Massive Russian-Linked Phishing Campaign Targets Travelers with 4,300 Fake Hotel Booking Sites
A cybercriminal operation among the Russian-speaking community has created more than 4,300 fake websites for hotels and travel bookings since February 2025, with the global market for sophisticated phishing scams that appear to be Booking.com, Expedia, Agoda, and Airbnb as its main target. The phishing kit changes the appearance of the pages according to the URL parameters, offers support for 43 languages, and uses fake CAPTCHA and support chat windows to collect credit card and personal data. The whole action indicates the concept of phishing as a service has evolved and thus attackers are able to perform mass credential theft at scale across the hospitality sector.

As per the research done by Netcraft, a large and sophisticated phishing attack has managed to fool travelers all over the world by way of its enormous and diverse network of fake hotel and travel booking sites. The operation, which is said to be Russian-speaking, has been capable of registering over 4,300 harmful domains since the beginning of 2025, thus making one of the year's most daring theft of credentials aimed at the hotel and travel industry.
The attack is mimicking the major travel providers - Booking.com, Expedia, Agoda, and Airbnb - plus at the same time standing in for hundreds of real and less-known luxurious hotels around the globe. Researchers found out that among the 4,344 domains related to the campaign, 685 domains, for instance, consist of the term "Booking," then followed by 18 with "Expedia," 13 with "Agoda," and 12 with "Airbnb," indicating that the attackers were deliberately aiming at high-traffic platforms that are often used by travelers.
"The ongoing operation has made use of cutting-edge phishing technology that modifies the view for site visitors based on a unique string in the URL path when the target first accesses the website," said Netcraft's security expert Andrew Brandt in an analysis that was published this month. He further said, "The modifications incorporate the logos of the leading brands in the online travel industry, such as Airbnb and Booking.com."
How the Attack Works
The scam starts with emails that come across as authentic, beseeching the prospective vacationers to confirm their hotel reservations. The emails usually say that booking confirmation must be done in 24 hours and take the recipients to click links that supposedly lead them to a travel confirmation page. However, instead of getting to the official booking sites, the victims are diverted through a complex network of redirects before they reach the counterfeit website.
The redirection system, which is a technical wonder, guides the victims through deserted websites that were registered years ago and free blogging sites like Blogspot before finally leading them to the real phishing page. This multi-level redirect method raises the chances that the bad domains will get past even the earliest detection by the security filters.
When the victim gets to the fake pages, they see screens that are very much like the real travel booking sites, with corporate logos, professional designs, and payment forms that are familiar. The phishing kit has an ingenious feature that is its "AD_CODE" parameter system. Each specific string value in the URL activates different branding elements, allowing the same infrastructure to impersonate several brands and individual hotels at the same time without needing distinct physical servers for each fraud site.
The pages are also equipped with the ability to be translated into 43 languages, making the attackers capable of really targeting a global victim population. Besides, every site has a false "online help chat" window which, through the use of pseudo-technical support language, alongside fake CAPTCHA challenges that impersonate Cloudflare's legitimate security verification system, provides the victims with confidence.
Technical Architecture and Data Extraction
The fake site processes the victim's payments in the background, after they have entered their payment details that consist of the name of the cardholder, the card number, the CVV code, and the expiration date. On the other hand, the support chat window is urging the users to do the "3D Secure verification," which is a social engineering tactic that leads the victims to think that their transactions are secure and legitimate.
The petty phishing trick uses a technology of persistent cookies that can help it to keep its fake images consistent throughout one victim's browsing session. The values of AD_CODE and the "D_TYPE" are both stored in the cookies, ensuring that the branding of the platform being impersonated is the same for all the subsequent pages. The researchers found out that using the same AD_CODE value in different phishing domains within the cluster impersonates the same brand, whereas using different AD_CODE values on the same domain yields different impersonations targeting various hotels.
The phishing kit working behind the scenes is always on the lookout for the users' actions, taking down their typing, the card information that they have submitted, and their chat messages for sending to the systems controlled by the attackers. The level of technical complexity of this data harvesting system reveals a firm that is very well-funded, still, as their main intention is to get every victim's financial as well as personal information.
Scale and Registration Patterns
The threat actors have shown an amazing operational capability by registering domains at an average of 10 to 65 per week during the entire period of their campaign that started in February 2025. However, one incident on March 20, 2025, when the attackers registered at least 511 domains in just one day, made the operation's scale visible; this was a synchronized mass registration that probably marked the beginning of a significant attack phase or a seasonal event.
The domain naming practices of the adversaries have very consistent patterns that make the whole thing even more misleading. The use of common words like "confirmation," "booking," "guestcheck," "guestverify," "cardverify," and "reservation" in the domain names gives an impression of legitimacy that is just superficial. A good number of domains even take the names of specific upscale and boutique hotels in different parts of the world including Nepal, Germany, Greece, Spain, and Brazil which could either mean targeted research or automated scraping of hotel databases.
Netcraft analysts have found out that the criminals have a preference for a limited number of domain registrars for the bulk of their registrations: WebNIC, Public Domain Registry, Atak Domain Bilgi Teknolojileri A.S., and MAT BAO Corporation. They also use the new gTLDs such as .world, .sale, and .help which may have easier monitoring for abuse compared to the traditional domains such as .com or .org, and the like.
Attribution and Phishing-as-a-Service Implications
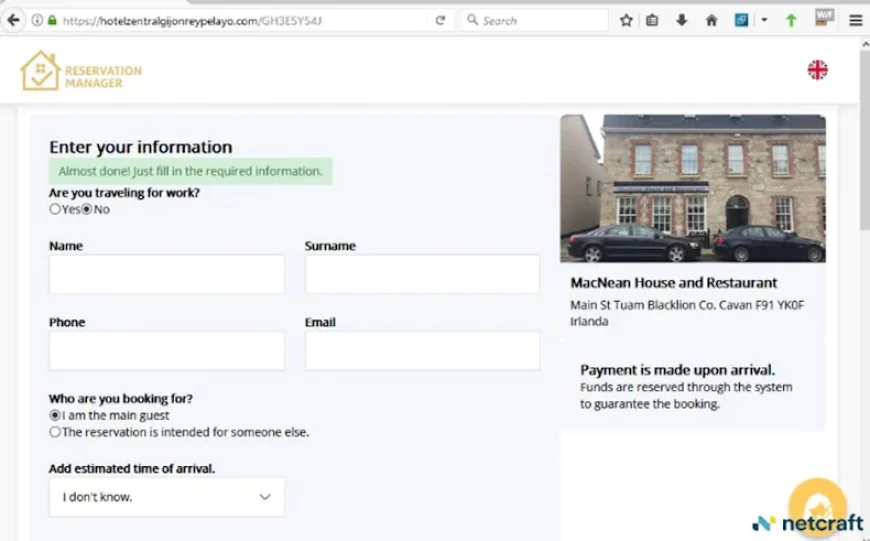
The accusation against Russian-speaking threat actors is based on several factors found in the source code of the phishing kit. The HTML files are filled with extensive Russian language comments and debugger output, while the development notes and variable names give away the presence of Russian linguistic patterns all over the project. Researchers point out that even if the presence of Russian language might mean the attackers' actual place of action, it might also have been a way to lure potential buyers of the phishing kit in criminal forums by customizing it to the Russian-speaking market.
The above reasoning may lead to the conclusion that the operation is not simply a single threat group but rather a phishing-as-a-service (PhaaS) offering. The process of phishing as well as its kit being cheap, customizable has completely changed the threat landscape and has made it possible for even the criminals with very little technical skills to mount large-scale campaigns. This kit's automation is a perfect example of this worrying trend, the speed of deployment of phishing attacks has increased, detection has become more difficult, and replication across different verticals and geographies has become exponentially easier.
Connection to Broader Hospitality Threats
This campaign is part of the general increase in phishing attacks which the hospitality industry has been facing. The operating French cybersecurity company Sekoia has cautioned that there are several phishing setups running concurrently which are using ClickFix-like pages for stealing hotel managers' passwords and then the criminals use the stolen passwords to access hotel systems and send customers fake reservation emails confirming their bookings. Sekoia shared, among other things, the domain indicators "guestverifiy5313-booking[.]com/67122859" and they were notably matched by the domain pattern registered by this campaign (for instance, "verifyguets71561-booking[.]com"), so it is quite likely that these two activity clusters are part of a coordinated operation.
At the same time, phishing activities on a massive scale have taken place impersonating major computer technology companies such as Microsoft and Adobe, as well as logistics companies like FedEx and DHL. The method is similar - HTML attachments are sent out via emails that when opened show a fake login page, while JavaScript code running in the background captures the credentials and sends them off to the attackers via Telegram bots.
Implications for Travelers and Organizations
The size and complexity of this operation serve as a strong reminder to both individual travelers and hospitality organizations about the necessity of being vigilant. The fact that the campaign was able to reach 43 languages and target luxury hotels worldwide shows the attackers are purposely trying to cover a large area and grab all the victims.
The travel industry should require multi-factor authentication for legitimate booking platform accounts, check URLs just before entering payment information, and train the workers to identify phishing cues such as strange email addresses, pressing tone, and requests for extra payment verification not included in the regular booking flow.
The risk is still present, and it is changing. Latest news says that the system is still working; new domains are being registered frequently to take the place of the ones that have been shut down. Organizations and individuals should be extra careful with unanswered booking confirmation emails and should call hotels directly using known contact numbers instead of clicking on links provided in the emails.











































