Cl0p Ransomware Group Exploits Oracle E-Business Suite Zero-Day: Nearly 30 Victims Named in Extortion Campaign

A Worldwide Enterprise Security Crisis
In one of the most major cybersecurity events directed against enterprise infrastructure in 2025, the infamous Cl0p ransomware group has arranged a broad extortion campaign using serious flaws in Oracle's E-Business Suite (EBS). Almost 30 suspected victims have been publicly named on the Cl0p data leak site, representing a pivotal time for companies all around dependent on Oracle's corporate software for mission-critical business operations.
The raid marks a turning point in cybercriminal strategy. Rather than just deploying ransomware to encrypt data, threat actors have moved toward a more complex "double extortion" paradigm: stealing sensitive corporate information and threatening to openly release it unless victims pay sizable ransoms sometimes reaching millions of dollars.
The Vulnerability: CVE-2025-61882 and CVE-2025-61884
Two crucial flaws in Oracle E-Business Suite at the center of this campaign affect versions 12.2.3 through 12.2.14. The main vulnerability, tracked as CVE-2025-61882, was used as a zero-day vulnerability starting in early August 2025-weeks before Oracle issued emergency fixes. Shortly thereafter, CVE-2025-61884, another vulnerability, came into view, thereby worsening the security crisis.
Commonly known as XSLT injection, both vulnerabilities share a common root cause: risky handling of user-supplied XSL (Extensible Stylesheet Language) templates. The defects let remote attackers execute arbitrary Java code via these harmful templates without needing any authentication whatsoever. Direct exploitation of these vulnerabilities over HTTP without any credentials makes them very hazardous for companies using Oracle EBS systems on internet-available networks.
With a CVSS (Common Vulnerability Scoring System) rating of 9.8, CVE-2025-61882 points to a crucial level of severity requiring prompt action from all impacted businesses. CVE-2025-61884's CVSS score is 7.5.
Timeline: How the Campaign Unfolded
July 10 - August 9, 2025: The trail of suspicious dealings led back to July 2025, though the breach was detected and confirmed around August 9, 2025. Attackers utilized a high-level multi-stage Java implant framework to get into Oracle EBS environments. The criminals took over the unprotected systems and conducted the silent phase of data extraction by stealing sensitive business records which included payroll data, vendor contracts, internal configuration files, and financial ledgers.
September 29, 2025: Following secretly for weeks a data theft, the Cl0p group then moved to the extortion phase. The attackers initiated a large-scale email campaign from hundreds of hacked third-party email accounts, probably taken from infostealer malware logs sold on underground forums, which pumped out a substantial amount of email into the inboxes of company executives and important personnel and claimed that the actors had penetrated their Oracle EBS environments and had made off with the sensitive data.
October 2-4, 2025: Security researchers from Google Threat Intelligence Group (GTIG), Mandiant, and other threat intelligence companies started to publicly notify about the universal exploitation. Oracle issued a preliminary emergency patch on October 2, 2025, and on October 4, 2025, a more in-depth security advisory was released. Nonetheless, the emergency patch was found to be inadequate and a second critical update was requested, thus leaving organizations vulnerable during the gap period.
October 8, 2025: Oracle disclosed CVE-2025-61884 patch details and also offered supplemental guidance. By this point, Google analysts were of the opinion that the campaign had probably affected more than 100 organizations worldwide.
November 2025: The campaign kept on changing, with Cl0p, the ransomware group, naming almost 30 victims on the data theft site; this served not only as proof of the exploitation but also as a means of pressuring the victims to pay.
Attack Methodology: Surgical Precision
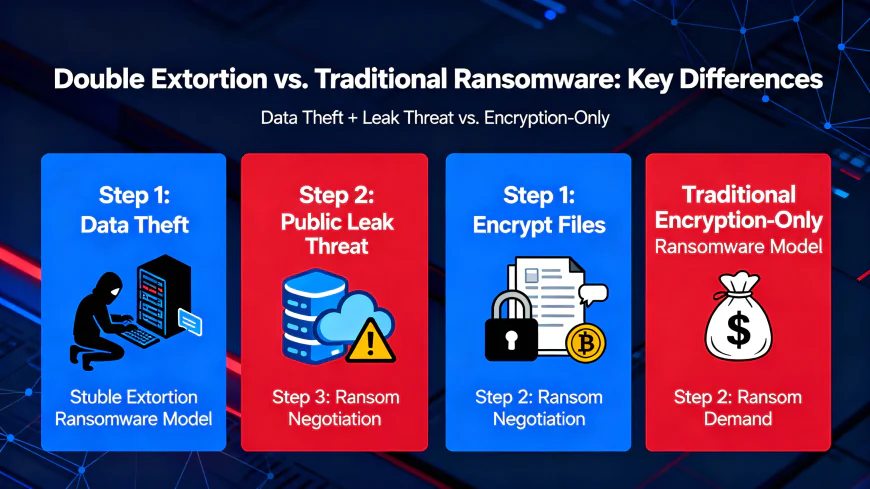
The Cl0p operation revealed an impressive sophistication in their tactics. After breaking into the victim's system via the use of zero-day vulnerabilities, the criminals resorted to a multi-phase technique:
Initial Compromise: Cybercriminals didn't sign in but rather waited for the right moment and scanned the internet until they found the Oracle EBS instances that had been running the outdated versions vulnerable to the attacks and were also exposed to the internet. The exploit chain would be set off automatically as soon as the system with a vulnerability was spotted.
Persistence and Lateral Movement: Becoming aware of the vectors through which initial compromises were made, attackers set up persistence mechanisms consisting of web shells, cron jobs, and unauthorized user accounts that allowed them to continue accessing the system for a long time even if the vectors were uncovered. They relied on the administrative accounts of the systems that had been compromised, particularly the "applmgr" account that is widely used in Oracle systems, to spread across the interconnected infrastructure.
Data Exfiltration: The attackers, after gaining access to the EBS environment, methodically exfiltrated enormous amounts of sensitive data over several months, and were extracting the information that would be the most valuable for the purpose of extortion.
Extortion: In the last phase, the criminals dispatched extortion emails to the top management along with the proof of successful exploitation, which included screenshots from the compromised EBS environments, directory listings, and samples of files. The emails contained addresses for contact through which ransom negotiation could take place, but the initial demands were purposely vague and were usually only specified after the victims indicated their willingness to negotiate.
High-Profile Victims and Impact
The campaign has so far included a list of major organizations that suffered attacks and among them the victims that were confirmed are: Harvard University, Envoy Air, DXC Technology, Chicago Public Schools, and last but not least, The Washington Post. The fact that The Washington Post, which is a prominent news organization with great cybersecurity resources, is on the list of victims, is a clear indication that the campaign has penetrated deep into various sectors.
In the beginning of November 2025 the Washington Post confirmed its participation in the Oracle EBS breach along with other Fortune 500 companies and critical infrastructure organizations on the Cl0p leak site.
According to Google's threat intelligence evaluation, the campaign most probably influenced more than 100 firms over the entire world, but only 30 of them have been publicly named on the Cl0p leak site so far. This means that a lot of the victims might not even know about their compromise or are dealing with the attackers behind closed doors.
The Strategic Shift in Ransomware Operations

The Oracle EBS endeavor is an emblem of the drastic change in the tactics of the ransomware group. In place of concentrating solely on encryption-based extortion, the Cl0p group has transitioned to data theft and publication threats - one of the models used is the dual-extortion or when legal threats are involved, it is referred to as "triple extortion".
This tactics change is indicative of a more profound comprehension of the victim's economics. An organization can retrieve its encrypted data from backup, but trade secrets, customer data, and proprietary information that have been stolen can never be "un-stolen". The theft gives the victim a leverage that is hard to overcome - they have an extremely strong negotiating position.
The previous campaigns of Cl0p targeting managed file transfer (MFT) systems like Accellion FTA, GoAnywhere MFT, MOVEit MFT, and Cleo LexiCom observed the same tactics of zero-day exploitation followed by massive data theft and extortion. The Oracle EBS campaign is a clear signal that this operational model has become highly lucrative and efficient, thereby entrenching it as the group’s standard practice in the future.
Organizational and Government Reaction
Oracle's Action: The supplier put out emergency patches on October 2 and 4, 2025, and a further patch for CVE-2025-61884 on October 11, 2025. Only however, the process of multi-stage patching left companies unprotected during the time between the patches.
CISA and Government Bodies: The U.S. federal agencies were ordered to close the security gaps of their systems by November 10, 2025. CISA confirmed that CVE-2025-61882 and CVE-2025-61884 were exploited by criminals and they issued them as known exploited vulnerabilities.
Security Sector: Threat intelligence firms significantly Google Threat Intelligence Group, Mandiant, SonicWall, and CrowdStrike released thorough threat advisories to alert organizations about the active exploitation and provided indicators of compromise.
Defensive Measures and Mitigation
The companies that use Oracle EBS systems have the following priorities:
Emergency Patching: Rush to apply the critical patches that Oracle has issued such as the October 2 and October 11 patches and henceforth install the rest of them.
Network Segregation: Only allow access over the internet to the Oracle EBS instances that are on the trusted networks. The hackers can carry out the attacks without any authentication and rely on the HTTP protocol.
Indicators of Compromise Monitoring: Set up threat detection rules that would alert you of XSLT injection attempts, spawning of the Java process, and copying of unusual data from the EBS systems.
Data Leak Monitoring: Organizations should track the Cl0p data leak forum and use threat intelligence services to get a better understanding of their status with regard to being a victim.
Incident Response Preparation: Organizations not certain of a compromise should regard themselves as potentially exposed and ready to carry out the incident response steps such as forensic preservation and notifying the police.
Broader Implications for Enterprise Security
This Oracle EBS campaign shines a spotlight on the major weaknesses in business security measures. The easy access to the internet of the mission-critical business systems, improper patching cycles that lasted a long time, and lack of proper network segmentation together made the conditions ripe for a big underground market to be created for the sale of stolen data.
The incident is a security threat that affects thousands of companies using Oracle EBS to handle enterprise resource planning, supply chain management, customer relationship management, and finance. In addition, it is a wake-up call in terms of digital infrastructure fragility that might reach far into the future.
The scenario in which the threat actors displaying advanced operational capabilities in the form of targeting enterprise software will force the companies to make drastic changes in their security approaches: the ones being rapid patch deployment, network isolation of critical systems, and continuous threat monitoring to detect and respond to sophisticated adversaries operating within the company infrastructure.











































