Dark Web Monitoring: Should You Check If Your Data Is Being Sold?
Dark web monitoring continuously scans hidden internet marketplaces to detect stolen personal information. Get alerts when your data appears online so you can take immediate action to prevent identity theft and fraud.

Introduction
The digital world of today makes it very likely that your personal data will get into the wrong hands. Data breaches that leak private info such as email addresses, passwords, Social Security numbers, and even credit card information occur every year, affecting millions of people. A considerable number of these breaches lead to a black market where the stolen data is sold for the highest price. The dilemma that numerous consumers and businesses are tackling is if they should be keeping an eye on the dark web for their information's sale. In this article, we are going to discuss monitoring of the dark web, its operation, significance, and its practicality for you as a user.
What Is The Dark Web? Why it matters?
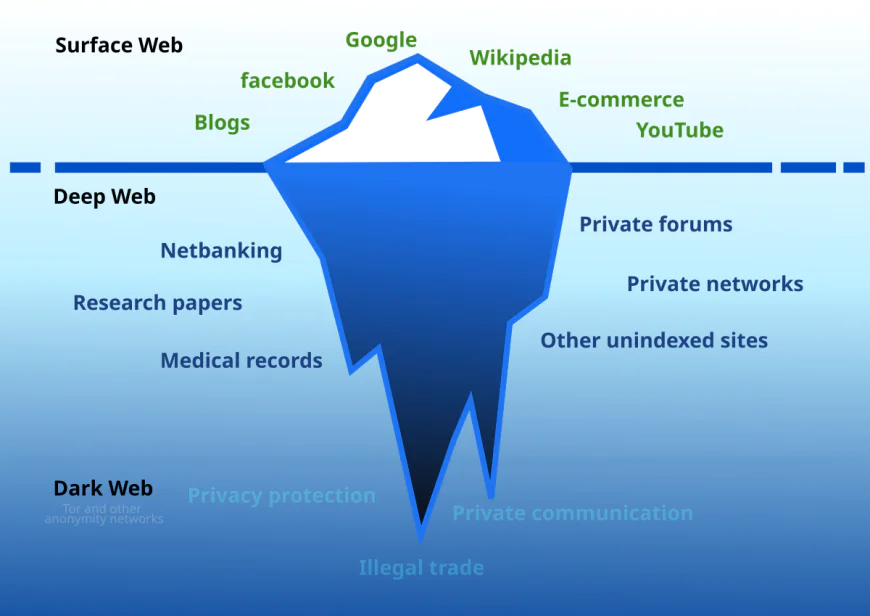
The dark web is the concealed section of the internet that is only accessible through special software. The dark web, where Google or Bing are not used, works with total anonymity that draws to it the surfers of the net of illegal activities. It has turned into a trading place where the hackers buy and sell stolen data openly.
The illegal activities include the exchange of login information, credit card numbers, Social Security numbers, medical records, and business data. The biggest dark web markets such as Abacus, STYX, and Russian Market are responsible for millions of these daily transactions. Criminals are the ones who work with total anonymity and it is this very fact that makes law enforcement action difficult.
How Dark Web Monitoring Works

Dark web monitoring is a continuous and proactive security measure that goes in-depth into the hidden corners of the internet to catch if the information about you is being sold or talked about. It is like an early warning system for theft and fraud.
You need to feed the monitoring service with your personal data such as email addresses, phone numbers, Social Security numbers, and credit card information. The service employs advanced tools to sweep dark web markets, forums, and secret channels where the sale of stolen data is done. If your information is spotted, you will be immediately informed along with the description of what has been found and the location of the finding.
The free dark web scanners will only check your email against the known breaches but they have a limitation of sources. The paid services like Aura, LifeLock, and Experian not only monitor more than 130 pieces of personal information but also have access to a wider range of dark web sources. They will also provide additional services such as identity theft insurance and fraud resolution assistance.
The Magnitude of Data Breaches in Today's World
To grasp the significance of dark web monitoring, one must first consider the scale of data breaches. In 2021, about 45 percent of businesses in the United States experienced a data breach and the trend is still going up. Each day brings new data breaches that put thousands or even millions of records at risk.
Major corporations are said to have been losing their usernames and passwords and these are just some of the transactions happening on the dark web through 2025. For example, the selling of records from a German electronics firm for the price of 250 dollars in January was one such instance. Monthly selling of credentials from an Indian educational technology firm for 800 dollars in March was another example. RDP access to an African government agency for 1,500 dollars was the highest auction price in June. The Tor network by itself is estimated to have about 2.7 million users logging in and out every day.
Stolen data is a criminal tool and not just a means of robbery. Cybercriminals perpetrate ransomware attacks, perform phishing, and carry out account takeovers with this data. Consequently, the dark web has turned into a backbone supporting the whole cybercrime industry.
Benefits of Dark Web Monitoring
Dark web monitoring is a very advantageous service for both people and businesses.
Early Detection and Quick Action
The main advantage is an immediate alert if your data reaches the dark web. It is much better not to know that your data was stolen months or years back when changes are already reflected in your credit report. The early alert gives you an opportunity to alter passwords, reach out to your bank, set up fraud alerts, and keep a close watch on accounts, all before the criminals can actually use your data.
Preventing Identity Theft
Identity theft is a crime and it can cause a lot of damage. A criminal holding your Social Security number and home address can create credit accounts in your name, take loans, file false taxes, or make unauthorized purchases. The affected persons will take hundreds of hours to sort out the issues, and in the process, they will lose their credit scores and financial reputation. Dark web monitoring will not stop the theft, but it will be the one that will give criminals less time to use your data before you realize it.
Cost Savings
Identity theft and data breaches have a huge financial impact. Recovery from a data breach costs companies millions of dollars. For a single person, the theft of an identity not only leads to direct loss of money but also to long-term damage of credit which makes it really hard to borrow for many years later.
Dark web monitoring can't be called an expense when compared to the possible damage. Free scanners don't cost anything. The monthly fee for paid services usually ranges from 5 to 30 US dollars. This little investment can lead to the saving of thousands of dollars in recovery costs.
Regulatory Compliance
The healthcare, finance, and legal industries are under heavy scrutiny regarding data protection. Strict regulations like GDPR, HIPAA, and PCI-DSS not only impose but also give out large fines for breaches and non-timely detection of them. Dark web monitoring supports organizations in fulfilling their compliance obligations by rapidly spotting the breaches thus enabling them to promptly inform those affected and rectify the issue.
Limitations to Consider
Dark web monitoring, spite its real benefits, has limitations which we need to understand.
Incomplete Coverage
Monitoring services are not capable of scanning every part of the dark web. The dark web is in the state of flux, the criminal forums are appearing, disappearing, and moving around. There is no such service that can claim to cover 100 percent of dark web activity. It's possible for your data to be on the dark web but not identified by your monitoring service.
Already Compromised Data
Dark web monitoring is a reactive measure, rather than a preventive one. It cannot prevent the breaches that have already occurred. It merely informs you that the data has been compromised. This is why monitoring is most effective when combined with other security practices, such as using strong passwords, two-factor authentication, keeping software updated, and phishing awareness.
Requires Your Action
Alerts mention issues but do not solve them. It is necessary for you to react by changing passwords, getting in touch with banks, making fraud notifications, and checking credit reports. The service detects the danger, but you take care of the reaction.
Quality Varies
Free scanning tools are not very powerful, and they only check a small number of sources. For paid services, one has to do quite a bit of research to pinpoint the trustworthy providers. Moreover, not every provider has the same access to the dark web or offers the same level of customer support and fraud resolution.
Who Should Monitor?
Monitoring would be beneficial for everyone who is online, but some users are at higher risk than others. Senior management and corporate leaders are the most profitable targets. People from the legal or medical sectors, who are dealing with very confidential information, require safeguarding. Cybersecurity resources are usually not available for small companies that keep their customers' data online. Employees who work from home and use their own gadgets are also vulnerable. Parents fear that their children's identities may get stolen and not be discovered for a long time. Anyone who was informed about a data breach in the past should be very mindful of the monitoring option.
Getting Started
Utilize free services first, such as HaveIBeenPwned, Aura, Google's dark web report, or Experian's free scan. These services allow you to easily see if your email was part of any known data breaches.
For wide-ranging surveillance, consider researching the paid services. You can make comparisons based on the kinds of information they keep an eye on, dark web sources they have access to, the level of customer support, the identity theft insurance offered, and the prices. Consult reviews from tech websites and look for consumer protection ratings.
Pick out the service that fits both your requirements and your financial plan. Be clear about the meanings of the alerts and prepare your response. For single users, the monitoring would include email addresses, Social Security numbers, account numbers, and driver's licenses. Deciding on a response before alerts come is wise so that you can react swiftly.
Conclusion
Is it advisable to check if your data is on the dark web? For the majority of people living in an environment surrounded by constant breaches, the answer is a definite yes. The occurrence of numerous breaches, the existence of dark web markets, and the low cost of monitoring combined make it worth the effort.
As a minimum, run a free scan that takes only minutes and is absolutely free. If you deal with sensitive financial data, work in regulated industries, or have been a victim of past breaches, then paid monitoring definitely deserves your careful consideration.
Dark web monitoring can never be a complete security solution by itself. But, it can play a crucial role in a broader strategy that involves strong passwords, two-factor authentication, and cybersecurity awareness; in fact, it serves as an early warning system catching threats before serious damage occurs. In a world where breaches are almost a given, that additional awareness and early detection can really make a difference in self-protection.









































