New Vishing Attack Exploits Microsoft Teams and QuickAssist to Deploy .NET Malware
Attackers use Microsoft Teams Vishing to trick users into granting remote access via Quick Assist. This leads to the download of a trojanized .NET executable which deploys fileless malware into memory using .NET Reflection to evade detection.
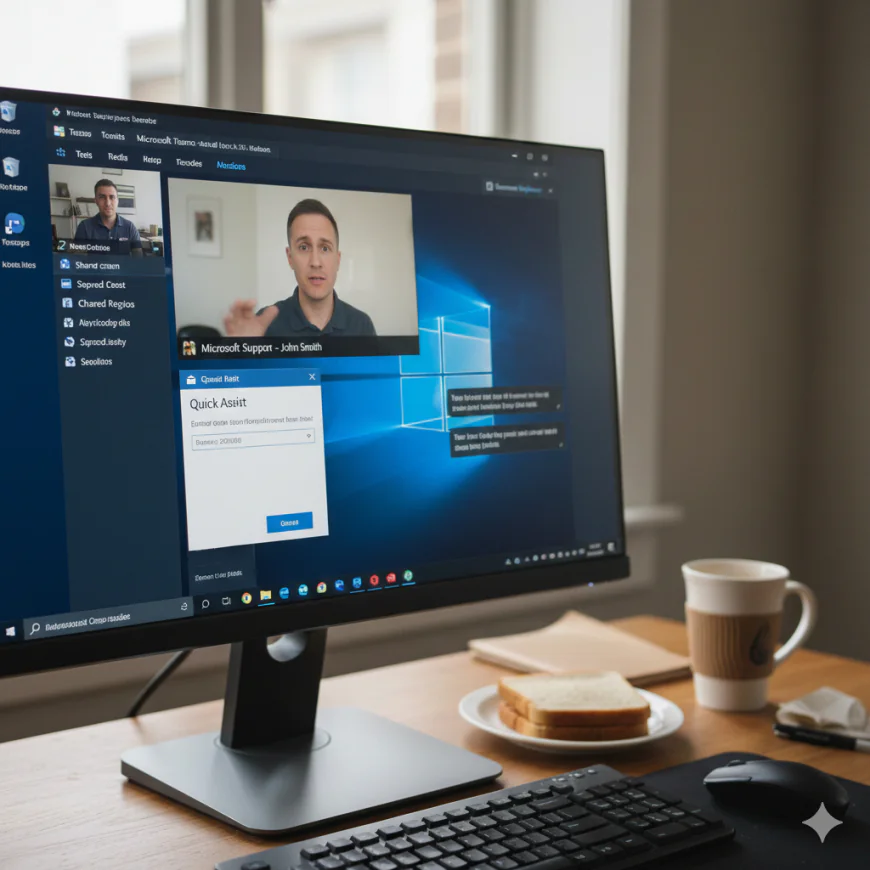
A complex vishing campaign has started that uses both social engineering and real Microsoft tools to set up command execution chains that lead to the deployment of .NET malware in multiple stages.
Security researchers have found a way for attackers to start by pretending to be IT workers and contacting victims through Microsoft Teams. The attack ends with fileless malware running through memory-based reflection techniques.
The infection starts with social engineering, where threat actors pretend to be Senior IT Staff by changing their display names in Microsoft Teams call notifications.
People who have been hurt get calls from what seem to be real internal IT support staff.
The attacker uses a carefully planned social engineering story to get the victim to open Windows Quick Assist, a real remote assistance tool that comes with Windows operating systems.
Once the victim starts Quick Assist, the attacker can get into the victim's computer remotely by pretending to be helping them with technical issues.
The user is sent to a bad website at ciscocyber[.]com/verify.php about 10 minutes after they get to this point.
At this point, the attacker makes a big change from using social engineering to using technical exploitation.
Putting malware on a computer and running it
The redirection installs "updater.exe," a trojanized executable that appears to be a real Windows system updater.
This is where the attack gets really bad. The executable is built as a .NET Core 8.0 wrapper with an embedded loader that can run without needing to save data to disk.
The loader.dll part controls the multi-stage payload delivery system. When it runs, it connects to the command-and-control infrastructure at jysync[.]info to get the encryption keys.
This way of managing keys separately makes it harder to find and analyze problems.
The loader then gets an encrypted payload from the same infrastructure and decrypts it using AES-CBC encryption and XOR obfuscation, which is a two-layered method that makes static analysis harder.
The last step of the attack chain uses .NET reflection to load the decrypted assembly directly into the memory of the running process without writing to disk.

This fileless execution method is a very effective way to get around traditional endpoint detection systems that rely on file monitoring and disk-based indicators of compromise.
The malware runs entirely in memory and can run any code with the same permissions as the person who started the first Quick Assist session.
What this means for security
This campaign shows how different types of attacks can work together, such as social engineering, misuse of legitimate administration tools, and advanced fileless execution techniques.
Using well-known apps like Microsoft Teams and Quick Assist makes people much less suspicious and gets around many network-level security controls.
The .NET Core wrapper method shows that the attackers are skilled at programming and know how modern application delivery systems work.
Companies should set up systems to monitor email and other forms of communication to look for impersonation attempts, enforce strict rules for remote assistance, and teach users how to check the identity of IT support staff before giving them access to the system.
To find this kind of fileless malware running on a network, you need endpoint detection and response solutions that can watch .NET runtime activity and process memory injection patterns.