Inside the Dark Web: Your Ultimate Guide to the Hidden Side
The dark web is the internet’s secret hideout that isn’t visible on regular search engines. It requires special software like the Tor browser to access and keeps users anonymous. While it's known for illegal activities, it also helps protect privacy and free speech, especially for people in dangerous situations.

What Is the Dark Web?
The dark web which is also commonly known as the darknet or the black web is one of the most mysterious and misunderstood sides of the internet. It is a small part of the deep web. The restricted part of the internet that cannot be indexed by standard search engines like Google or Bing is the dark web. It is intentionally hidden and inaccessible through normal browsers or search engines which is unlike the surface web that everyone uses through the traditional browser. The dark web is infamous for its illicit activities and also known for its legitimate activities. More than 2,700 live dark websites were classified by researchers Daniel Moore and Thomas Rid and discovered that 57% contained illegal content. It requires special software, like Tor browser, to access the dark web.
Is the Dark Web Real?
Yes, the dark web is absolutely real. It’s not just a concept from dramas or books but exists as a network of websites requiring specific tools and configurations to access. While much of the dark web is associated with illicit activities, not everything there is illegal. The dark web provides a platform for journalists, and individuals in oppressive countries to communicate safely. It is also well used for academics and niche content which is otherwise unavailable.
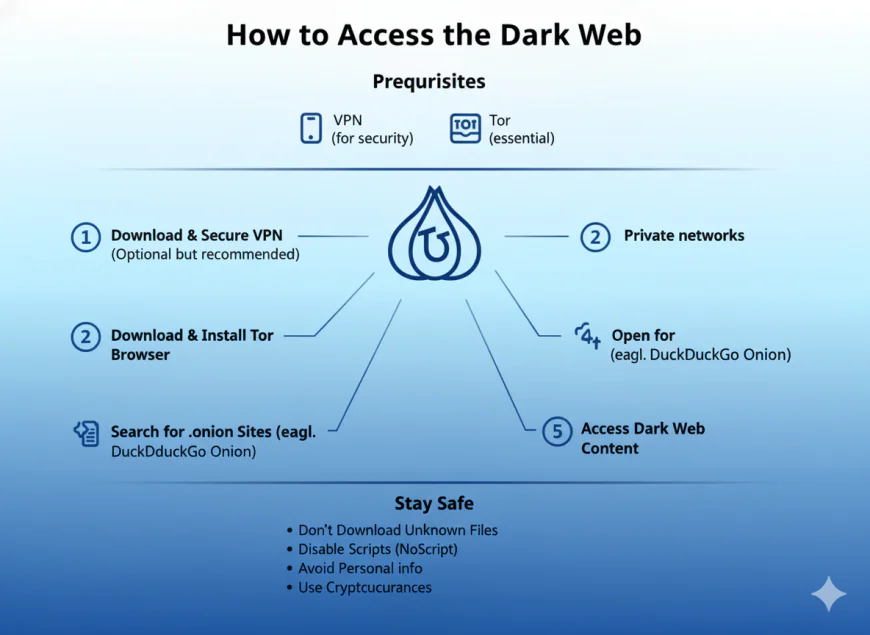
How to Access the Dark Web
The dark web requires a special software, it typically requires the users to download the Tor browser. It allows people to connect to dark web sites ending in the .onion domain. .Onion domain offers anonymity by routing the connection through several encrypted nodes, making user activity virtually untraceable. Navigation is challenging inside the dark web, though many dark web links are unreliable or short-lived, search engines such as Grams or directories like The Hidden Wiki help users find what they’re looking for.
The Tor network operates through three security levels:
-
Standard: All features enabled, including JavaScript and multimedia
-
Safer: Disables potentially dangerous features like JavaScript on non-HTTPS sites
-
Safest: Only basic website functionality enabled, with JavaScript disabled globally
What Can You Find on the Dark Web?
There is a mix of legal and illegal activities on the dark web. One can find stolen credit card details, hacked social media accounts, counterfeit currencies, and illegal drugs on the dark web. We can say that the dark web is also a hub for cybercriminals offering hacking services and tools like malware or ransomware kits. However, there’s also a lawful side to the dark web, privacy advocates, journalists, and activists use the dark web for secure communication. You can even find dark web social networks, book clubs, and digital privacy resources.
What Is the Dark Web Used For?
The dark web is used for many activities including for illicit and legitimate purposes. It is like an infamous marketplace for illegal goods such as drugs, weapons, data, hacked accounts etc. The dark web is often misused by cybercriminals as they buy or sell stolen credentials, spread malware and ransomware kits and also offer hacking services. There are also very dangerous activities happening over the dark web like money laundering, human trafficking and trading due to the anonymity the dark web provides there is privacy for everyone.
Despite some illicit activities there are also some legal uses of the dark web. It serves as a shelter for journalists, activists, and whistleblowers seeking to communicate securely and avoid censorship or surveillance, particularly in authoritarian regions. There are many government organizations, tech companies, and media that use the dark web for encrypted information exchange. The dark web is monitored by researchers and law agencies for information gathering, tracking criminal behaviour and also for collecting forensic evidence for digital crime.
Security experts, such as Patrick Tiquet of Keeper Security, use the dark web for threat analysis and monitoring. The dark web acts as an intelligence source that reveals information about stolen data, emerging cyber threats, and underground hacking trends. Many cybersecurity professionals scan the dark web for compromised credentials or confidential enterprise data to assess the scope of cyberattacks.
Overall, we can say while the dark web is widely associated with criminal activity, it is also a vital resource for privacy, secure communications, and intelligence work, with applications spanning government, media, cybersecurity, and civil society.
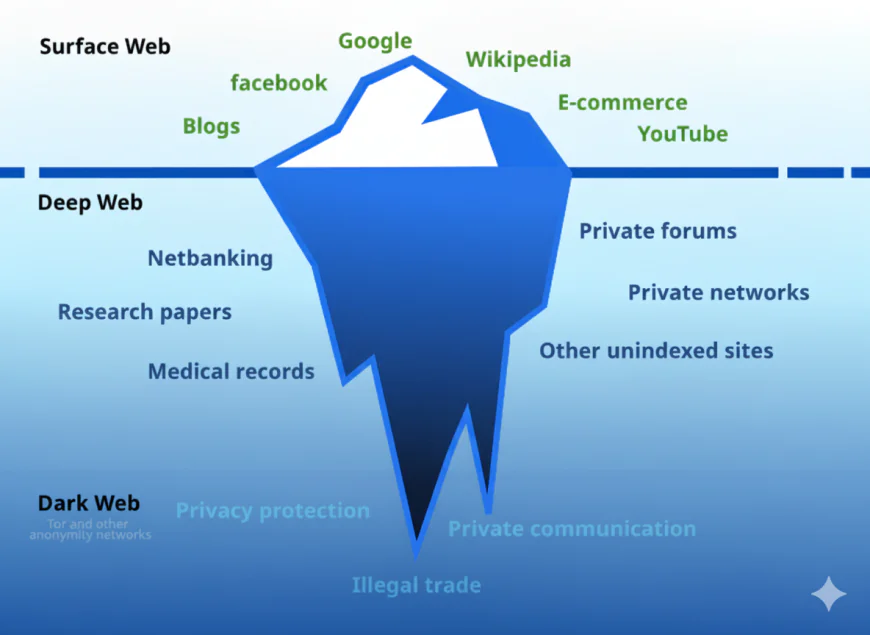
Defining the Dark Web and Its Place in Internet Architecture
There are three distinct layers where the internet exists, each with different accessibility and purposes. Understanding these layers is fundamental to grasping the dark web's significance and impact.
The Three Layers of the Internet
Surface Web: Also known as the clear web represents only 4-5% of the total internet. It includes all publicly accessible websites that are indexed by search engines like Google, Bing, and Yahoo. Through normal web browsing these sites can be easily found and they represent the internet that most users interact with daily. Surface Web contains popular platforms like Facebook, Wikipedia, and news etc.
Deep Web: Under Surface Web is the Deep Web, representing approximately 90-95% of the internet. All content not indexed by search engines is surrounded by the deep web. This includes password-protected sites, private databases, academic journals behind paywalls, medical records, personal email inboxes, and corporate intranets. To access the deep web content proper credentials, direct URLs, or institutional access are typically required.
Dark Web: A small part of the deep web is the dark web, it is assessed by a special software like Tor and it represents only about 5% of the total internet. It's intentionally hidden and designed for anonymous communication and transactions, utilizing encrypted overlay networks that prioritize user anonymity.
Tools and Services Available on the Dark Web
On the dark web, there are well over a dozen categories of dangerous tools and services: malware, DDoS attacks, compromised credentials, espionage tools, and phishing kits. The dark web even has ransomware-as-a-service (RaaS) businesses that allow criminals to extort money from victims. The ransomware groups REvil and GandCrab, sell their ransomware on the dark web and it is available to criminals who attack victims while splitting profits. IBM research indicated the profits for REvil on the dark web were over 80M for one year.
A Dark Web Browser
Anonymity is paramount for everything done on the dark web. The dark web operates largely through the Tor network - traffic away from your IP address is encrypted, and while the Tor system looks like a standard browser, it is relatively a slow user experience due to this encryption design. Using a dark web browser is much messier than browsing the "normal" internet, and scammers have hijacked the dark web for hacking and other digital opportunism.
Dark Web Search Engines
Searching for information on the dark web is a far cry from using Google and involves a different set of skills. For instance, dark web search engines such as Grams and indexes (sometimes called directories or catalogs) such as The Hidden Wiki will attempt to categorize dark web sites, but something often goes wrong. Some links simply lead to dead links (or links that time out), while others lead to blank pages or pages that aren't worth reading. It also serves as a reminder that the dark web is an unstable environment.
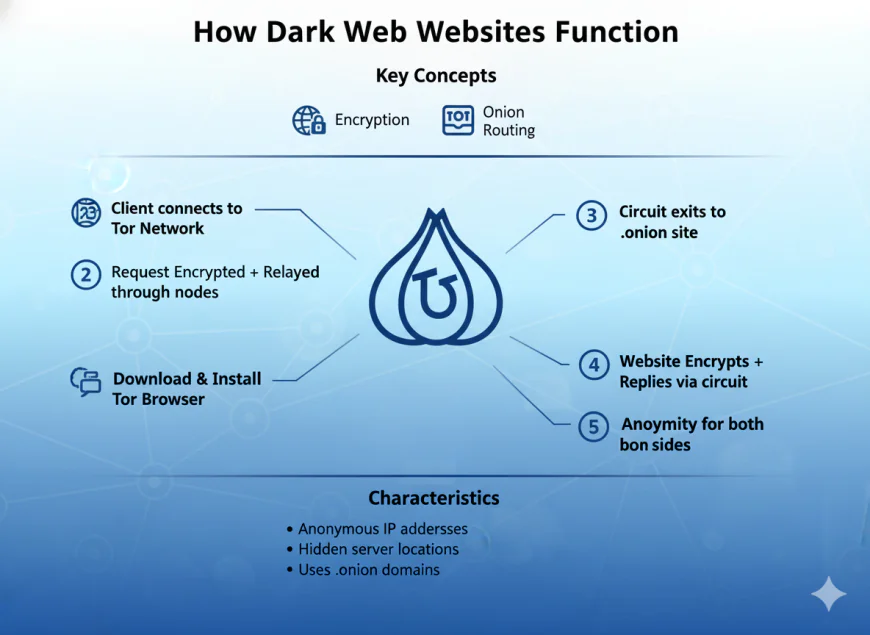
How Dark Web Websites Function
Dark web websites are made up of .onion domains with confusing names that are hard to remember and only accessible through Tor. .onion is a way to create an additional layer of protection for site visitors and creators. The dark web appears to mirror regular e-commerce sites with product listings, product reviews, communication, and some verification for transactions, but scams abound. Many dark web markets can shut down overnight, and buyers can find themselves stuck with their cryptocurrency gone.
How Bitcoin is Used on the Dark Web
The dark web and Bitcoin emerged together to enable anonymous transactions between buyers and sellers. Most dark web marketplaces only trade in cryptocurrency for the sake of anonymity, including Bitcoin and Monero, but those same factors led law enforcement to crackdown on illicit operations, arrests, and shut down places like AlphaBay.
Is the Dark Web Illegal?
Not everything on the dark web is illegal, despite its reputation. The dark web is an important haven for individuals who value privacy, journalists, and dissidents in oppressive regimes where free expression is limited. Websites like SecureDrop, as well as dark web access to Facebook and Wikileaks, help provide a forum for communication, activism, and whistleblowing. Numerous reputable organizations, including government agencies monitor the dark web for leaked information and emerging threats.
Why Is the Dark Web Important?
Understanding the dark web is helpful for your own cybersecurity understanding, as the dark web illustrates the hidden infrastructure of world cybercrime knowledge, but it also provides insight into digital privacy, and even digital freedom. Monitoring the dark web for all types of security incidents has become, and will increasingly become, a fundamental component of any modern cybersecurity strategy - from protecting sensitive data to complicated ransomware.
In the end, the dark web is a double-edged sword; it’s a breeding ground for cyber threats, as well as an important tool for anonymity and digital rights. Whether through curiosity or security purposes, you can be sure the dark web stands as one of the most complex, secretive and interesting world of the internet.











































