How to Secure Docker Containers: Best Practices for 2025
In 2025, securing Docker containers is no longer optional—it’s survival. With supply chain attacks, misconfigured images, and leaked secrets driving over 60% of cloud-native breaches, DevOps teams must rethink how they build, ship, and run containers. This blog breaks down the real-world risks, shares hands-on best practices like using distro-less images, non-root containers, runtime monitoring with Falco, and secret management with Vault, and gives engineers a step-by-step security checklist they can apply immediately. Whether you’re deploying on AWS, Azure, or Kubernetes, these practices will help you stop attackers before they compromise your workloads.

Introduction
Containers have become the backbone of modern application deployment, offering speed, scalability, and efficiency. Docker, in particular, has simplified how developers build and ship applications. But with this convenience comes a critical challenge: **security**. Unlike traditional VMs, containers share the host OS kernel, which means a single vulnerability can potentially impact multiple containers and even the host system. This makes securing Docker containers not just a good practice but a necessity in 2025, where cyber threats are more advanced than ever.
In this blog, we’ll explore the best practices to secure Docker containers in 2025, ensuring your applications remain resilient, compliant, and safe from evolving attack vectors.
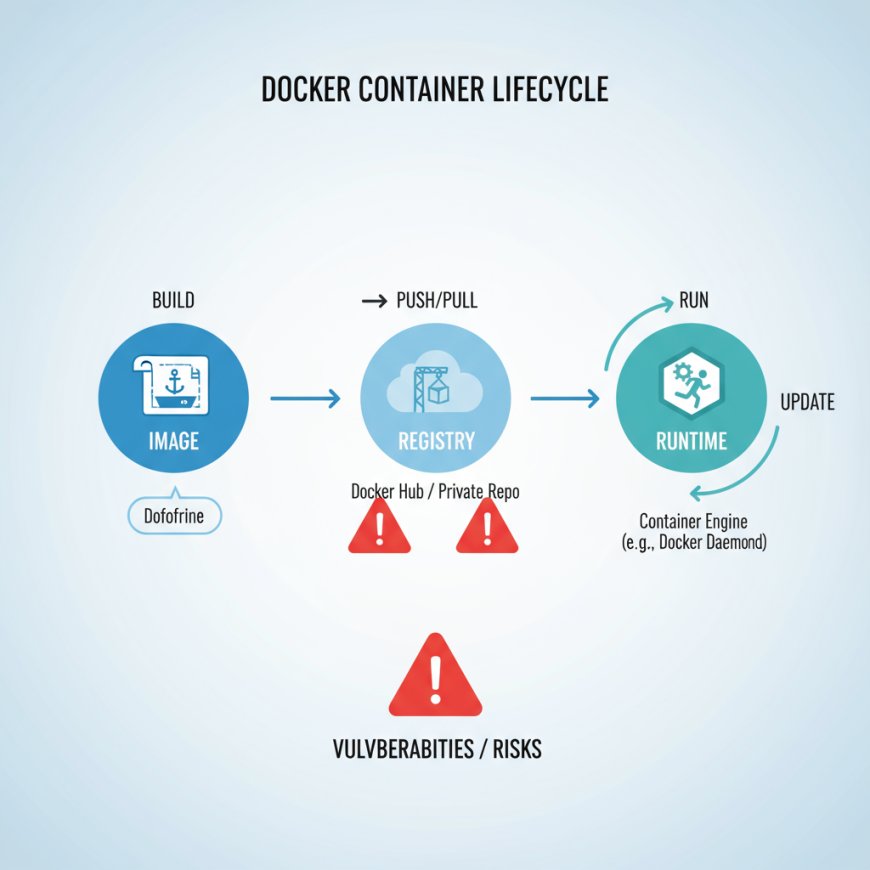
1. Common Security Risks in Docker Containers
Before securing containers, it's important to understand the attack surface:
· Unpatched Images: Old base images with CVEs get exploited.
· Over-Privileged Containers: Running as root allows full system takeover.
· Leaked Secrets: API keys & DB passwords often end up in .env files.
· Unrestricted Networking: Containers can freely talk to each other — lateral movement for attackers.
· Supply Chain Risks: Pulling malicious or compromised images from Docker Hub.
2. Best Practices for Securing Docker Containers in 2025
Use Trusted Base Images:
Always start with official or minimal base images (e.g., alpine:3.19) instead of random ones from unverified sources.
Scan Images Regularly:
Integrate tools like Trivy in CI/CD pipelines to detect vulnerabilities early.
Example: trivy image myapp:latest
Apply Least Privilege:
Avoid running containers as root. Use USER in Dockerfile and drop unnecessary Linux capabilities.
Keep Docker Host Updated:
Regularly update Docker, host OS, and container images. Use automation like Watchtower for container updates.
Isolate Workloads:
Run services on custom Docker networks to prevent unnecessary exposure.
Secure Secrets:
Never hardcode credentials in images. Use Vault, AWS Secrets Manager, or Kubernetes Secrets.
Enable Resource Limits:
Set CPU and memory limits in docker-compose.yml or Kubernetes to prevent abuse.
Use Read-Only Filesystems:
Run containers with read-only permissions to stop attackers from tampering inside.
Runtime Security Monitoring:
Install runtime monitoring tools like Falco, Aqua, or Sysdig Secure. Detect crypto mining, suspicious syscalls, or privilege escalation.

Adopt DevSecOps Practices:
Embed security scanning, policy checks, and automated compliance in CI/CD workflows.
3. Future of Docker Security in 2025
AI-Powered Vulnerability Scanning: Security tools will increasingly use AI/ML to auto-detect zero-day vulnerabilities in container images and block unsafe deployments before they reach production.
Shift-Left Security by Default: Security checks will move even earlier in the pipeline. Developers won’t just write code --- their IDEs will auto-scan Dockerfiles and dependencies for risks in real time.
Policy as Code Adoption: Tools like Open Policy Agent (OPA) and Kyverno will become standard, enforcing security rules (e.g., no privileged containers) directly in CI/CD pipelines.
Confidential Containers: With growing focus on data privacy, containers will adopt hardware-based encryption like Intel SGX/AMD SEV to protect sensitive workloads at runtime.
More Fine-Grained Access Control: Expect Docker and orchestrators like Kubernetes to strengthen RBAC (Role-Based Access Control), so teams can strictly limit who can run, manage, or modify containers.
Stronger Image Provenance: By 2025, image signing and verification (e.g., Sigstore, Cosign, Notary v2) will be a must to ensure containers are built from trusted sources only.
Automated Threat Detection: Runtime protection tools (Falco, Aqua, Sysdig) will integrate deeper with Docker, automatically detecting anomalies like crypto mining or container escapes.
Conclusion
Securing Docker containers isn't about one tool or one best practice—it's about embedding security throughout the lifecycle: build, ship, run. In 2025, DevSecOps engineers who follow these principles will not only prevent breaches but also meet compliance requirements like PCI DSS, ISO 27001, and NIS2.
Action item for engineers:
Start today by scanning your images with Trivy, enabling non-root users, and monitoring containers with Falco. Small steps now can prevent million-dollar breaches later.