Experts Reports Sharp Increase in Automated Botnet Attacks Targeting PHP Servers and IoT Devices
The automatic botnet attacks are not only becoming larger but also more complex. Their primary targets are PHP servers and IoT devices all over the globe, and they do this by taking advantage of the already existing weaknesses such as CVE-2017-9841 (PHPUnit), CVE-2021-3129 (Laravel), CVE-2022-47945 (ThinkPHP) and also by misconfiguring clouds. The intention of the criminals is to use the robots that perform their duties automatically to quickly and easily find and take over the less protected systems, and in most cases, they are operating through the cloud to avoid detection and at the same time, steal the important credentials. The use of these botnets is not limited to the DDoS attacks but they have also taken on the roles of credential theft, phishing, and even AI-driven web scraping, thus making the risks to companies, smart homes, and cloud infrastructures greater than ever. The experts are calling for rapid patching, correct configuration, and advanced anomaly detection as the main strategies to combat these threats effectively.

Unprecedented automated botnet attacks are reported to be hitting PHP servers and IoT devices across the globe, due to the publication of several cybersecurity reports this week. According to experts, the artillery's scale and technological savvy have already redesigned the threat landscape, thus putting more risk on the organizations and consumers than ever.
Automated Botnet Attacks Hit PHP and IoT Ecosystems
On October 30, 2025, significant threat intelligence teams together with the Qualys Threat Research Unit, reported a considerable increase in botnet activities. The malware primarily targeted widely used PHP web servers but also the devices connected to the internet, like routers and digital video recorders. Groups like Mirai, Gafgyt, and Mozi that are recognized as major opponents are taking advantage of the recent disclosure of CVE vulnerabilities and the lack of proper security configurations that are common in cloud infrastructure and smart device networks.
What’s Driving the Spike?
Several factors are said by analysts to be the root cause of the attacks:
Exploiting Known Vulnerabilities: The attackers, leveraging RCE flaws, have gone after several vulnerabilities that have already been reported. Among those are CVE-2017-9841 (PHPUnit), CVE-2021-3129 (Laravel), and CVE-2022-47945 (ThinkPHP). The process involves scanning for unprotected systems, usually with the help of automating tools, and then executing commands through the vulnerabilities to take over the system.
Cloud Misconfiguration and Hygiene Problems: Not only misconfiguration and poor hygiene in the cloud but also weak security settings in the case of PHP-based content management systems such as WordPress and Craft CMS and the use of default passwords on IoT devices grant attackers easy access.
Debugging Tools Keep Active: Attackers can find out server activities and even get hold of sensitive information like cloud passwords if they are allowed to use debugging tools such as Xdebug in production.
James Maude, field CTO at BeyondTrust, says, “The history of router hack and botnets is a repeating one. Weak passwords and unpatched software have remained the points of entry for hackers regardless of the warnings given over the last decade.”
How Are the Attacks Happening?
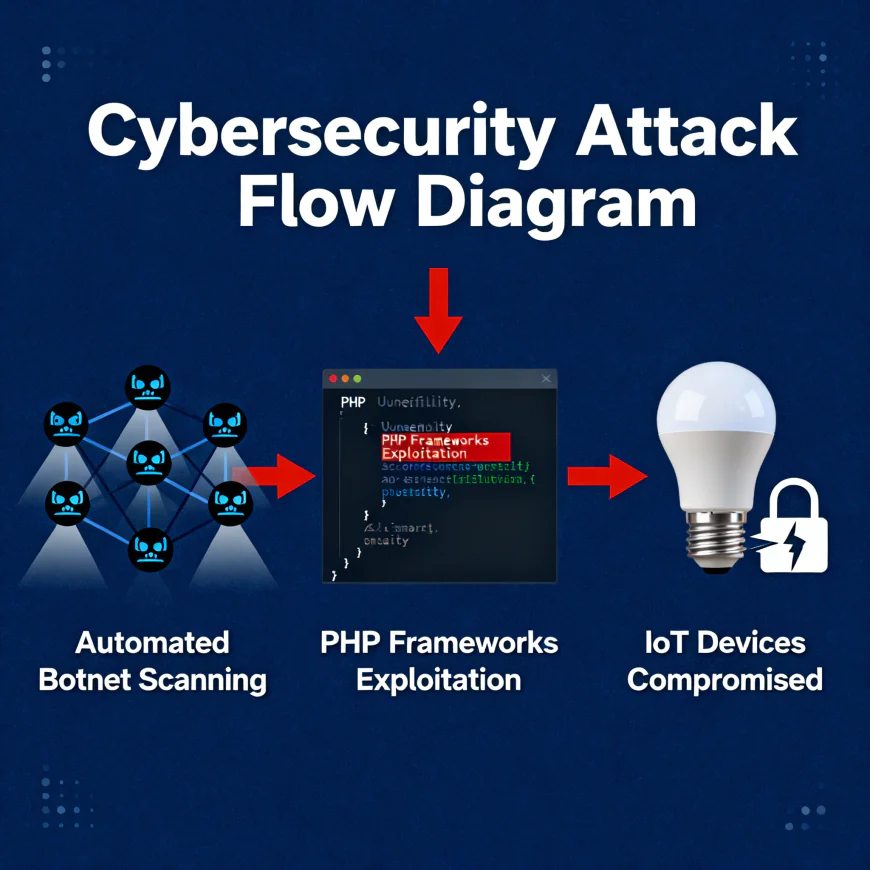
The Qualys Threat Research Unit along with various security teams have indicated that these campaigns are heavily reliant on automation for their entire process of going through the internet to spot weak systems, and doing it quick enough for those systems to be taken over by the botnet:
PHP Framework Exploitation: The criminals are persistently utilizing RCE (Remote Code Execution) weaknesses in the affected frameworks, e.g., PHPUnit (CVE-2017-9841), Laravel (CVE-2021-3129), ThinkPHP (CVE-2022-47945), and the aforementioned Spring Cloud Gateway (CVE-2022-22947) and TBK DVR devices (CVE-2024-3721) misconfigurations. Through this, they are capable of injecting commands and controlling the systems entirely without much hassle.
Debugging Tools Exploitation: One other significant approach is where attackers prepare HTTP requests specifically to the Xdebug features that are still enabled in production servers and exploit them. In case they are not properly turned off, then they can be used to extract the delicate application data or even make the exploitation deeper.
IoT Devices Targeting: IoT devices such as broadband routers, DVRs, and surveillance cameras often running the obsolete firmware are still very easy targets. The intruders take advantage of vulnerabilities (such as the command injection in TBK DVRs and MVPower DVR backdoors) or default passwords to keep on abducting millions of devices for new botnets regularly.
What Makes Today’s Attacks More Dangerous?
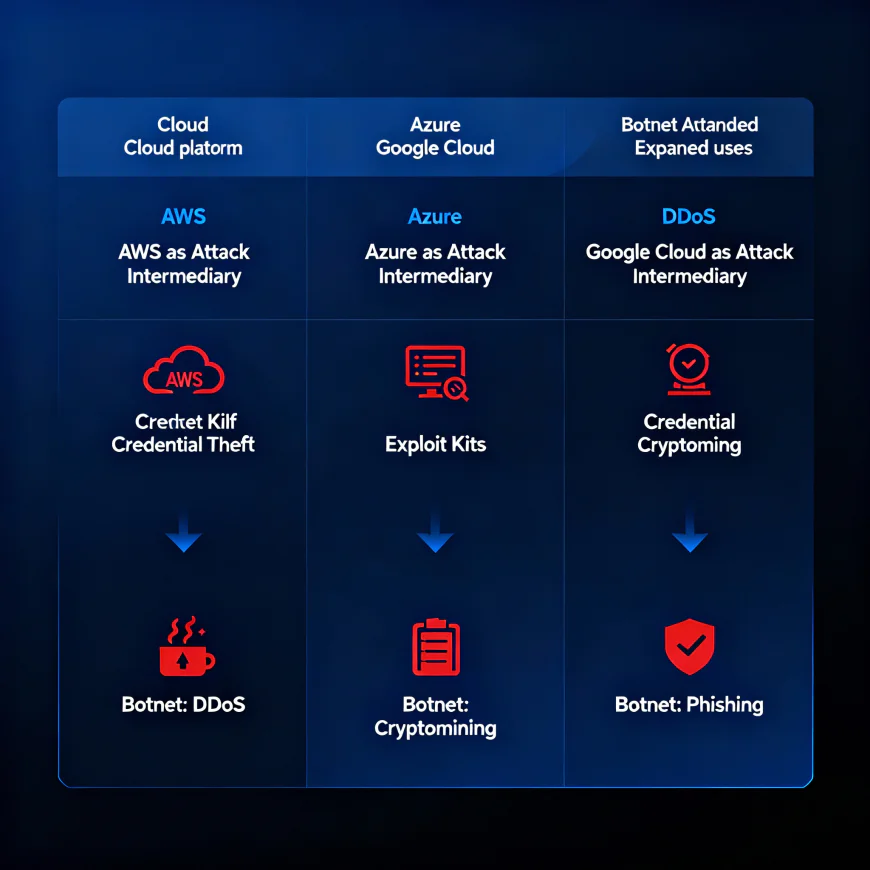
Cloud Abuse: Attackers are utilizing major cloud platforms (AWS, Google Cloud, Microsoft Azure) as intermediaries for their attack traffic in order to hide the origins and make it more difficult to identify the sources. As a result, this scenario has made traditional detection less effective and has also raised the level of difficulty in responding to incidents.
Credential Theft at Scale: The accessed servers and IoT devices are commonly found to be contain sensitive information such as AWS credentials, API keys, and user tokens. Oxygen for the actors lurking around for such credentials is granted through their escalation to the highest privilege, being persistent, and sneaking their way through the networks.
Availability of Attack Kits: Robust exploit kits and thorough botnet frameworks are abundantly available and unchallenging to operate. Thus, it virtually becomes impossible to prevent the emergence of “entry-level” criminals that can cause enormous harm with just the assembled tools. Expanded Uses: Botnets have outgrown their original usage as mere accomplices to DDoS attacks. DDoS attacks are now only one of the many things botnets can do:
credential stuffing, phishing, spamming, web scraping using AI, and cryptomining, to name a few. Moreover, they are acting as residential proxies for paid customers, which is a development that is increasing their commercial and criminal appeal.
Impact: Statistics and Risks

Attack Frequency: PHP is the backbone of more than 73% of the web, and the figure of 82% of organizations that reported cloud misconfiguration incidents in the past year is indicative of the unprecedented attack surface.
IoT at the Forefront: In its joint 2025 report, Bitdefender and Netgear reveal that 13.6 billion IoT attacks have occurred in just the first ten months.
DDoS Escalation: AISURU (TurboMirai) is now capable of launching DDoS attacks that exceed a staggering 20 terabits per second. The goal of such attacks includes to major consumer ISPs, government portals, and online streaming services.
European Risk: Germany, France, the UK, Italy, and Spain are the most affected countries, as they face heavy financial and reputational impacts due to the occurrence of downtime, non-compliance with regulations (like GDPR), and data leakage.
Who Is at Risk?
Web-Based Businesses: Outdated or poorly configured PHP web applications are the main attraction for hackers.
Smart Homes and Enterprise Networks: Hackers keep trying to break into networks with vulnerable IoT devices-such as home routers and business DVRs-even if these attacks are unsuccessful.
Cloud Infrastructure: In the case of AWS, Azure, or any other cloud service, companies are highly vulnerable if their security credentials are compromised or improper public settings are used.
Expert Recommendations
Scott Schneider from iCOUNTER speaks out the significance of risk-based vulnerability management (RBVM) in directing action towards the highest danger via the same channel.
Security leaders are pushing for urgent measures:
Applying the patches for flaws in all frameworks, plugins, and CMS deployments should be the first thing to do. Live environments should not have debugging tools like Xdebug or if they are there, then they should be configured properly. Regular audits of the cloud should be conducted in order to identify misconfigurations and then lock them down. IoT devices should be isolated on separate subnetworks or VLANs in order to contain potential breaches. Adoption of cutting-edge anomaly detection techniques, AI systems included, should be done in order to detect and trace unusual traffic, especially from cloud service providers. Managed secret stores (e.g., AWS Secrets Manager, HashiCorp Vault) in combination with multifactor authentication should be employed to reinforce credentials. Teams should be trained on new botnet tactics and such scenarios should be incorporated in incident response plans.
Outlook
Professionals in the field are voicing worries that with the increasing availability and user-friendliness of exploit kits and botnet frameworks eventually even untrained hackers will be able to cause huge damage. The incidents that occurred this week corroborate the argument of the necessity for powerful and proactive security measures not only in the internet and the connected gadgets but also the potential of even bigger attacks should the organizations neglect this point. The engagement of cyber security experts worldwide in the monitoring of the changes in botnets close to real-time is supported by the incoming new threat reports, thus revealing that the race for cyber weapons is still on.