RondoDox Botnet Exploits Critical XWiki Flaw to Expand DDoS Infrastructure
A high severity remote code execution vulnerability (CVE-2025-24893) in XWiki Platform with the highest score (9.8) according to CVSS has become the target of the RondoDox botnet as well as other hackers and is being used to break into unpatched servers around the globe. Crypto miners are being installed, reverse shells are being set up, and compromise systems are being added to the botnet that will later be used for DDoS operations by the attackers, who have also seen a significant increase in exploitation attempts in early November even though patches have been available since February 2025. CISA has ordered all federal agencies to have security measures in place by November 20, 2025, as the vulnerability is still one of the most commonly exploited flaws in the security landscape.

RondoDox is the name of a very advanced botnet malware, which has come to be a part of an increasing number of cyberattacks that are aimed at unpatched XWiki servers all over the planet. The malware is taking advantage of a vulnerability in the system that allows hackers to execute their commands remotely - something security researchers have been warning about as one of the most intensively exploited weaknesses in the last couple of months. The situation is a big change in the threat scenario, as different hacker groups are now fighting with each other to gain access to the same systems, which they could then use for cryptocurrency mining, botnet recruiting, and launching distributed denial-of-service attacks.
The Vulnerability: CVE-2025-24893
CVE-2025-24893, an eval injection vulnerability with a high-impact score of 9.8 out of 10 on the CVSS severity scale, is the cause of the security crisis. This defect is located in the SolrSearch function of the XWiki Platform and it is determined by how the software treats 'text' when requests to the /bin/get/Main/SolrSearch endpoint are processed.
The security issue's main risk is its easy access for an outsider. Any non-registered user will be able to hack and perform remote code execution with XWiki's coaxial installations which are at risk. During the course of the vulnerability, a great number of XWiki versions are impacted, specifically the range from 5.3-milestone-2 to 15.10.11, and the range from 16.0.0-rc-1 to 16.4.1.
The exploit's development involves the flawed validation of Groovy expressions in the search queries. As a consequence, the attackers are able to introduce the malicious Groovy code which the system will evaluate with poor sanitization and thus will lead to the compromise of the whole system under the privileges of the web server account. The impact of the attack is on the confidentiality, integrity, and availability of the entire XWiki installation.
Patch Timeline and Exploitation History
XWiki developers acted quickly after the vulnerability announcement and made security updates available in the 15.10.11, 16.4.1, and 16.5.0RC1 releases by the end of February 2025. Nonetheless, even with the patches accessible, there is already proof that a situation of exploitation had nearly started when reported attacks were seen in March 2025.
The exploitation of the vulnerability was not a widespread problem but rather a limited one, that was under control until the end of October 2025, when the vulnerability researcher group VulnCheck reported to have observed a large increase in the number of attacks. The investigators revealed that sophisticated two-stage attack chains were being utilized to install cryptocurrency mining malware on the hacked systems.
On the heels of VulnCheck's announcement, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) took the step of including CVE-2025-24893 in its list of known exploited vulnerabilities on October 30, 2025. The agency required that all federal entities enforce the necessary security measures by November 20, 2025.
Escalation: The RondoDox Campaign

Security researchers have been monitoring the situation very closely since early November, and they are reporting an increase in abuse attempt verging on the extreme. The threat intelligence data from VulnCheck has shown that activity related to exploitation reached the highest level on the 7th of November and continued with another significant wave on the 11th of November. This increase in activities is suggestive of a wider range of scanning and subsequent exploits which multiple threat actors pulled off.
RondoDox is the first amongst these adversaries and it’s considered a serious concern. The group was first noted to have started exploiting CVE-2025-24893 on November 3, 2025, RondoDox is a developing botnet that mainly concentrates on launching distributed denial-of-service (DDoS) attacks. It is a network of computers that operates by attacking the victim’s server with massive requests through the use of various channels like HTTP, UDP and TCP.
Security experts have detected that RondoDox has been gradually increasing the number of exploits it can use and, as quickly as any new vulnerability has been introduced, has been moving in to take control of that security gap and then, in turn, add those devices to its network. Through this aggressive capability development, the threat is perceived as a well-funded operation that possesses a high level of technical expertise.
Multi-Actor Threat Environment
The exploitation of CVE-2025-24893 has taken a path which is now described by VulnCheck’s Chief Technology Officer Jacob Baines as “the same old story: one attacker does it first, followed by many”. Just days after the first use of the vulnerability was noted, the researchers could see the same thing happening with botnets, cryptocurrency miners, and scanning tools used by the opportunistic.
In addition to RondoDox's botnet activities, other criminals have been seen taking advantage of the flaw for deploying Monero miners' cryptocurrency mining software, configured to connect with c3pool.org mining pools. Other patterns of exploitation include establishing reverse shells on the attacked systems and using Nuclei templates specifically designed for CVE-2025-24893 to conduct general reconnaissance activity.
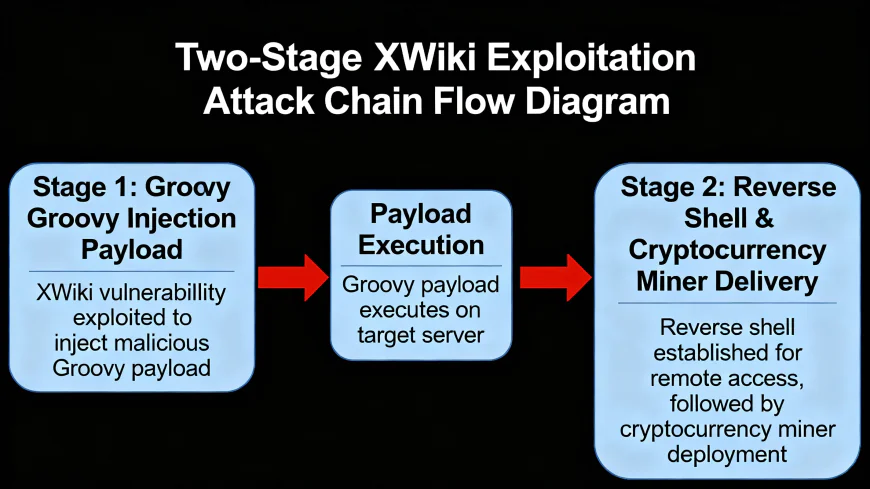
The VulnCheck research team has recorded one unusually detailed attack chain from Vietnam, which used a very clever two-pass exploitation workflow. During the first phase, the hijackers stage a downloader script by sending a malicious GET request that takes advantage of the template injection vulnerability with Groovy scripting features on the part of the attacker. This first payload uses a wget command to download malicious files into the target system's /tmp folder.
The staged method gives the attackers the ability to change payloads after the compromise and to check if the victim is connected before finally delivering the remaining malware. After that, the secondary scripts will then download and install UPX-packed binaries for the cryptocurrency mining, prepare the environment by stopping other mining processes, and launch the miner with pool-specific settings.
Geographic Distribution and Infrastructure
The attack traffic has been detected from different places and among them Vietnam and Venezuela were the most important. The hackers use a wide distribution of infrastructure which includes an instance of the secondary payload server operating through transfer.sh that serves the multiple stages of the attack chain.
A Honey Potting system of VulnCheck's Canary Intelligence is used to detect the exploitation attempts and it has captured hundreds of distinct attack attempts since late October. The data shows not only the scanning volume increase but also the clear evidence of multiple independent adversary groups using their own tools and techniques for the exploitation process.
Impact on Enterprise and Government Networks
The critical nature of CVE-2025-24893 exploitability across the board of affected systems significantly increases the risk for all the organizations that are using the vulnerable XWiki installations. Government and enterprise agencies that depend on the platform for knowledge management and collaboration will feel the brunt of this risk. Thesaurus maximum severity rating, and simple-exploitation conditions make it an easy target for the attackers ranging from the less-skilled to the most sophisticated ones.
For the attacked system, the results are not limited to the immediate malicious payload. Hacked users with arbitrary code execution can possibly get to the sensitive information, implement persistent access means, move around the network, and even interrupt important services. The cryptomining activities may lower the system's performance and increase the cost of computational power very significantly.
CISA by adding the vulnerability to its KEV catalog highlighted the importance of the danger to federal networks. The November 20 deadline for federal agency remediation shows the urgency of the need for security measures.
Detection and Mitigation Strategies
All XWiki installations should be upgraded without delay by security teams to the versions 15.10.11, 16.4.1, or 16.5.0RC1 and newer. Organizations that cannot upgrade right away should apply the fixes recommended by XWiki maintainers, which consist of altering Main.SolrSearchMacros to suitably sanitize the rawResponse macro with proper content type handling.
Apart from adopting the patch, the defenders must take up different protective measures. The outbound connections can be restricted to the known cryptocurrency mining pools through network segmentation, thus, minimizing the effect of successful attacks. The security teams should setup the detection rules that will target the specific infrastructure IP addresses and file hashes related to the known exploitation campaigns.
VulnCheck has disclosed the detailed indicators of compromise that consist of the file hashes for the tcrond cryptocurrency miner (SHA-1: 0b907eee9a85d39f8f0d7c503cc1f84a71c4de10 for the UPX-packed version) along with the attacker IPs like, 123.25.249.88 and 193.32.208.24. Organizations are recommended to feed these indicators to their security monitoring systems.
Keeping an eye on the /bin/get/Main/SolrSearch endpoint for intentionally suspicious requests especially the ones that are injecting Groovy code can serve as an early warning about exploitation attempts. The security information & event management (SIEM) systems should be set up to notify about the unusual activity patterns that are in line with the...two-stage attack technique.
Broader Implications for Vulnerability Management
The case of CVE-2025-24893 exploitation campaign brings to light the never-ending difficulties which are the result of organizational patching management practices. Even though the patches were already available since the end of February 2025, still a hundred to thousands of vulnerable instances which are Internet reachable remain there for months.
Jacob Baines from VulnCheck reiterated this phenomenon: "We saw within a few days from the start of the exploitation that botnets, miners, and opportunistic scanners were all taking advantage of the same vulnerability". The quick and widespread ability to exploit weaknesses after their discovery serves to confirm that the defenders at the modern cyber fronts have no longer the luxury of time.
The whole episode also puts a premium on the necessity of complete threat intelligence for an organization and not only reliance on official catalogs. By March 2025, VulnCheck had already included CVE-2025-24893 in its proprietary KEV database based on third-party exploitation evidence from Cyble, Shadow Server, and CrowdSec, thus, it was seven months ahead of CISA's official recognition. This early warning was a great opportunity for subscribing organizations to be properly informed about active threats beforehand.
Conclusion
The RondoDox's usage of CVE-2025-24893 is the latest incident in the long-standing security crisis around the XWiki products that has been affecting their users all over the world. As a result of continuous probing from different hacker groups, the opportunity for taking defensive measures is getting shorter day by day. Organizations that use XWiki must treat the removal of the vulnerability as an urgent matter and either install the patches or use compensating controls right away.
Thus, the discoveries made affirm the existence of the aforementioned cybersecurity best practices: keeping up with patch management processes, having thorough threat intelligence capabilities, network segmentation, and monitoring, and considering every publicly disclosed critical vulnerability quickly exploited by enemy groups as the rule of thumb. The present threat environment has made it such that the window between vulnerability disclosure and mass exploitation has virtually closed, thus leaving defenders with a very narrow margin for error.











































