5 signs you’ve been hacked–Here’s how to fight back!
Five red flags mean you’ve been hacked: ransomware pop-ups, fake antivirus warnings, mysterious friend requests, password lockouts, and finding strange software on your system. Stay safe by running backups, verifying unexpected messages, enabling multi-factor authentication, cleaning out unknown software, and acting quickly if your accounts are compromised.

What is hacking?
Hacking is obtaining unauthorized access to computers, networks, or digital systems by exploiting vulnerabilities in security, typically with the intent to steal, change, or destroy data. While hacking is usually viewed as illegal or malicious behavior (i.e. stealing information, destroying services, etc.), it can also represent ethical or authorized testing to enhance security.
Here are 5 signs you’ve been hacked and what to do in that event.
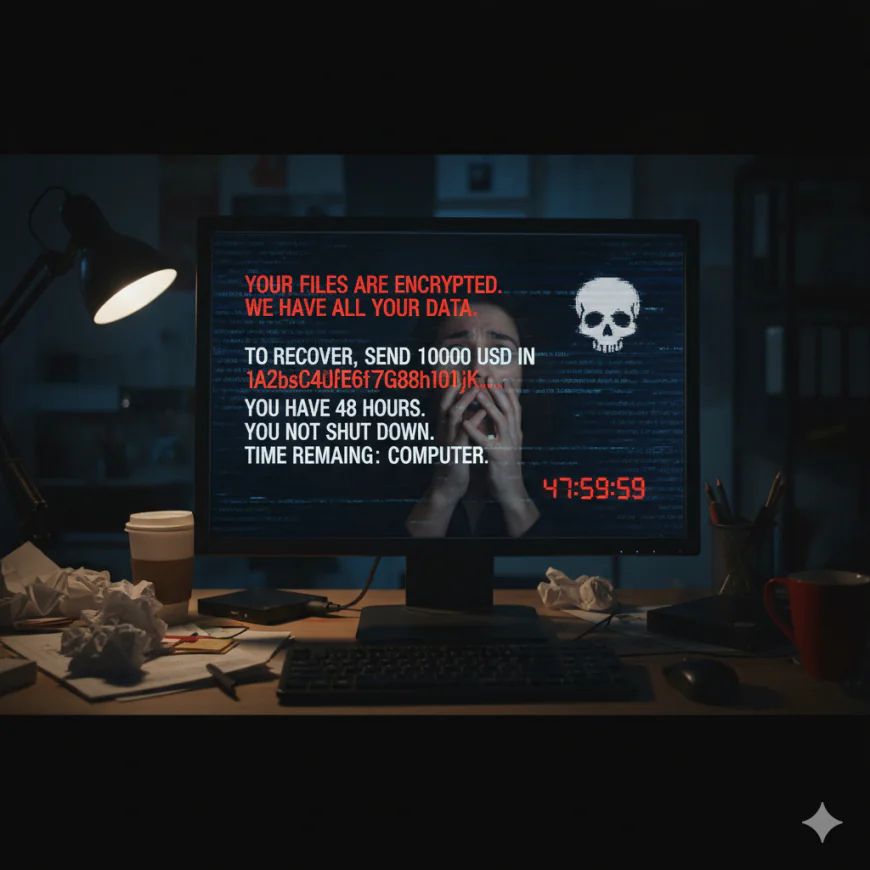
1. You get a ransomware message
One of the most alarming messages that a computer user can see is a malicious screen blocking access to a system that says all files are encrypted and payment is needed to unlock the files. Ransomware is rampant! After a slight decline of ransomware in 2017, ransom software has returned to give the impression it might be here to stay. Productivity losses are in the billions and ransom paid is in the billions. Small sites, large sites, hospitals, police and cities are all being crippled by ransomware. Almost 50% of victims pay the ransom resulting in a belief it is not going away.
Unfortunately, paying the ransom to cyber insurance companies, who are generally involved in the payment process, indicates that the system may remain unworkable 40% of the time. Ransomware programs are not perfect and encrypting linked systems is not as easy as populating a decryption key. Even if the ransom is paid, most victims lose multiple days of work and many additional recovery steps.
What to do: First, if you have a recently tested backup of the affected systems, you simply restore the affected systems and verify (officially called unit testing) that the restoration is 100%. Unfortunately, most organizations do not have the great backups they thought they had. Test your backups! Don't let ransomware be the first time your organization's critical backups are being assessed.
The best defense is to have good, reliable, tested, offline backups. Ransomware is becoming more sophisticated. The criminals using the malware are spending time in the compromised enterprise environment figuring how to do the most damage, including encrypting or corrupting your recent online backups. You are taking a risk every second you do not have good, tested, backups that are inaccessible to malicious intruders.
If you are a user of a cloud storage service for files, it likely retains backup copies of your data. Do not be over confident. Not all cloud storage services can recover from ransomware attacks and some services do not address all file types. You may want to reach out to the cloud-based file service that you use and express your concerns. Sometimes tech support can recover your files, and more of them, than you can yourself.
Lastly, several websites may be able to help you recover your files without paying the ransom. Either they’ve figured out the shared secret encryption key or some other way to reverse-engineer the ransomware. You will need to identify the ransomware program and version you are facing. An updated antimalware program might identify the culprit, although often all you have to go on is the ransomware extortion message, but that is often enough. Search on that name and version and see what you find.
2. You receive a fake antivirus warning
You will see a pop-up message on your computer or mobile device that it is infected. The pop-up message imitates an antivirus scanning product and claims to have detected a dozen or more pieces of malware on your computer. This isn’t nearly as common as it used to be, but fake antivirus warning messages are still a scenario that can pose a risk if not handled properly.
You can experience these for one of two reasons: Your system has been compromised in some way or it is just affected by the pop-up message. Hopefully, it is the latter. These types of fake antivirus messages have typically figured out a way to lock up your browser so that you can’t get out of just the fake message without killing the browser and restarting it.
What to do: If you have luck on your side, the fake AV message disappears when you close the tab and restart the browser. The fake message does not re-appear. It was a one time occurrence. Most of the time you will just have to kill the browser. Restarting the browser sometimes loads the same original page that introduced the fake ad to you, so you see the fake AV ad again. If this happens, restart your browser in incognito or in private mode, and you can browse to a different page and stop the fake AV message from loading.
The worst case scenario is that the fake AV message actually compromised your computer (probably through social engineering or unpatched software). If this is true, you are going to have to power down your computer. If you need to save anything and can do it, do it before you power down the computer. Then restore your system to a previous clean image. Most operating systems have reset features built especially for this.
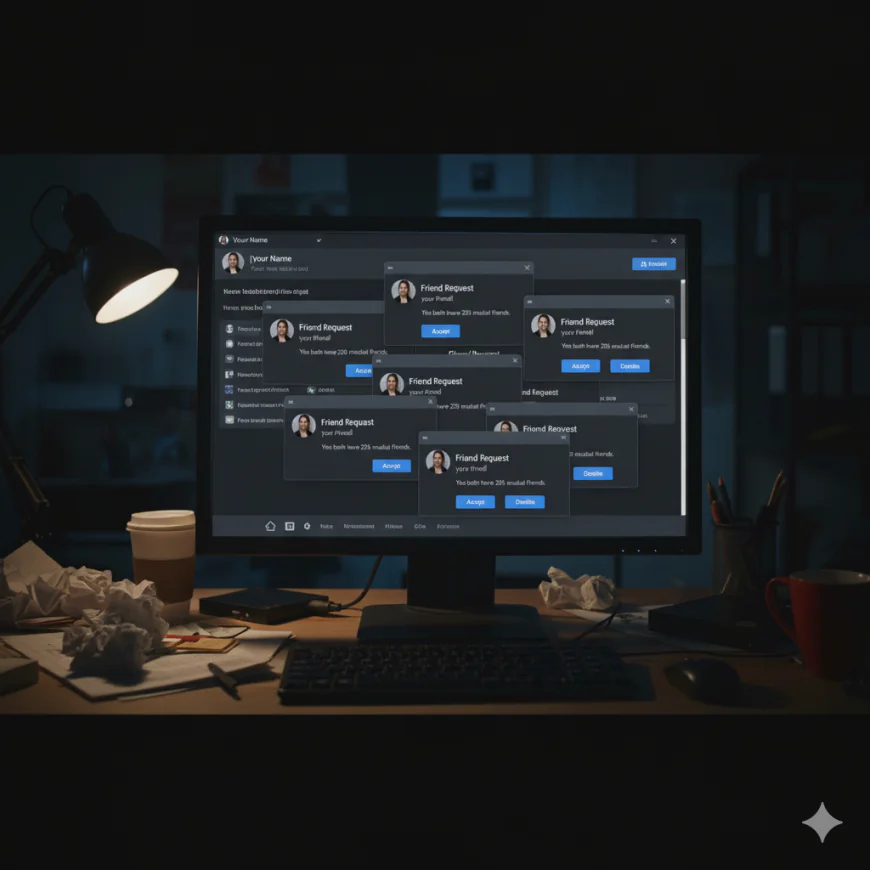
3. Your friends are receiving social media invitations from you that you did not send
We've all had this happen to us as well. Either you or your friends are receiving invitations to "be a friend," while you are already connected with friends on that social media platform. You are wondering, "Why did they invite me again? Did they unfriend me, and I just did not realize it, and now they are inviting me again." You then look at the new friend's social media site and see that that account has little or fewer recognizable friends and no older posts. Or that friend is contacting you, wondering why you are sending them friend requests. In either case, you, the hacker, has control of your social media site, created a second almost-identical bogus page, or you or the friend has downloaded a rogue social media application.
Here’s what to do: First, warn your other friends not to accept the surprise friend request. You may say something like, “Don’t accept that new request from Bridget. I think she’s hacked!” Then, contact Bridget in another way to verify. Spread the information through whatever common social media streams you have. Then, if you didn't already, contact the social media site and report the site or friend request as bogus. Each site has its own process for reporting bogus friend requests. Check their online help, you’ll usually find something like “report a bogus friend request” which will tell you how. Sometimes it is as simple as clicking a report button. If the social media site really was hacked (and not just a second bogus look alike page), then you will need to change your password (check your help information on changing your password if you do not know how).
Better yet, do not waste your time! Change to a Multi-factor authentication (MFA) system. That way the bad guys (and rogue apps) can’t steal it as easily and take over your social media presence. Last, but not least, be leery about installing any social media app. Most of them are malicious in the first place. Periodically check to see what applications you have installed under the applications page of your social media account/page, and delete all unless you actually want to keep them.
4. You're unable to log in with your online password
If you are sure that you are entering your online password correctly, and it’s still not working, you may be hacked! I normally try again in 10 to 30 minutes because I have experienced sites having technical issues and not accepting a valid password for a short period of time. Once you are sure you can no longer use your current password, a hacker probably came online using your password and changed it to lock you out.
Usually it is as simple as the victim responding to an authentic-looking phishing email claiming to be from the service. The bad guy uses the victim to collect the logon information, comes online and changes the password and other information to make it harder for the victim to recover, then uses the service to take money from the victim or acquaintances of the victim (while pretending to be the victim).
What to do: If multiple acquaintances were contacted, contact all of your close contacts immediately to avoid escalation of your compromised account. This action will limit the damage done to others by your error. Additionally, contact the online service to report the compromised account. Most online services now have effective reporting methods through easy routes or an email contact address; due to the high volume of compromised accounts recently, if you report your account as compromised, most times, they will take the necessary steps to help restore your legitimate account access. You may also want to consider enacting MFA.
If the compromised logon information is used on other websites, change the passwords associated with those accounts immediately. Next, be more vigilant in the future. Most websites do not send emails asking for you to provide your logon information. Instead, if in doubt, go on the internet to get direct access to the website (don’t click on the link provided in the email) to see if they are requesting the same. You can also consider calling the service on their telephone line or emailing them to report the phish email received or for verification.
5. You see software you didn't expect to be installed
Another major indicator is unwanted or unexpected software installs. In the early malware days, the majority of the programs were computer viruses, which replicated by modifying other known and legitimate programs to disguise themselves better. Apparently, nowadays, most malware programs are Trojans and worms. Trojan and worm programs typically install themselves in the same way as legitimate programs, and this may be because their authors are trying to walk a fine line when the legal system catches up to them. They can say something like, “But we are a legitimate software vendor.”
The unwanted software is often installed legally by other programs or software you installed, so take the time to read your license agreements. I can't tell you how many times I've read agreement disclosures that explicitly state that they will be installing one or more additional programs. In some cases, you can opt out of these other installs; however, in most instances, the additional programs or software do not allow you to opt out.
What to do: Many programs will show you all the programs you have installed and let you selectively disable running programs. My favorite checkers for Microsoft Windows are Microsoft’s free programs, Autoruns and Process Explorer. They don’t show you every single program installed but they will tell you the ones that automatically start when your PC is restarted (Autoruns) or the ones currently running (Process Explorer).
Most malware programs will be found embedded in the much larger list of valid running programs. The difficult part can be determining what is valid and what is not valid. You can enable the “Check VirusTotal.com” options and the programs together with Google’s Virustotal.com web site will tell you which ones it thinks are malware. When in doubt, simply disable the unrecognized program, reboot PC, and only re-enable the program if some necessary functionality is not working after the reboot.












































