Massive Credential-Spraying Campaign Targets Cisco & Palo Alto Networks VPN Gateways
In mid-December 2025, threat actors launched a coordinated credential-spraying campaign against enterprise VPN infrastructure, targeting Palo Alto Networks GlobalProtect portals with 1.7 million login attempts in 16 hours and pivoting to Cisco SSL VPNs the next day. Originating from 10,000+ IPs hosted by Germany's 3xK GmbH, the attacks use automated password spraying rather than vulnerability exploitation.
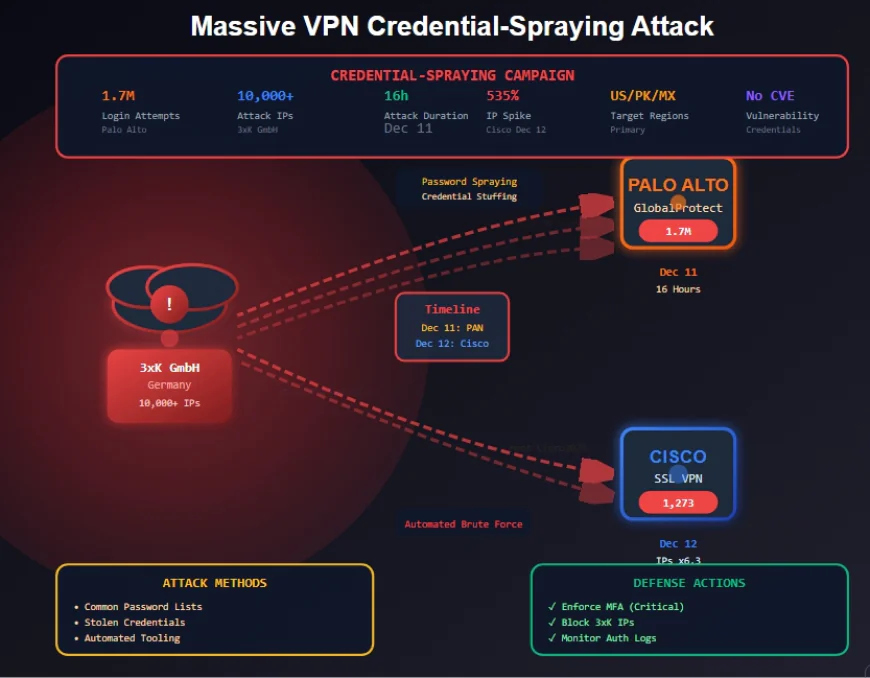
Enterprise VPN infrastructure became the target of a massive, coordinated credential-spraying campaign in mid-December 2025, with threat actors hammering Palo Alto Networks GlobalProtect portals and Cisco SSL VPN endpoints with millions of automated login attempts. Unlike sophisticated zero-day exploits, this campaign relies on a simpler but equally dangerous approach: testing stolen credentials and common passwords against enterprise authentication systems at unprecedented scale.
On December 11, 2025, GreyNoise threat intelligence detected over 1.7 million login sessions targeting GlobalProtect portals in just 16 hours, followed by a sharp pivot to Cisco SSL VPNs the next day. With more than 10,000 unique IP addresses participating—nearly all hosted by Germany's 3xK GmbH—this campaign demonstrates the persistent threat facing remote access infrastructure and the critical importance of strong authentication controls.
The Attack Timeline: Two Days of Relentless Probing
December 11: Palo Alto Networks GlobalProtect Under Siege
GreyNoise sensors detected a massive surge on December 11, 2025, with over 1.7 million sessions flooding emulated GlobalProtect portals in just 16 hours—a staggering volume that peaked at sustained rates exceeding 100,000 attempts per hour.
Attack Characteristics:
- Volume: 1.7 million login sessions in 16 hours
- Source IPs: 10,000+ unique addresses
- Infrastructure: Almost entirely from 3xK GmbH (Germany) IP space
- Target Geography: United States, Pakistan, Mexico
- Method: Automated credential stuffing and password spraying
Technical Indicators: Attackers deployed uniform request patterns with common username-password combinations and a Firefox user agent atypical for automated activity through this provider. The sharp spike suggests a new inventory effort or campaign kickoff, as GreyNoise has tracked similar waves during peak threat periods.
December 12: Pivot to Cisco SSL VPN
Activity shifted to Cisco SSL VPNs on December 12, with attacking IPs spiking from a baseline of under 200 to 1,273 unique addresses in a single day—a stark anomaly indicating coordinated campaign expansion.
Cisco Attack Profile:
- Daily IPs: From ~200 baseline to 1,273 (535% increase)
- Infrastructure: Same 3xK IP space as Palo Alto attacks
- User Agent: Dominant Windows NT 10.0 (unusual for this provider)
- First Large-Scale: First major 3xK deployment against Cisco SSL VPN in 12 weeks
Most traffic hit GreyNoise's vendor-agnostic Facade sensors, indicating opportunistic scanning rather than precise targeting. Sessions shared the same TCP fingerprint and cloud infrastructure as the Palo Alto wave, confirming coordinated campaign activity.
The Threat Actor: 3xK GmbH Infrastructure
Nearly all malicious traffic originated from IP space associated with German hosting provider 3xK GmbH, indicating the use of centralized, cloud-hosted infrastructure rather than widely distributed botnet operations.
Why Cloud Infrastructure?
- Scalability: Rapidly deploy thousands of attacking IPs
- Legitimacy: Cloud IPs harder to blanket-block than residential proxies
- Control: Centralized command and orchestration
- Speed: High-bandwidth connections for rapid attacks
Historical Context: 3xK infrastructure has been observed in previous VPN targeting campaigns, including Arctic Wolf's February 2024 detection of similar password spraying against Cisco, Palo Alto Networks, and WatchGuard appliances.
Attack Methodology: Credential Stuffing vs. Password Spraying
This campaign employs two related but distinct techniques:
Credential Stuffing
Definition: Testing stolen username/password pairs from data breaches against different services.
How It Works:
- Attackers obtain credential lists from previous breaches
- Automated tools test these pairs against VPN login portals
- Successful matches grant immediate network access
- Often targets users who reuse passwords across services
Password Spraying
Definition: Testing a small number of common passwords against many accounts to avoid lockouts.
How It Works:
- Attackers compile lists of usernames (OSINT, directory harvesting)
- Select common passwords: "Welcome1", "Spring2024!", "Password123"
- Try one password against all accounts, then move to next password
- Timing delays prevent account lockouts
- Targets organizations with weak password policies
Observed request bodies indicate automated credential-based authentication attempts rather than vulnerability exploitation. Example payloads follow standard SSL VPN login workflows, including CSRF token handling and parameterized username/password fields, consistent with scripted attacks.
Why This Campaign Matters: The Enterprise Risk
No Vulnerability Required
Palo Alto Networks confirmed: "This activity reflects automated credential probing and does not constitute a compromise of our environment or an exploitation of any Palo Alto Networks vulnerability."
The Reality: Attackers don't need zero-days when weak passwords exist. This campaign succeeds by exploiting human factors—password reuse, weak credentials, and insufficient MFA adoption.
VPN Gateways Are High-Value Targets
Why Attackers Target VPNs:
- Direct Network Access: VPN compromise bypasses perimeter defenses
- Lateral Movement: Authenticated VPN provides springboard for internal attacks
- Credential Harvesting: VPN access often indicates privileged users
- Persistent Access: VPN accounts can maintain long-term access
Scale Overwhelms Traditional Defenses
The Challenge:
- 1.7 million attempts in 16 hours = 29,000+ attempts per minute
- 10,000+ unique IPs make IP blocking impractical
- Automated tooling operates 24/7 without fatigue
- Cloud infrastructure provides unlimited scale
Technical Analysis: How the Attacks Work
Request Structure
Palo Alto GlobalProtect Login:
POST /ssl-vpn/login.esp HTTP/1.1
Host: vpn.target.com
Content-Type: application/x-www-form-urlencoded
user=testuser&passwd=Welcome2024!&ok=Login&direct=yes
Cisco SSL VPN Login:
POST /+webvpn+/index.html HTTP/1.1
Host: vpn.target.com
Content-Type: application/x-www-form-urlencoded
username=admin&password=Cisco123&Login=Login
Common Password Lists
Observed Patterns:
- Season + Year variations: "Spring2024!", "Winter2025"
- Company name + number: "Acme123!", "Cisco2024"
- Default credentials: "admin/admin", "user/password"
- Keyboard patterns: "Qwerty123", "Password1!"
Evasion Techniques
How Attackers Avoid Detection:
- Low-and-slow: Space attempts over time to avoid rate limits
- IP rotation: 10,000+ IPs prevent effective IP blocking
- Legitimate-looking: Firefox/Windows user agents mimic real users
- Standard workflows: Follow normal login processes with CSRF tokens
Real-World Impact: What Successful Attacks Enable
Case Study: Cisco 2022 Breach
Attack Vector: Password spraying against contractor accounts Result: Threat actors accessed internal systems, enrolled new MFA device, exfiltrated source code
Key Lesson: A compromised contractor account accessed via password spraying enabled threat actors to enroll a new MFA device and gain access to Cisco's internal systems, highlighting the risk of incomplete offboarding and unmonitored contractor credentials.
CISA Federal Agency Breach
Attack Method: Password spray campaign against Outlook Web Access and VPN portals Outcome: Web shell implantation, persistent access via scheduled tasks Impact: Federal agency systems compromised for extended period
The Broader Pattern
Organizations compromised through VPN credential attacks typically experience:
- Initial access leading to ransomware deployment
- Lateral movement to domain controllers
- Data exfiltration before detection
- Extended dwell times (weeks to months)
- Business disruption and financial losses
Detection: Identifying Active Attacks
Log Indicators
Palo Alto GlobalProtect:
Auth failure logs with:
- Rapid sequential attempts from same IP
- Common usernames ("test", "admin", "user")
- Geographic mismatches (user normally US, login from Pakistan)
- Failed attempts outside business hours
Cisco SSL VPN:
Authentication failures showing:
- Multiple usernames from single IP
- Unusual user agents (Firefox from enterprise Windows environment)
- Successful login followed by immediate logout (credential validation)
GreyNoise Detection Tags
For Security Teams:
GreyNoise tags identified:
- "Palo Alto Networks Login Scanner"
- "Cisco SSL VPN Bruteforcer"
Query GreyNoise for attacking IPs:
greynoise query "classification:malicious AND tags:VPN"
Network Behavior Anomalies
Monitor for:
- Authentication spike beyond normal business variance
- Login attempts from unexpected geolocations
- Sequential failed attempts across multiple accounts
- Successful logins followed by unusual internal activity
Immediate Defense Actions
1. Enforce Multi-Factor Authentication (MFA)
Critical Priority: MFA makes credential spraying ineffective even with correct passwords.
Implementation:
- Phishing-resistant MFA: Hardware keys (YubiKey, Titan Security Key)
- Push notification MFA: Duo, Microsoft Authenticator (with number matching)
- Avoid SMS: Susceptible to SIM swapping
- Universal enforcement: No exceptions for "convenience"
Reality Check: Many successful attacks target accounts without MFA or with easily bypassed SMS-based methods.
2. Implement Strong Password Policies
Requirements:
- Minimum 14 characters
- Complexity requirements
- Password history (prevent reuse)
- Regular password rotation for privileged accounts
- Ban common passwords ("Welcome2024!", "Password123")
Use Password Managers: Organizations should mandate password manager usage to enable unique, complex passwords across all systems.
3. Deploy Rate Limiting and Account Lockouts
Intelligent Throttling:
After 3 failed attempts: 5-minute delay
After 5 failed attempts: 15-minute delay
After 10 failed attempts: Temporary account lock + alert
Geographic Restrictions: If users only work from specific countries, block authentication from unexpected regions.
4. Block Malicious IPs
GreyNoise Blocklists:
- Palo Alto Networks Login Scanner blocklist
- Cisco SSL VPN Bruteforcer blocklist
Firewall Rules:
# Block 3xK GmbH IP ranges (example)
deny ip 3xK-range any
deny ip 3xK-range vpn-gateway
# Implement dynamic blocking
create automated rules from threat feeds
5. Audit Network Appliances
Regular Checks:
- Review authentication logs daily
- Identify unexpected login patterns
- Verify all accounts are authorized
- Remove stale/inactive accounts
- Audit contractor access
Questions to Ask:
- Are all login attempts expected?
- Do they require escalation?
- Are legacy accounts still needed?
- Is MFA enforced universally?
Advanced Protection Strategies
1. Implement Zero Trust Architecture
Principles:
- Never trust, always verify
- Least-privilege access
- Microsegmentation
- Continuous authentication
- Device posture checks
VPN Replacement: Consider transitioning to Zero Trust Network Access (ZTNA) solutions that eliminate traditional VPN vulnerabilities.
2. Deploy Deception Technology
Honeypot VPN Portals:
- Deploy fake VPN login pages
- Monitor for credential stuffing attempts
- Collect attacker IPs and tooling signatures
- Feed intelligence to blocking systems
3. User Behavior Analytics (UBA)
Anomaly Detection:
- Baseline normal login patterns
- Alert on deviations (time, location, frequency)
- Machine learning identifies subtle anomalies
- Automated response workflows
4. Conditional Access Policies
Microsoft Azure/Entra ID Example:
Require MFA when:
- User location outside approved countries
- Device not joined to corporate domain
- Risk level elevated
- Accessing from new device
5. Threat Intelligence Integration
Automated Blocking:
- Subscribe to GreyNoise, AlienVault, etc.
- Automatically block known malicious IPs
- Correlate attacks across industry
- Share intelligence with peers
The Broader Context: Enterprise VPN Under Siege
Historical Pattern
February 2024: Arctic Wolf detected password spraying targeting Cisco, Palo Alto, WatchGuard appliances using random usernames like "test"
December 2025: Coordinated campaign with 3xK infrastructure, 10,000+ IPs, millions of attempts
The Trend: Attacks growing in sophistication, scale, and coordination.
Why Attackers Focus on VPNs
2024-2025 Threat Landscape:
- Remote work normalization expands VPN attack surface
- VPN compromise provides internal network access
- Easier than exploiting zero-days
- Credential breaches provide ammunition
- Cloud infrastructure enables massive scale
Industry Response Needed
Collective Defense:
- Share threat intelligence across sectors
- Coordinate blocklist efforts
- Industry-wide MFA adoption
- Government-private partnerships (CISA collaboration)
Vendor Statements and Guidance
Palo Alto Networks
Official Statement: "We are aware of the credential-based activity reported by GreyNoise targeting VPN gateways, including GlobalProtect portals. This activity reflects automated credential probing and does not constitute a compromise of our environment or an exploitation of any Palo Alto Networks vulnerability. Our investigation confirms that these are scripted attempts to identify weak credentials."
Recommendations:
- Use strong passwords
- Enable multi-factor authentication
- Monitor authentication logs
- Implement conditional access policies
Cisco Response
Cisco was contacted for comment but had not issued a public statement as of this writing. However, the company's standard guidance emphasizes:
- Enforcement of MFA on all remote access
- Regular password policy audits
- Monitoring for unusual authentication patterns
GreyNoise Guidance
For Platform Customers: Block all malicious IPs using GreyNoise platform blocklists for:
- Palo Alto Networks Login Scanner
- Cisco SSL VPN Bruteforcer
For Non-Customers: Use GreyNoise Block templates to quickly block threat IPs (14-day free trial available)
Long-Term Security Transformation
Move Beyond Passwords
Passwordless Authentication:
- Windows Hello for Business
- FIDO2 security keys
- Biometric authentication
- Certificate-based authentication
Benefits:
- Eliminates credential stuffing entirely
- Phishing resistant
- Improved user experience
- Reduced help desk burden
Network Architecture Evolution
From VPN to ZTNA: Traditional VPN provides network-level access. ZTNA provides application-level access with:
- Identity-centric security
- Continuous verification
- Microsegmentation
- Better visibility and control
Security Culture
User Education:
- Password hygiene training
- Phishing awareness
- MFA adoption campaigns
- Reporting suspicious activity
Conclusion: The Persistent VPN Threat
This December 2025 credential-spraying campaign demonstrates that attackers don't always need sophisticated zero-days—weak credentials and insufficient MFA adoption provide ample opportunity. With 1.7 million login attempts against Palo Alto GlobalProtect in 16 hours and a rapid pivot to Cisco SSL VPN the next day, this campaign shows coordinated, professional operation at scale.
Key Takeaways:
✅ This is NOT a vulnerability - it's a credential attack exploiting weak passwords
✅ MFA is critical - attackers can't bypass properly implemented MFA
✅ 10,000+ attacking IPs - traditional IP blocking is insufficient
✅ Cloud infrastructure - 3xK GmbH hosting enables massive scale
✅ Ongoing threat - campaign continues with new targets daily
Immediate Actions:
- Enforce MFA universally - no exceptions
- Audit VPN logs - look for attack indicators
- Block malicious IPs - use GreyNoise blocklists
- Strengthen passwords - minimum 14 characters, no common patterns
- Plan ZTNA migration - move beyond traditional VPN
The Hard Truth: Enterprise VPN infrastructure remains under persistent pressure from credential-based attacks. Organizations that rely solely on passwords even with periodic changes—remain vulnerable. The only sustainable defense combines strong MFA, continuous monitoring, threat intelligence integration, and a roadmap toward passwordless authentication.










































