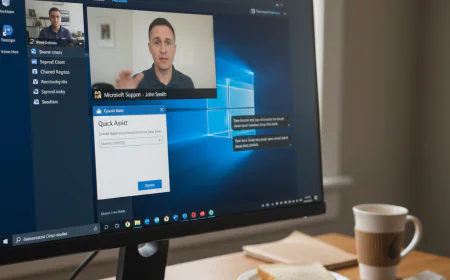
1.5 Millions Devices Under Threat: Massive Cyber Attack
A global cyber attack threatens over 1.5 billion devices, exploiting critical security vulnerabilities across major technology systems. Learn how hackers use SMS phishing, fake websites, insider threats, and supply chain attacks to compromise data, and discover strategies organizations are using to defend against this unprecedented cybersecurity crisis.

In an unprecedented cyber attack news development that has been sent to shockwaves through the global technology landscape, cybersecurity insiders have revealed over 1.5 billion devices face close threats from sophisticated attack vectors targeting fundamental security infrastructure. This isthe massive cyber attack news story represents one of the most significant cybersecurity breach news events of 2024, with security researchers issuing urgent warnings about coordinate campaigns affecting millions of users worldwide.
The scale of this cyber threat news can’t be ignored. As cybersecurity insiders report are shown that threat hackers have developed advanced procedure to stealing credentials across multiple devices. These cyber threat news develop highlight the evolving nature of the modern cybersecurity threats, where the standard security methods fail to protect against the opposition are getting smart and more skilled.
Critical Device Security Weaknesses Expose Billions of Users Ecosystem
The latest or recent cyber attack news reveals that security researchers at multiple cybersecurity insiders organizations have identified critical security weaknesses affecting the worldest largest technologies ecosystems. This cybersecurity breach threat news comes as threat intelligence analysis warn that attackers had been developed the new techniques or technologies to bypass standard security measures and exfiltrating or stealing confidential information.
Cybersecurity insiders report that the hackers methodology involves advanced social engineering action combined with technical utilize that target fundamental weaknesses in device authentication systems. These cyber attack threat news develops show how attackers can support apparently legal communications to compromise with user accounts and access the sensitive information stored on billions of devices all over the world.
The cyber attack threat news reveals that attackers have been deploying the advance scam that incorporate multiple layers of mislead to appear legally to unconcious users. Cybersecurity insiders note about the attacks are represents a significantly adaption in threat actor capabilities, or combining technically experienced with psychological manipulation techniques.

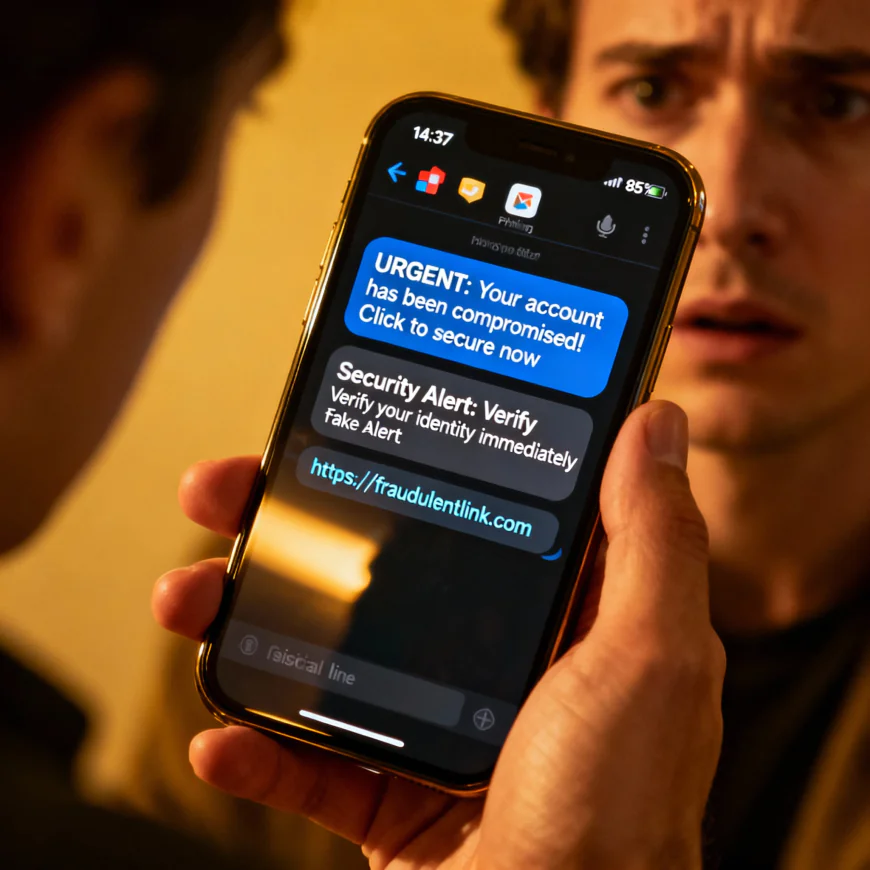
SMS or Text Based Attack Targeting the Millions of Users Accounts
As per the latest cyber attack threat news, the hackers have created an elaborate text-based scam that targets users' computers by means of the text message which is intended to look like a legal security notification. Cybersecurity sources claim that these cyber attack threat news cases are all about the careful manipulation of the words in the messages that request the users to the malicious sites that are intended for stealing the authentication credentials. According to the cybersecurity breach news, users have been started to receive such SMS in July 2024, and the cybersecurity insiders have been following the deceptive messages and distributing them across different geographic areas. These cyber attack news events have shown that the attackers have used CAPTCHA verification systems on their fake websites to make their phishing operations appear more legitimate. Cybersecurity insiders looking into these cyber attack news incidents say that the malicious text messages are usually sent with an urgent request to the recipient to visit a scam site that has a layout very similar to that of the original and is very hard to recognize as a trap. The cybersecurity breach news mentions that unchecked attacks lead to taking over the entire account that allows the hackers to see personal data, financial information, and even the control of the device used to be granted to them.
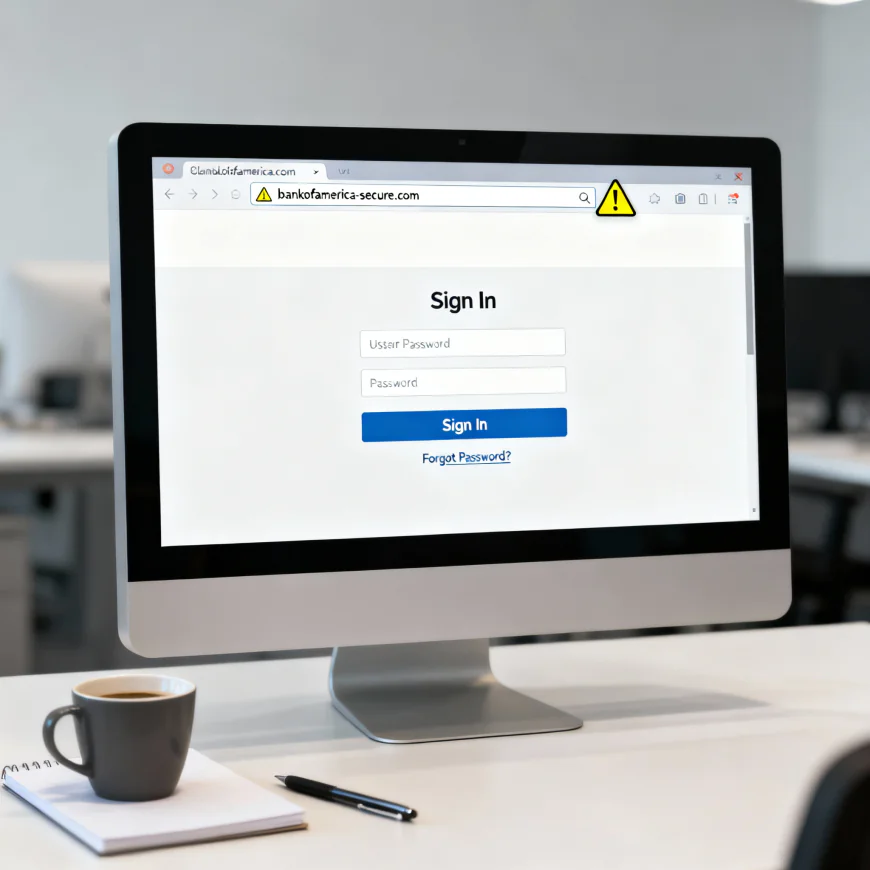
Sophisticated Website Impersonation Techniques
The cyber attack news indicates that the criminals have come up with very sophisticated methods to impersonate websites and thus they are able to create an almost identical copy of a legitimate login page. According to cybersecurity sources, these fake websites use not only the original design elements but also the interactive features which make them so hard for the users to recognize as malicious.
As per the reports regarding the cybersecurity breach, the imitation sites in this cyber attack incident are said to have such outdated interface designs that in a way they have gained the trust of the users by being linked to the security systems of the older time. Cybersecurity experts say that this kind of psychological manipulation displays a very good grasp of user behavior patterns. Impersonation sites could be reached via both desktop and mobile browsers as mentioned in the cyber attack news which has consequently increased the number of possible victims to a great extent. Experts in the field of cybersecurity have pointed out that this cross-platform access is a complete reversal of the trend in which most mobile-oriented phishing campaigns are confined, thus, showing the attackers' determination to spread their operations as far as possible.
Global Aviation Industry Faces Unprecedented Cyber Attack News Crisis
The cyber attack news crisis has hit the global aviation industry like a quick and severe blow struck. The mentioned situation with the American Airlines hacked case is only one part of the whole cyber attack news crisis, which has affected the aviation sector in its entirety. The attack again airline industry and aviation airports targets has confirmed that a very infamous cybercriminal gang that is referred to as "Scattered Spider" has attacked airline networks in a planned and systematic fashion all over North America. As per cybersecurity insiders, the group has been able to infiltrate various airline systems which is a sign of their extensive planning and the high level of coordination of their attack methodologies. The hacking news coming from the aviation industry indicates that these attacks were executed during the busiest travel times which means that the attackers had planned their activities very well to not only disrupt the operations but also make their presence felt financially, which is a major objective of their attacks. The cyber attack news reveals that the attackers deliberately chose the summer travel season for their campaigns, knowing full well that service disruptions would affect millions of travelers around the globe.

Scattered Spider Group Targets Critical Infrastructure
Cyber attack news brings to light the fact that Scattered Spider has become one of the deadliest cybercriminal groups working, with the help of security insiders indicating them as the basis of several major breaches in different sectors. This security breach news development marks a big step up in the level of threat actor capabilities and coordination. According to cybersecurity insiders, Scattered Spider makes use of advanced social engineering techniques in its initial access to the target networks, often posing as the company's real IT staff or a contractor who needs to get through the multi-factor authentication system. The cyber attack news also reports that once they are able to get footprint inside the target networks, the group is capable of launching a ransomware attack in less than one hour after the initial compromise. The news about the cyber attack achievements of the Scattered Spider group shows that the group has been able to maintain a high-level of persistence and lateral movement within the hacked networks. The Cybersecurity experts affirm the group’s speedy privilege escalation and maintaining constantly through their activities being the most significant factors for their success.

Airport Infrastructure Becomes Primary Target
The recent cyber attacks news has brought to light the major weaknesses in the airport infrastructure systems, with the insiders from the cybersecurity industry saying that the attacks have been successful in the major international airports across the globe. The news of the cybersecurity breach indicates that the aforementioned attacks have been focused on the indispensable operational systems like, for instance, the flight information displays, ticketing systems, and passenger processing infrastructure. According to cybersecurity insiders who are analyzing these cyber attack news events, the perpetrators of the airport attacks have used both ransomware and distributed denial-of-service (DDoS) methods to create the maximum disruption to the operations. The cyber attack news informs that the attackers have been asking for ransoms running into millions while, at the same time, causing disruptions in the essential passenger services. The cybersecurity breach news from the airport attacks shows how the vulnerabilities in the critical infrastructures can lead to operational failures of a large scale affecting thousands of travelers at the same time. Cybersecurity insiders have pointed out that these incidents are a reflection of the interdependence of the modern aviation systems and their vulnerability to organized cyber attacks.

Enterprise Security Landscape Faces Massive Insider Threat Surge
With the news of external cyber attacks hitting the headlines, on the other hand, insiders in cybersecurity have reported an enormous rise in the number of incidents related to insider threats. About 83% of organizations have acknowledged at least one insider attack occurrence in 2024. This cybersecurity breach news is a major milestone in recognizing the negative forces, as the internal staff are becoming more and more important in the list of security breaches. The cyber attack news with insider threats has indicated that already compromised organizations have their attack frequencies multiplied by up to 500% compared to the years before. Cybersecurity insiders claim that the increase in attacks is both because of better detection and the existence of insider threats across the board in different industries. The analysis of cybersecurity breach news has come to the conclusion that the insider threat has become a broad category covering all sorts of attack vectors, including credential stealing, privilege misuse, employee negligence, and even malice. The cyber attack news shows that the internal threats can sometimes be even more dangerous than external ones as they easily harvest the perimeter security controls.

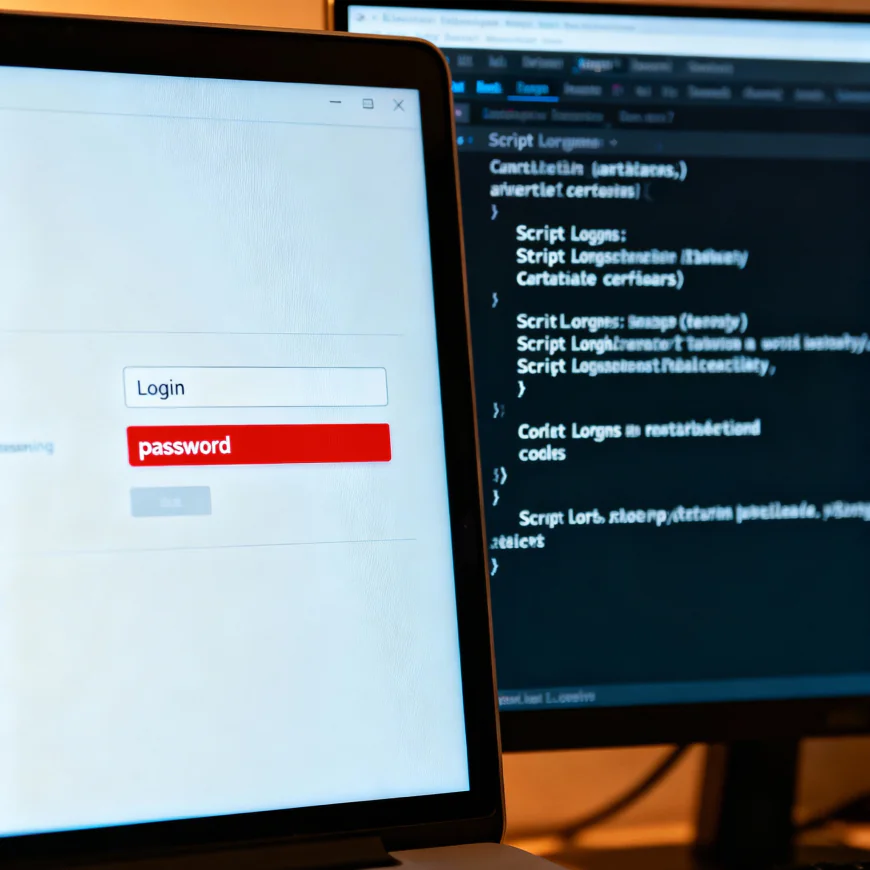
Credential Theft Emerges as Primary Attack Vector
Cybersecurity specialists have found through their analysis of the most recent cyber attack news trends that credential theft has emerged as the primary technique for unauthorized access to organizational systems not only by external but also by internal threat actors. This development in the cybersecurity breach news is a direct consequence of the escalating sophistication of social engineering attacks, which have shifted from generic phishing to impersonating trusted sources and even coworkers in order to collect employee credentials. The cyber attack news suggests that the perpetrators are using a variety of means to acquire user credentials, such as social engineering, brute force, and credential stuffing attacks. Security experts observe that once the intruders get hold of the passwords, they can sneak in and out of the systems for a long time without being caught. Cybersecurity breach news indicates that credential-based attacks lead to the highest data exfiltrations, as the intruders with access rights can unnoticeably and slowly drain the targeted data over time. Incidents that are the subject of the cyber attack news emphasize the necessity of strong credential management and monitoring systems.
Financial Sector Faces Coordinated Insider Attacks
Recent cyber attack news revealed that a major fraud operation using insiders was executed in financial institutions, cybersecurity insiders informed that data of clients was being sold to fraudsters by bank staff through encrypted channels. The hacking incident is seen as a highly technical insider threat due to the presence of both internal access and external criminals. Insiders on the cybersecurity front have traced these cyber attack news incidents back to low-paid workers, who on the one hand have access to the system, and on the other hand have been secretly routing and selling customer data to fraudsters targeting the vulnerable. The cyber attack report has already indicated that the criminals’ activities have actually been benefiting a whole cluster of banks. With respect to the latest cybersecurity breach news, the financial investigations have suggested that the fraudsters have built quite an intricate system of protection against detection through the main monitoring systems. Cybersecurity insiders say that the fraudsters often engage in simultaneous activities in different institutions which makes the job very difficult for law enforcement and regulators.
Global Data Breach Statistics Reveal Unprecedented Scale
According to a compiled collection of the most recent cyber attack news, there were 49 cyber attacks and data breaches reported to the public globally during the month of September of the year 2025, and cybersecurity insiders have been following the records and confirming that the exposure was almost 2 million records and potential one billion and five hundred million records. This news has made up one of the largest monthly counts in the history of cybersecurity. Insiders in the cybersecurity sector who are analyzing the statistics of the cyber attacks news claim that the real extent of the data being exposed might be much more than the confirmed figures because so often the companies that suffer the security incidents take long before they publicly disclose it as they conduct their internal investigations. Thus, the news of the cybersecurity breach suggests that actual exposure figures might be much higher than the reported ones. The news about the cyber attacks indicated that the major supply chain hacks, operating ransomware campaigns, and penetrating government agencies were some of the incidents that happened during September of 2025. The cybersecurity experts pointed out that this wide-ranging portfolio of attacks reflects the variety of threat actors who are operating at the moment and their different tactical methods.

Supply Chain Attacks Intensify Across Multiple Sectors
A recent cyber attack saga has highlighted a dramatic rise in supply chain attacks, with the insiders in the cybersecurity field saying that in order to be able to access several downstream organizations at a time, the attackers have changed their focus to third-party service providers. The cybersecurity breach news indicates that the adoption of those more efficient methodologies for attacking is becoming the norm. As per the cybersecurity insiders observing these trends in cyber attack news, one successful compromise in the supply chain can make hundreds of organizations vulnerable. The cyber attack news has it that the hackers have started to exploit OAuth tokens and compromised CI/CD pipelines, thus extending their reach more than ever before. According to the cybersecurity breach news, attackers have become more and more skillful when it comes to the supply chain and have even devised specialized methods for taking advantage of the trust relationships between organizations and their tech vendors. Insiders from the cybersecurity world assert that the aforementioned attacks are seldom detected as they use legitimate access channels to gain prolonged periods of silence.

Critical Infrastructure Vulnerability Assessments
The news on cyber attacks has brought to light the major insecurities that are present in the current infrastructure systems, among which are the healthcare facilities, the educational institutions, and the government agencies that have reported successful attacks. This incident of cybersecurity breach is evidence of the wide-ranging targeting strategies of the current threat actors. According to cybersecurity experts who are monitoring the infrastructure cyber attack news, one of the main arteries of the attackers is the systems that deal with sensitive personal information, especially those connected with children and other vulnerable groups. The cyber attack news also points out that these attacks are characterized by a huge public response and regulatory attention. The cybersecurity breach news in the case of the infrastructure attacks reveals that the actors are intentionally attacking the systems when there is not much staff or the operational capacity is low. The cybersecurity experts have indicated that professional threat actors have made holiday and other times of reduced organizational vigilance their preferred attack windows.
Advanced Threat Actor Methodologies and Attribution
Cybersecurity experts who look into the present-day trends in cyber attack news have noticed an important change in how the hackers operate, with the attackers showing more and more skill in both the technical side and the security measures for communications. This cybersecurity breach news to say the least, points to the fact that innovative threats have born out of great masterminds who now use a variety of methods to their advantage for one purpose—the fastest and most efficient damage done. The cyber attack news tells us that modern threat actors are making good use of very sophisticated reconnaissance tactics to uncover and take advantage of previously unknown weaknesses in target systems. Insiders in the cybersecurity field confirm that such reconnaissance actions often consist of a thorough analysis of social media, a research on public records, andmapping the technical infrastructure. Cybersecurity breach news analysis shows that the winning attack campaigns are more and more frequently involving the aspects of timing and coordination which are so carefully planned as to have maximum operational impact and at the same time minimum risk of detection. The cyber attack news gives the picture of having threat actors become more tactical in their selection of targets and timing of attack, entrenched in the periods when companies are the most vulnerable.

Multi-Vector Attack Coordination
The news about recent cyber attacks has revealed that there are very sophisticated multi-vector attack campaigns that mix up the use of traditional technical exploits with the application of advanced social engineering techniques. Insider information from the cybersecurity industry indicates that using these combined approaches has greatly improved the success rates of attacks by taking advantage of both technical flaws and human psyche at the same time. Cybersecurity insiders who are following the developments reported in these cyber attack news have pointed out that multi-vector attacks very often start with a long intelligence gathering phase which may last several months before the actual exploitation happens. The cyber attack news discloses that employing this method of the attacker being patient allows him to realize the most favorable attack vectors and timing for inflicting the highest impact. The cybersecurity breach news is suggesting that in the case of coordinated attack campaigns, there is a high probability that several groups of threat actors are involved in the attacks and they work together by sharing their intelligence and resources in order to reach a common goal. Outsiders in the cybersecurity field have stated that these partnerships among the criminals mark a notable advance in the organization of the cybercriminal ecosystem.
Zero-Day Exploitation Trends
The news about recent cyber attacks has revealed that there are very sophisticated multi-vector attack campaigns that mix up the use of traditional technical exploits with the application of advanced social engineering techniques. Insider information from the cybersecurity industry indicates that using these combined approaches has greatly improved the success rates of attacks by taking advantage of both technical flaws and human psyche at the same time. Cybersecurity insiders who are following the developments reported in these cyber attack news have pointed out that multi-vector attacks very often start with a long intelligence gathering phase which may last several months before the actual exploitation happens. The cyber attack news discloses that employing this method of the attacker being patient allows him to realize the most favorable attack vectors and timing for inflicting the highest impact. The cybersecurity breach news is suggesting that in the case of coordinated attack campaigns, there is a high probability that several groups of threat actors are involved in the attacks and they work together by sharing their intelligence and resources in order to reach a common goal. Outsiders in the cybersecurity field have stated that these partnerships among the criminals mark a notable advance in the organization of the cybercriminal ecosystem.
Organizational Defense Strategy Evolution
Increasing cyber attacks news, the security experts say, have compelled organizations across the globe to change their security policies drastically in order to cope with the new threat scenario. This cyber attack news indicates that there is a growing acceptance of the fact that traditional security models based on the perimeter are not capable anymore of stopping the attacks of modern times. Experts in the field have observed a significant increase in the deployment of behavioral monitoring systems and anomaly detection tools as response to cyber attack news events. The news about cyber attacks reveals that organizations now prefer to invest in threat hunting, continuous monitoring and security measures in advance rather than waiting for the attacks to happen and then responding. The cybersecurity news report states that organizations which have faced or are facing the attacks with success have set up complete security frameworks which take care not only of the technical vulnerabilities but also of the human errors causing security incidents. The experts believe that this overall strategy indicates that we are beginning to understand the difficult nature of the modern security challenges better.
Zero-Trust Architecture Implementation
The latest cyber attack news has been a major factor in accelerating the adoption of zero-trust architecture principles by organizations. Cybersecurity experts have revealed that comprehensive verification and monitoring systems are being widely implemented. This breach in cybersecurity news marks a significant transition from the old way of using security based on trust to continuous approaches of verification. Those insiders familiar with the zero-trust implementations are saying that organizations are increasingly considering all network traffic and user activities as potentially harmful until they are proved otherwise. The news about the cyber attack has brought a lot of skepticism and such an approach has already proved to be successful in spotting and stopping different types of attacks. superblocks + 1 The recent events concerning the cybersecurity breach and zero-trust deployments detail that a successful implementation undergoes not only a significant change in the organization’s culture but also an overhaul of the technical infrastructure. According to cybersecurity insiders, the most successful zero-trust programs are built on technology solutions coupled with a widespread user education and training initiative.

Artificial Intelligence in Threat Detection
Cybersecurity experts monitoring the trends of current cyber attack news are reporting that the use of artificial intelligence and machine learning systems for threat detection and response capabilities has increased. This incident of cybersecurity breach news bears out the fact that organizations are trying to match the levels of sophistication that modern threat actors have. The cyber attack news has shown that the AI-based security systems have been particularly effective in catching the subtle differences and patterns that the human analysts might miss during their usual monitoring. Cybersecurity professionals claim that these systems have unerringly pinpointed the coming unknown attack routes and the behaviors of the adversaries. Cybersecurity breach news evaluation implies that the success of AI security applications depends on large-scale training data and constant updates to keep their effectiveness against changing threat landscapes. The cyber attack news suggests that organizations committed to acquiring AI security capabilities are achieving lighter than before detection of threats and speedier response times.
Regulatory and Compliance Landscape Evolution
The news events of the most recent cyber attacks with unprecedented scale have led the worldwide regulatory authorities to create new rules for the cybersecurity governance and incident related response requirements. Reportedly, cybersecurity insiders have said that the government agencies are bringing forth tougher data protection requirements and disclosure of incidents, basically responding to the growing sophistication of the threats. The news analysis of the cybersecurity breaches shows the regulatory agencies are changing their approach to cybersecurity from considering it merely a voluntary organizational enhancement to regarding it as a basic infrastructure protection requirement. The recent news about the cyber attacks has indicated that this transition is a reflection of the growing acknowledgment of the cyber security's role in economic stability and national security. Cybersecurity insiders who analyze the regulatory developments report that there is a growing number of government agencies and private sector organizations working together to tackle the common cybersecurity issues. The news regarding the cyber attacks showcases that this joint effort marks a big step forward from the earlier regulatory approaches which mostly considered cybersecurity a private sector issue.
International Cooperation Initiatives
The news events of the most recent cyber attacks with unprecedented scale have led the worldwide regulatory authorities to create new rules for the cybersecurity governance and incident related response requirements. Reportedly, cybersecurity insiders have said that the government agencies are bringing forth tougher data protection requirements and disclosure of incidents, basically responding to the growing sophistication of the threats. The news analysis of the cybersecurity breaches shows the regulatory agencies are changing their approach to cybersecurity from considering it merely a voluntary organizational enhancement to regarding it as a basic infrastructure protection requirement. The recent news about the cyber attacks has indicated that this transition is a reflection of the growing acknowledgment of the cyber security's role in economic stability and national security. Cybersecurity insiders who analyze the regulatory developments report that there is a growing number of government agencies and private sector organizations working together to tackle the common cybersecurity issues. The news regarding the cyber attacks showcases that this joint effort marks a big step forward from the earlier regulatory approaches which m