Cephalus Ransomware Group Targets Organizations Through Unsecured RDP Access
A new ransomware operation known as Cephalus has emerged as a significant cybersecurity threat, targeting organizations across multiple industries by exploiting unsecured Remote Desktop Protocol access. Using sophisticated encryption and aggressive tactics, the group combines technical sophistication with psychological pressure to extract ransom payments from victims.

A new ransomware group that has been named Cephalus is a tremendous danger to the companies all around the world. Based on the information from cyber-security specialists, the group has been using stolen Remote Desktop Protocol (RDP) passwords to break into networks and then unleash strong encryption attacks that imprison firms and their essential data and systems.
The Threat Actors Who Executed the Attacks
The AhnLab research team has been following the Cephalus ransomware operation, which was first seen in the middle of June 2025. The Cephalus threat group is purely financially motivated and deliberately attacks businesses that do not have adequate security measures in place to secure their remote access infrastructure.
The group’s name comes from a character in Greek mythology who had an unerring spear, and this reference seems to indicate the threat actors' belief in their success rates. The choice of name implies a certain degree of complexity and structure within the criminal organization.
How Cephalus Works
The ransomware group, Cephalus, uses a simple but highly effective attack method that makes the most of a certain security weakness that many organizations have. They mainly target companies that operate RDP (Remote Desktop Protocol) services without multi-factor authentication (MFA) that is where they get into the system by illegally logging in with credentials.
After the cybercriminals access the victim's network through the RDP credentials they have stolen, they launch a particular attack sequence. The operation gets started by breaking into the systems and finding the data that is worth stealing. After gaining access, the criminals carry out data theft by the method of copying the sensitive data transferring the encryption payload to the victim's infrastructure.
One thing that stands out in Cephalus's operation is that they are very open to doing their ransomware deployment for the specific target. The level of customization would imply that the gang has operational sophistication and technical expertise at a very high level. Although it is not certain yet whether Cephalus is a Ransomware-as-a-Service (RaaS) platform or if they collaborate with other threat groups, their combined effort is a strong indicator of the kind of well-established processes and procedures that exist.
Technical Sophistication
The Cephalus ransomware virus shows a good deal of technical sophistication that is not limited to simply encrypting the victim's files and asking for ransom. Written in the Go language, this malware utilizes very advanced anti-forensics and evasion mechanisms which are intended to secure the submission of the encryption and at the same time keep the security tools in the dark.
The moment the ransomware runs on a target computer, it instantly takes measures that are defensive in nature to impede recovery and to obstruct security actions. It first of all turns off the real-time protection of Windows Defender, then deletes the volume shadow copies that could otherwise be used for data recovery, and lastly, it goes on to kill off important services such as the Veeam backup solutions and Microsoft SQL Server.
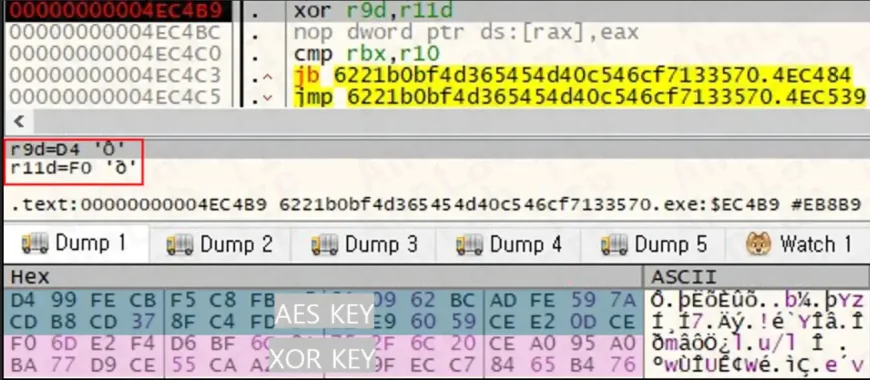
The combined approaches of cryptography form the encryption mechanism itself. Cephalus applies AES-CTR symmetric cryptography together with RSA public-key cryptography to ensure the security of the data stolen from the victims. One of the particularly ingenious aspects of the malware's design is the creation of false AES keys that are specifically aimed at misleading the dynamic analysis tools. This trick hides the true encryption process from both security researchers and endpoint protection systems, thus making it more difficult to analyze and eventual decryption.
Recommended Security Measure
Security experts propose such measures as implementing multi-factor authentication, strong credential hygiene, incident response teams, etc. The very first step is to apply multi-factor authentication (MFA) on every RDP access point since the absence of this security measure seems to be the main vulnerability that attackers like Cephalus rely on. Multiple security measures like this one should prevent or at least significantly slow down the unauthorized access process.
After introducing MFA, organizations should apply strong password management practices, and back up data regularly but store backups in locations separate from production networks. Security staff needs to ensure that they are capable of prevention and quick damage control measures for the endpoints, as well as monitoring and picking up the distinctive signals that would indicate that Cephalus is present.
Through the occurrence of Cephalus, it becomes clear that organizations need to put more emphasis on securing their remote access infrastructure as many companies still provide RDP services without strong protective measures just as Cephalus did simply by taking advantage of that flaw. Furthermore, with the spread of remote work in most sectors, the security of remote access protocols keeps being a challenging task that every organization has to face regardless of location.