servers with minimal hardening are one of the most frequently used ways to get into this campaign.
The usual manner of infection includes:
- guess and check FTP credentials
- put a PHP web shell on the server
- get and run the GoBruteforcer payload through a shell script
- picking the right binary for the system automatically
- FTP brute-force module, unlike other services, is dependent on a very small fixed password set which is a strong indication that it is primarily targeting default web-hosting accounts and outdated software stacks.
How Compromised Servers Are Used
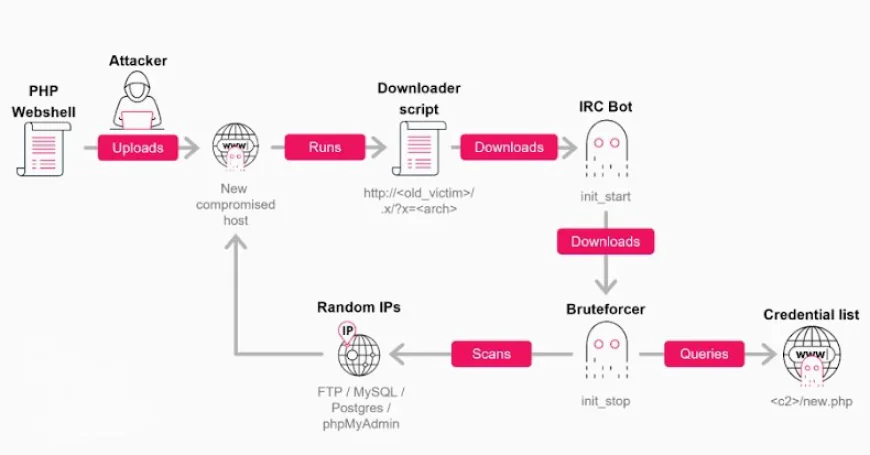
An infected server can take on several roles in the botnet:
- Conducting brute-force attacks on FTP, MySQL, PostgreSQL, and phpMyAdmin
- Storing and transferring malware payloads
- Functioning as a backup C2 or IRC channel for botnet survivability
Such versatility makes it possible for the botnet to continue operating amidst disruptions of its infrastructure.
Blockchain-Focused Activity Detected
A more detailed investigation has uncovered that at the very least, one of the hacked servers was running a module that could check the TRON blockchain addresses. The module obtained the balances through the Tronscan API queries in order to point out the wallets that had money in them, thus indicating a direct interest in the financial exploitation of blockchain ecosystems.
Hence, the fear of a systematic targeting of crypto projects with the motivation of their financial value and the often insecure nature of their infrastructures is once again confirmed.
Broader Security Implications
Check Point skriver, GoBruteforcer viser et vedvarende og voksende problem:
Brute-force attacks are easily made by large hackers and all because of the trio of exposed services, weak passwords and automated attack tools.
The malware, however, is not that sophisticated but the perpetrator has a great number of poorly configured systems that are still on the internet.
Final Thoughts
The GoBruteforcer attack reminds us all again that the most basic security measures are still very important. Companies -particularly those dealing with cryptocurrencies and blockchain- should:
- Remove default and reused passwords
- Control the public access to administration services
- Strengthen old technology foundations such as XAMPP
- Check AI-drafted deployment settings
When automated attacks are getting bigger every day, it is easy to turn one’s infrastructure into a global botnet just by ignoring the basic security measures.